Single Sign-On Architecture
Single sign-on with OAM requires an EnterpriseOne HTML Server configuration with an application server, such as Oracle WebLogic Server 10g, that contains a J2EE container, which is required for the Java servlets and Java code to run. In addition, WebGate must be installed on an Oracle HTTP Server, and it must be configured to protect the EnterpriseOne URLs that are used to access the HTML Server.
This illustration shows the integration environment and process flow:
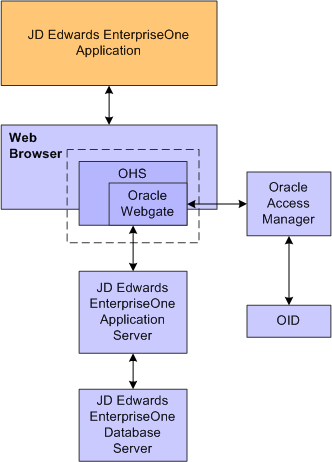
The following steps describe the single sign-on process:
A user attempts to access an EnterpriseOne program by entering a URL to the EnterpriseOne web client in a web browser.
A WebGate deployed on the EnterpriseOne HTTP Server intercepts the request.
The WebGate checks OAM to determine whether the resource (EnterpriseOne URL) is protected.
If a valid session does not exist and the resource is protected, WebGate prompts the user for credentials through the OAM login page.
After the user enters the single sign-on user ID and password on the OAM login page, the WebGate captures the user credentials and sends them to OAM for authentication.
OAM compares the user credentials against the Oracle Internet Directory (OID).
If the user's single sign-on credentials are not in OID, OAM notifies WebGate and the user is denied access to EnterpriseOne.
If OAM finds the user's single sign-on credentials in OID, OAM authenticates the credentials.
If the credentials are validated, the user gains access to the EnterpriseOne web client.
If a valid session already exists and the user is authorized to access the resource, WebGate redirects the user to the requested EnterpriseOne resource.