- OIG Integration Quick Start
- OIG Integration Quick Start
- Set Up Oracle Identity Governance Integration
Set Up Oracle Identity Governance Integration
To enable the Oracle Identity Governance agent to connect to Oracle Access Governance, you need to enter connection details and credentials for the target system, and build an agent specific to your environment.
- In a browser, navigate to the Oracle Access Governance service home page and log in as a user with the Administrator application role.
- On the Oracle Access Governance service home page, click on the
 icon and select Service Administration and then
Orchestrated Systems.
icon and select Service Administration and then
Orchestrated Systems. - Select the Add an orchestrated system button, to navigate to the Add an orchestrated system page to start the workflow.
- On the Select system step of the workflow, you can specify which type of
system you would like to onboard. You can search for the required system by name
using the Search field.
- Select Oracle Identity Governance
- Select Next
- On the Enter Details step, enter the general details for
the orchestrated system:
- Enter a name for the system you want to connect to in the What do you want to call this application? field.
- Enter a description for the system in the How do you want to describe this application? field.
- Click Next.
- On the Add owners step:You can associate resource ownership by adding primary and additional owners. This drives self-service as these owners can then manage (read, update or delete) the resources that they own. By default, the resource creator is designated as the resource owner. You can assign one primary owner and up to 20 additional owners for the resources.To add owners:
Note:
When setting up the first Orchestrated System for your service instance, you can assign owners only after you enable the identities from the Manage Identities section.- Select an Oracle Access Governance active user as the primary owner in the Who is the primary owner? field.
- Select one or more additional owners in the Who else owns it? list. You can add up to 20 additional owners for the resource.
- On the Integration settings step of the workflow, enter
the configuration details required to allow Oracle Access Governance to connect to the required Oracle Identity Governance instance.
- In the What is the JDBC URL of your OIG database
server? field, enter the JDBC URL for the OIG database you want
to connect with.
Note:
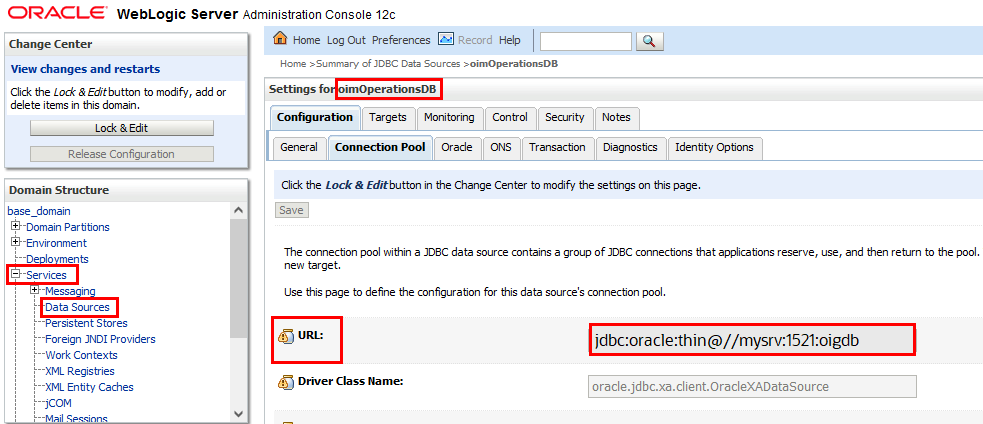
To obtain the JDBC URL:- Log on to the Oracle WebLogic Server Administration Console associated with your Oracle Identity Governance instance.
- Navigate to Services → Data Sources.
- Select oimOperationsDB from the Configurations tab.
- Select Connections Pool, and copy the value from the URL: field to use as the JDBC URL for Oracle Identity Governance.
- In the What is the OIG database user name? field,
enter the database user to connect to the OIG database.
Note:
This can be any user with read access to the OIG database. - In the Password field, enter the password for the OIG database user you have specified.
- In the What is the URL of your OIG server? field,
enter the URL of the OIG server you want to integrate with.
