Configure KSS Keystore
- Sign in to Oracle Enterprise Manager Fusion Middleware Control
12c:
The default Administration Server port number is 7001.http://administration_server_host:administration_server_port/em - Create a stripe and name it
owsm- In the content pane, select WebLogic Domain, then
Security, and then
Keystore.
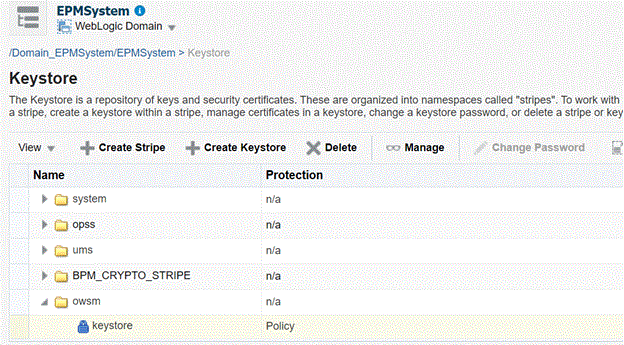
- Click Create Stripe.
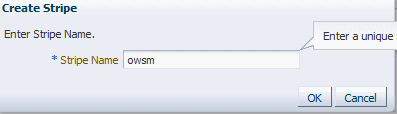
- Enter owsm and then, click OK.
- In the content pane, select WebLogic Domain, then
Security, and then
Keystore.
- Create a keystore named
keystorein theowsmstripe.- Select the
owsmstripe you created and click Create Keystore.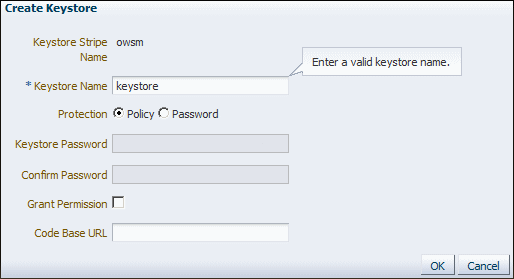
- Name this keystore
keystore. - Set the protection type to Policy. (Password protected KSS keystores are not supported in this release.)
- Clear the Grant Permission check box.
- Do not specify a code base URL.
- Click OK.
- Select the
- Select the keystore you just created and click Manage.
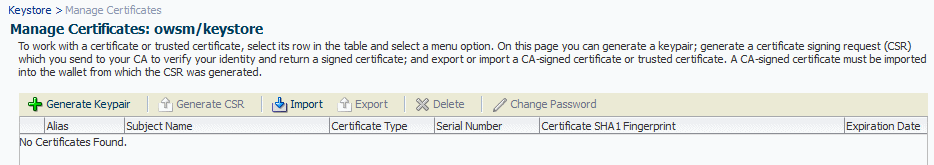
- Click Generate Keypair to generate a private/public
key pair.
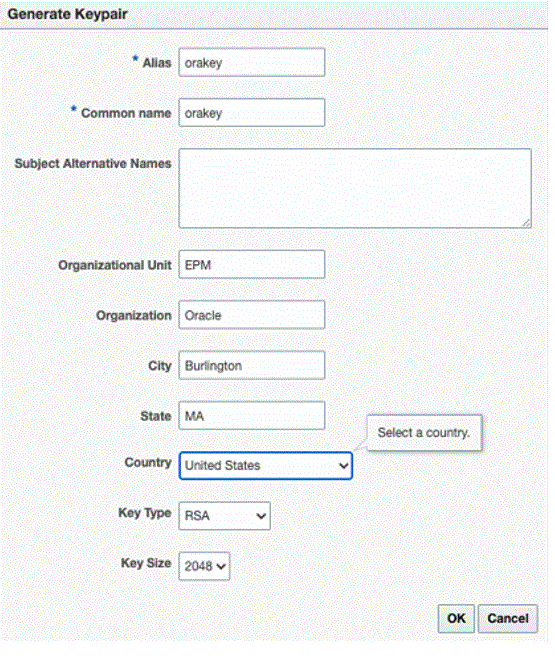
- Specify an alias such as
orakeyfor the key pair and enter the other information as appropriate. - Click OK.
- Click Generate Keypair to generate a private/public
key pair.
- On the Manage Ceritifcates page, select
orakeyand click Import to import the trusted certificate. The Import Certificate dialog appears: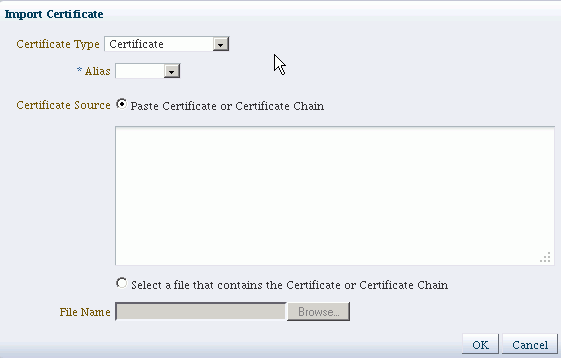
- Select the certificate type, either Certificate or Trusted Certificate, from the drop-down.
