Configuring OAuth 2.0 Resource Servers with OAM 11g
You can use an OAuth 2.0 resource server to handle the authentication requests from AIS clients. This type of authentication allows access to AIS services, as well as orchestrations created using the Orchestration Studio. In this authentication process, an OAuth token is requested from an authentication provider and then passed to the AIS token request (stateful) or AIS service directly (stateless). If the AIS token request (stateful) is used, the AIS token is used for subsequent AIS calls.
To use OAuth 2.0, the format of the OAuth 2.0 token must be JWT and you must configure the steps required for JWT configuration.
See "Configuring EnterpriseOne HTML Server for JSON Web Token (JWT) (Release 9.2.3.2)" or "Configuring EnterpriseOne HTML Server for JSON Web Token (JWT) (Release 9.2.0.5)" in the JD Edwards EnterpriseOne Tools Security Administration Guide.
This graphic shows OAuth 2.0 authentication flow for stateful scenario.
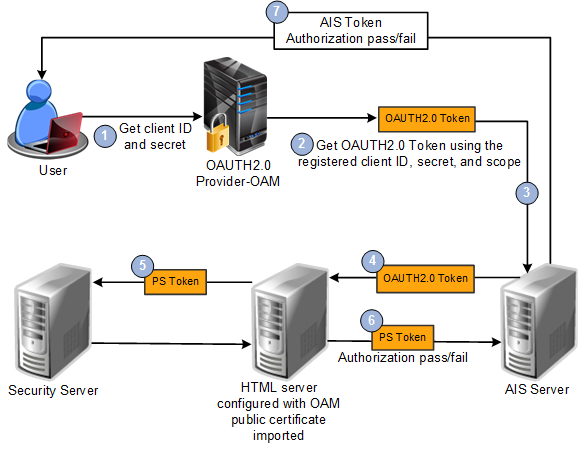
The following steps describe the configuration and authentication flow:
Create an OAuth 2.0 resource server.
See Creating an OAuth 2.0 Resource Server for more information.
See Creating an OAuth 2.0 Client for more information.
Get an OAuth 2.0 token using the registered client ID, secret, domain, and scope.
The following is an example of the parameters that you would provide to generate an OAuth 2.0 token. In this example, the value passed for Authorization parameter 'SkRFOnBsNEhBYzg5' is a base64 encoded value of client ID and secret that is separated by a colon.
curl -i -H 'Authorization: Basic <SkRFOnBsNEhBYzg5'> -H "Content-Type: application/x-www-form-urlencoded;charset=UTF-8" -H "X-OAUTH-IDENTITY-DOMAIN-MAME:<JDEIdentityDomain>" --request POST http://mycompany.com:14100/oauth2/rest/token -d 'grant_type=client_credentials&scope=<JDEResourceServer>'.
Parameter
Value
Description
Authorization Header
Basic <base34_clientid_secret>
This parameter contains base64 encoded values of the client ID and client secret separated by colon. The parameter is used as access token by the client.
Client ID
<client_id>
This parameter is the unique API key that is generated when you register your application with OAM.
Client Secret
<client_secret>
This parameter is the private key that is generated when you register your application with OAM.
Access Token URL
ms_oauth/oauth2/endpoints/oauthservice/tokens
This parameter is an endpoint that is used to obtain an access token from OAM.
Grant Type
client_credentials
This parameter indicates that the REST API to be invoked is owned by the client application.
Scope
JDEResourceServer
This parameter returns all the grants provided to your application.
Domain
JDEIdentityDomain
This parameter is the Identity Domain name under which all clients and resource servers are created.
An OAuth 2.0 token is generated with the client ID, secret, and scope and sent in the Bearer header of an AIS token request. (Stateless requests are also supported.)
The AIS Server forwards the OAuth 2.0 token to the EnterpriseOne HTML Server and is configured to allow a JWT. The AIS Server forwards the OAuth 2.0 token in the Bearer if login is required.
The Security Server checks the PS Token with node trust, and returns an authorization response to the EnterpriseOne HTML Server. You must import the OAM certificate into the HTML Server to validate OAuth 2.0 token locally in the HTML Server. For more information, see "Adding an Existing Certificate to a New Keystore" in the JD Edwards EnterpriseOne Tools Security Administration Guide.
The EnterpriseOne HTML Server returns the authorization response to the AIS Server. The PS Token is included in the response.
The AIS Server returns the authorization response to the AIS client (third-party). If passed, for a token request the response includes an AIS token.
In stateless scenario, if passed, the actual resources are provided to the user.