Note:
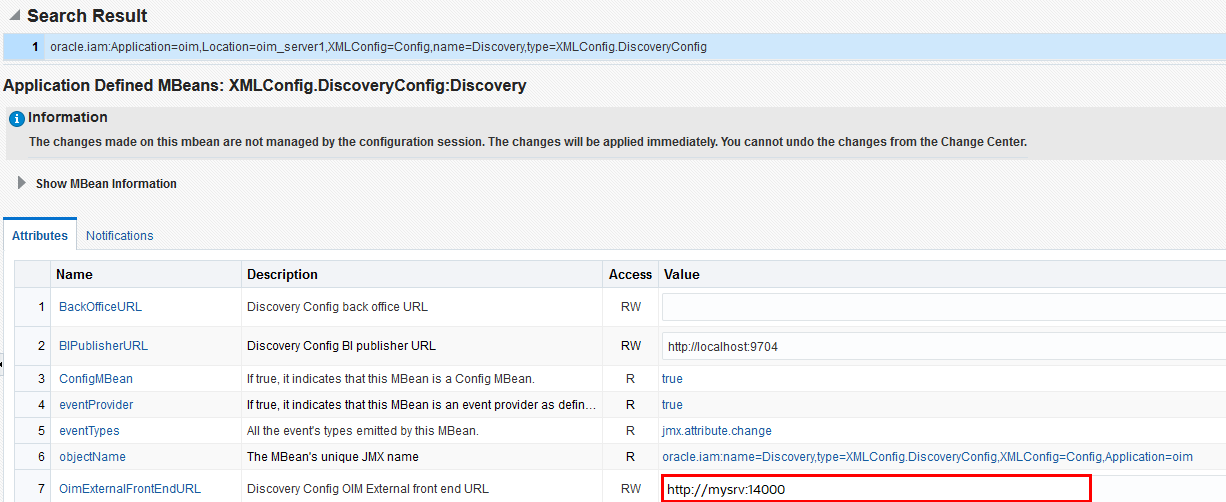
To obtain the OIG Server URL:- Log on to the Oracle Enterprise Manager Fusion Middleware Control.
- Navigate to the System MBean Browser and locate the XMLConfig.DiscoveryConfig MBean.
- Copy the value of the OimExternalFrontEndURL attribute and use this as the value for the Oracle Identity Governance Server URL.
- In the What is the OIG server user name? field, enter
the OIG user used for remediation and schema discovery.
Note:
The Oracle Identity Governance Server user can be any user that is a member of the System Administrator administration role. This role is required to perform the remediation process, and to support schema discovery for custom attributes. In the case where only remediation support is needed then user can be a member of the OrclOAGIntegrationAdmin administration role. With this user the schema discovery operation will fail. - In the OIG server password field, enter to authenticate the OIG server user when calling OIG APIs to perform remediation.
Note:
Information about the Oracle Identity Governance Server (URL, Username, and Password), and Oracle Identity Governance datasource (JDBC URL, Username, and Password) is required to integrate Oracle Access Governance and Oracle Identity Governance. Oracle Access Governance will use the Oracle Identity Governance data source to load the data and the Oracle Identity Governance Server URL to perform remediation operations. In case of a connection failure, the Oracle Access Governance agent automatically retries a maximum of three times to secure a connection with the Oracle Identity Governance server. - In the What is the JDBC URL of your OIG database
server? field, enter the JDBC URL for the OIG database you want
to connect with.
- Optionally, you can select to perform data loads using OIG database incremental
data load. If you select the Do you want to enable OIG database incremental
data load? option then Day-N data loads will use an event-driven mode
which applies changes to Oracle Access Governance as they happen, rather than as a periodic snapshot. If you select this
option, ensure that you have completed the prerequisite tasks in the OIG
database defined in Database Setup Steps for Event-driven Data
Load..
Note:
You should use this option if you want to see events from OIG in real-time rather than periodically. For example, if your organization creates an identity for a user which needs to be reflected in Oracle Access Governance immediately then you should use this option. When the identity is added, the event is noted by the integration and reconciled with AG. The default snapshot data load will not reconcile the new identity until its next scheduled run, when it will run a data load of all changes since the last. With the event-driven data load, changes are identified in real-time and loaded into Oracle Access Governance as each event takes place. - Enter filter attributes which will be used to filter the data that is returned
from OIG.You can add up to three filter name/value pairs which will be used to restrict the users and accounts ingested from Oracle Identity Governance by Oracle Access Governance. You can also set the search filter values separator to a character of your choice if required (default is
~).Details of the attributes you can use to set filters against can be found in Supported Attributes for User Data Load Filtering.
- Verify the details entered are correct, and click the Add button
- On the Download Agent step, select the
Download link and download the agent zip file to the
environment in which the agent will run.After downloading the agent, follow the instructions explained in the Agent Administration article.
- You are given a choice whether to further configure your orchestrated system before running a data load, or accept the default configuration and initiate
a data load. Select one from:
- Customize before enabling the system for data loads
- Activate and prepare the data load with the provided
defaults: If you select this option, the default matching rule
for Oracle Identity Governance
orchestrated system will be used.
Table 1-1 Default Matching Rule
Mode Authoritative Source
userName = userNameManaged System
Default rule is not supported. Matching is based on UID.