- Select the alias from the drop-down.
- Specify the certificate source. If using the Paste option, copy and paste the certificate directly into the text box. If using the File Name option, click Browse to select the file from the operating system.
-
Click OK. The imported certificate or trusted certificate appears in the list of certificates.
- In the content pane, navigate to WebLogic Domain, then
Web Services, then WSM Domain
Configuration. If you encounter any error, ensure that you have
started the SOA managed server (soa_Server1).
- Click Manage Security and enter the following details:
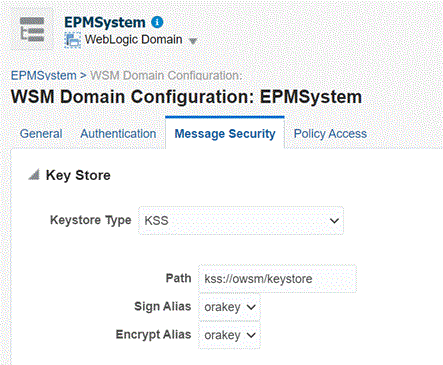
- Click Apply.
- Click Manage Security and enter the following details:
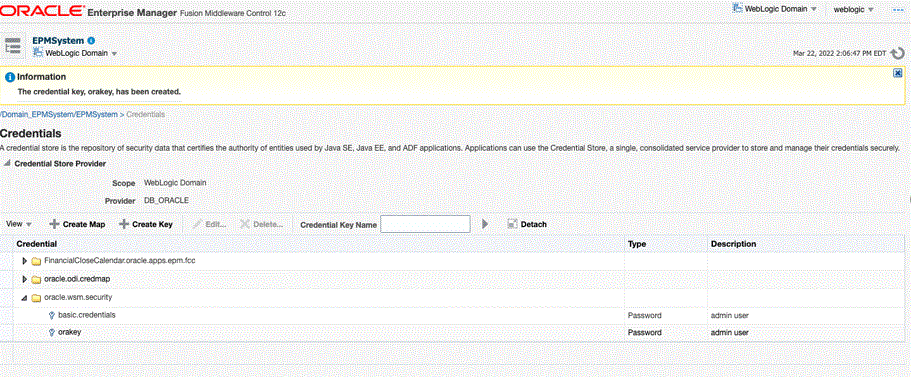
- Additionally ensure if credential store
oracle.wsm.securitymap is created by default or not. If the credential storeoracle.wsm.securitymap was not created, you must create it before you can use the credential store to store user credentials.- In the content pane, navigate to WebLogic Domain, then Security, then Credentials.
- Click Create Map.
- Specify the Map Name as
oracle.wsm.securityand then, click OK. - Click Create Key. Enter the information as
appropriate. For example:
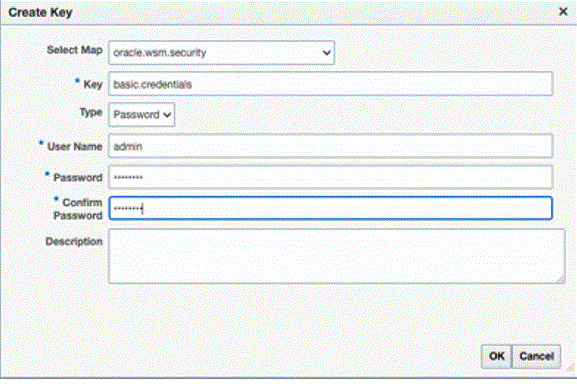
- Create another key and name it as
orakey. Click OK. - The following dialog appears:
- In the content pane, click Weblogic, and then click logout.
- Stop the servers:
- To stop the WebLogic Administration
Server:
MIDDLEWARE_HOME/user_projects/domains/domainName/stopWebLogic.cmd - To stop the SOA Managed
Server
MIDDLEWARE_HOME/user_projects/domains/domainName/stopWebLogic.cmd soa_server1
- To stop the WebLogic Administration
Server:
- After configuring the KSS Keystore, you must:
- Start WebLogic Admin Server and the SOA managed server.
- Run
DeployToSOA.cmdcommand. For example:<Local Drive>:\Oracle\Middleware\EPMSystem11R1\common\config\11.1.2.0>deployToSoa.cmd <Local Drive>:\Oracle\Middleware <Local Drive>:\Oracle\Middleware\user_projects\epmsystem1