JWT Internal Flow
For authentication with a JWT, the following must take place:
You must configure the private key certificate that is used for token generation on the AIS Server. It is initially configured with the Demo Certificate.
You must configure the public key certificate used for token validation on the HTML Server.
You must store the certificate in a secure PKCS 12 keystore (.p12) and upload it to the HTML Server.
You must configure the EnterpriseOne HTML Server as a trusted node through the single sign-on trust configuration.
The following image shows the internal authentication flow in an environment in which JWT is used for authentication.
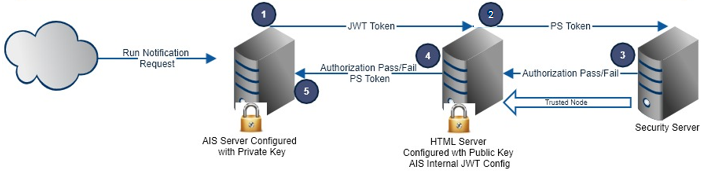
The following steps describe the internal authentication flow:
A JWT is generated for each subscriber (with the subscriber user ID) and is passed to the JTML Server to establish a session.
The JWT is validated against the public key, the token timeout is validated, and the principal (user) is extracted from the JWT payload. A PS Token is generated for that user and sent for authorization by the Security Server (EnterpriseOne Enterprise Server).
The Security Server checks the PS token with SSO node trust, and then an authorization response is returned to the EnterpriseOne HTML Server.
The authorization response is returned to the AIS Server. The PS Token is included in the response.
The AIS Server uses that subscriber's session to execute the defined notification and then logs out.