Configuring the Deployment Server JDE.INI File (Release 9.2.5.1)
Starting with JD Edwards EnterpriseOne Tools Release 9.2.5.1, the Network and Queue Settings (JDENET Configuration) section of the deployment server JDE.INI file contains three settings for SSL or TLS support. These settings are used when the enterprise server connects to the deployment server during a package build from the web client. The deployment server passes the information to the enterprise server on the type of connection to be used. Older enterprise servers that do not support SSL or TLS cannot connect with a deployment server that is enabled with SSL or TLS because of this architecture. Therefore, SSL or TLS support for JDENET requires that the release level of the EnterpriseOne clients matches the release level of the EnterpriseOne servers.
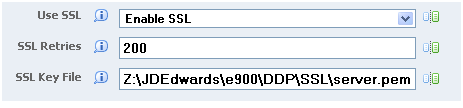
The SSL or TLS settings in the Network and Queue Settings (JDENET Configuration) section of jde.ini are:
useSSL
The valid values for this field are
Enable SSLorDisable SSL. If you enable this option, the JDENET messages will be exchanged using secure sockets (SSL or TLS). This setup is done only on the deployment server, but for the setup the enterprise servers accessing the deployment server must be able to process SSL or TLS messages (that is, all the enterprise servers must be running on the same EnterpriseOne ToolsRelease as the deployment server). Starting with EnterpriseOne Tools Release 9.2.5.1, Disable SSL is the default setting.sslRetries
This setting specifies the maximum number of times the server or client will attempt to complete an SSL or a TLS handshake. If the handshake is not completed within the retry limit, the SSL or TLS connection fails. The retry limit prevents the server from hanging on an SSL or a TLS connection that may never be established. The default value of 1,000 for this setting should be appropriate for most installations, but may need to be increased to allow for slow clients or high network latency.
sslKeyFile
You must set this parameter to the fully qualified path of the file containing the server's SSL/TLS certificate and private key. The server must have a valid certificate/key file in PEM format in order to use secure sockets. See Generating an SSL/TLS Certificate and Key File in this chapter for more information.
The following is an example of a typical SSL/TLS setup viewed from Server Manager: