About Private Endpoints
When you set up an Oracle Analytics Cloud instance you have the option to restrict access through a private endpoint. Private access means that traffic doesn't go over the internet. Private access can be from hosts within your virtual cloud network (VCN) or your on-premise network.
For example:
-
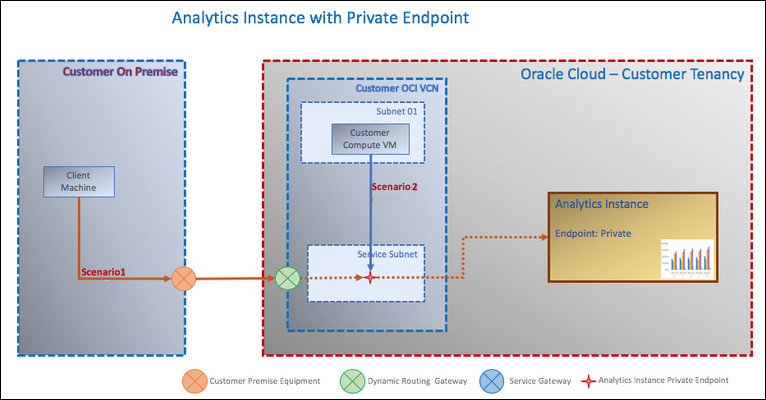
Scenario 1 - Allow access to Oracle Analytics Cloud from an on-premise (corporate) network. Don't allow access to anyone outside the corporate network.
- Scenario 2 - Allow access to Oracle Analytics Cloud from an Oracle Cloud Infrastructure VCN that's deployed in the same region as Oracle Analytics Cloud. Don't allow access to anyone outside the virtual cloud network.
When you deploy an Oracle Analytics Cloud instance with a private endpoint, the Oracle Analytics Cloud URL is only accessible from a browser if the client machine supports host name resolution. This means you must configure Domain Name Server (DNS) resolution on your private network to access the private endpoint. For example, you might use a DNS resolution strategy similar to that described in the article Hybrid DNS Configuration using DNS VM in VCN.
Description of the illustration oac_private_ep.jpg
The diagram shows Oracle Analytics Cloud deployed with a private endpoint. The private Oracle Analytics Cloud is only accessible through an Oracle Cloud Infrastructure VCN in your tenancy; you can't access Oracle Analytics Cloud from the public internet.
You must peer the VCN to your on-premise network. To enable access to Oracle Analytics Cloud, the on-premise network DNS must provide host name resolution for Oracle Analytics Cloud.
Ingress and Egress Access Control Rules
If you deploy Oracle Analytics Cloud with a private endpoint, you can restrict incoming traffic (ingress) to your service through predefined network security groups that contain one or more access rules.
If the Oracle Analytics Cloud uses a private access channel to connect to private data sources, you can also use network security groups to restrict outgoing traffic (egress) on the private access channel.
You can specify up to five network security group rules for incoming traffic and for outgoing traffic on the private access channel, and you can edit the rules whenever you want.