Process Flow for Standard EnterpriseOne Windows Client Sign-in Security
EnterpriseOne provides sign-in security with an architecture that is designed to provide user security for EnterpriseOne and the logically attached database management systems. The security architecture prevents you from viewing the database or system password and from bypassing EnterpriseOne applications to view and change data.
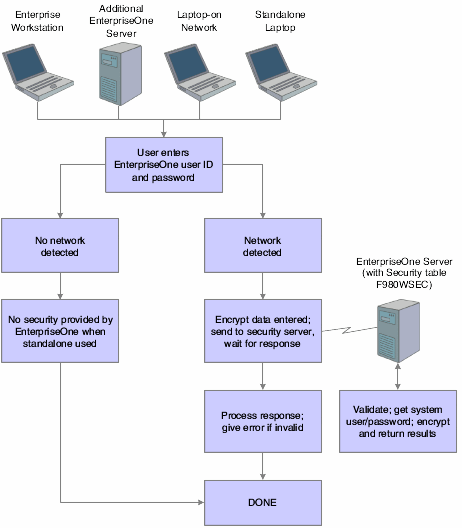
Standard sign-in security for EnterpriseOne Windows clients uses this process flow:
Users sign in to EnterpriseOne on their workstations using their user ID and password.
The workstations can be networked or standalone workstations, laptop computers, or other EnterpriseOne hosts.
If you enter a valid user ID and password, as validated against the local workstation installation, the start-up process continues.
As the software starts, it tries to detect an operational network environment.
If a network is not detected, the software allows local operation in a store-and-forward mode. Because the workstation or laptop computer is not connected to a network or an enterprise server, no validation can be performed against the F980WSEC table. Therefore, security is limited to that provided by the local workstation or laptop installation.
If a network is detected, the software encrypts the password information and sends it over the network to the JD Edwards EnterpriseOne enterprise server.
The enterprise server checks the incoming validation request against a table of valid users and passwords. If the user ID and password information are valid, the software accepts the sign-in values and returns the system ID and password to the logically attached database servers. This information is also encrypted on the enterprise server prior to broadcast on the network.
This graphic displays a process flow model for standard sign-in security:
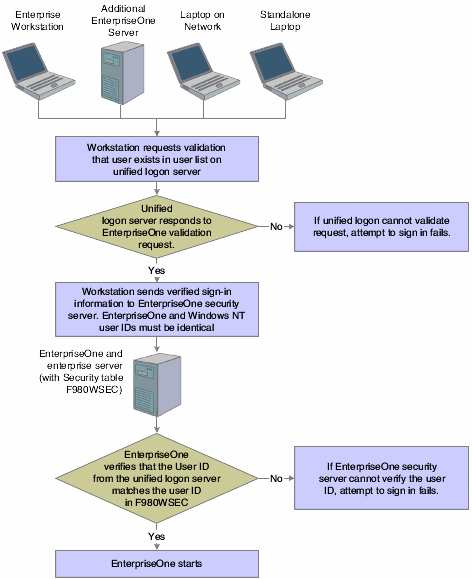
The process flow for sign-in security with a unified logon (prior to release 9.2.2 only) is as follows:
A user starts EnterpriseOne on a workstation.
EnterpriseOne verifies that the unified logon is active and then sends an authentication request to the unified logon server, based on the domain user ID.
Note:The unified logon server is not a physical server. It is a device that verifies sign-in security against the domain sign-in security maintained by Microsoft Windows.
During jdesnet initialization, jdesnet activates the unified logon server thread. The unified logon server ends automatically when jdesnet ends.
The unified logon server searches its user list for an entry that matches the domain user ID. When the server finds a match, the server sends a validation request to the enterprise server.
The Enterprise Server verifies that the response from the unified logon server matches the security information in the F980WSEC table.
If the security information from the user list on the unified logon server matches the security information in the F98OWSEC table on the enterprise server, the start-up process continues.
The first time that a user signs in to EnterpriseOne with the unified logon, the Environment Selection appears.
The user must enter an environment in the Environment field. Select the option to set the environment as the default, and avoid the Environment Selection form on subsequent sign-in attempts.
This illustration displays the process flow for unified logon: