How It Works
When a new orchestration is saved in the Orchestrator Studio, the name of orchestration is used to define an endpoint on the AIS Server. The endpoint URL is:
http://<server>:<port>/jderest/orchestrator/<orchestrationname>
To invoke an orchestration, calling applications or devices use a post operation to this
URL, where <orchestrationname> is the name of your orchestration.
The post operation must include security parameters that enable access to the
orchestration and any EnterpriseOne application invoked by the orchestration. See Orchestration Security Considerations for more information.
The following illustration shows how the EnterpriseOne Orchestrator processes orchestrations. The illustration depicts processing an orchestration designed to receive data from external devices in an IoT configuration, but you can also use orchestrations to consume and provide data to Cloud services, third-party applications, custom EnterpriseOne programs, and more.
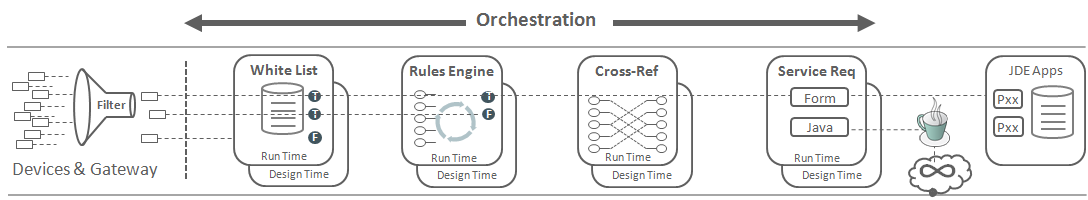
Third-party devices and a gateway collect and process information from one or more devices, converts the information to a platform-independent format and communicates this information over the internet. The gateway typically deploys intelligence to filter sensor data, secure data transfer, automate software updating, run diagnostics, start or stop the device, and support other features.
The Orchestrator uses the following orchestration components, created in the Orchestrator Studio, to transform incoming raw data into data that can be used by EnterpriseOne:
Orchestration. The master process that defines the inputs for the orchestration and provides a unique name for the orchestration process in the Orchestrator. An orchestration uses the next four components in this list to run a single orchestration instance.
Service request. An invocation of a JD Edwards EnterpriseOne interactive application or a Java application via a REST service call to the EnterpriseOne Application Interface Services (AIS) Server.
Rule. Contains a set of conditions against which the orchestration input is evaluated to produce a true or false state. Rules can be nested to produce complex evaluations. Rules determine how the orchestration is processed at runtime. You can also use custom Java to define additional rules.
Cross reference. A set of data relationships defined by the designer of the orchestration that enriches the minimal input from devices. For example, a device's serial number can be cross-referenced to a JD Edwards EnterpriseOne Equipment Number for use in service requests.
White list. An initial rudimentary pass/fail check of the incoming message's device signature against a predefined list of signatures. A white list provides an additional layer of security to the Orchestrator security.
You can also use custom Java to create custom client applications (that run on the AIS Server) for viewing and working with the filtered data. You can create a custom Java application to perform a specific business process or a process for storing the data in another database outside of EnterpriseOne.