Call the Developer APIs with Resource Owner Password Credentials
Prerequisites to Complete
Before you can call the Oracle Integration Developer APIs with Resource Owner Password Credentials, you must create a confidential client application and perform other prerequisites. For instructions, see:- Access the Identity Domain.
- Configure prerequisites for your grant type: Prerequisites for Client Credentials and Resource Owner Password Credentials.
Information You Need
| Information You Need | Where to Find It |
|---|---|
| Design-time URL or Runtime URL, depending on your use case | See Do You Use the Design-time or Runtime URL?.
Example Design-time URL: Example Runtime URL: |
|
Domain Host |
You can get the identity domain host from the Domain URL field of the domain you are in. For instructions on accessing your domain, see Access the Identity Domain. 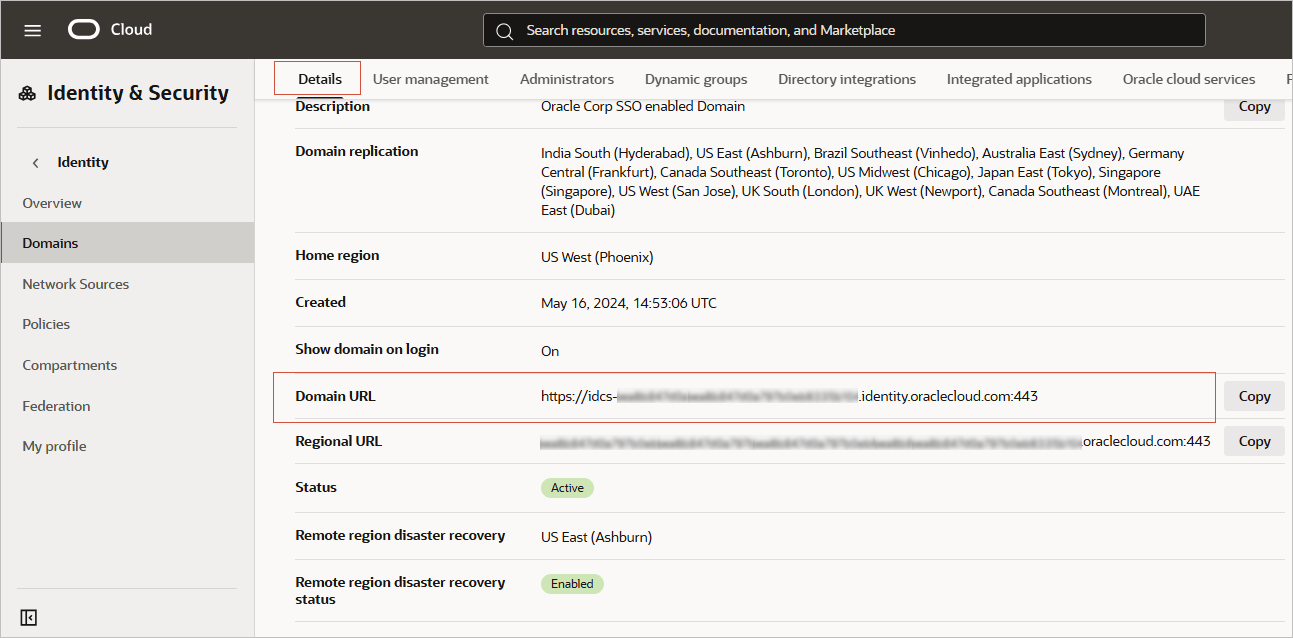 |
|
Client ID Client Secret |
Add the client ID for the confidential application that you configured. To find your confidential application, access the identity domain, select Integrated Applications, select your application, and look for OAuth Configuration, then Client ID and Client Secret. For instructions, see Access the Identity Domain. |
|
Scope |
Add the same scope that you added to your confidential application. You can find the scope you added to the confidential application in your confidential application details under Token Issuance Policy. To find your confidential application, access the identity domain, select Integrated Applications, select your application, and look for OAuth Configuration, then Client ID and Client Secret. For instructions, see Access the Identity Domain. This scope allows users to access both integration endpoints and Oracle Integration Developer APIs: This scope allows users to only access the Oracle Integration Developer APIs: |
|
Integration Instance |
Name of the integration instance. |
Configure Postman for Resource Owner Password Credentials
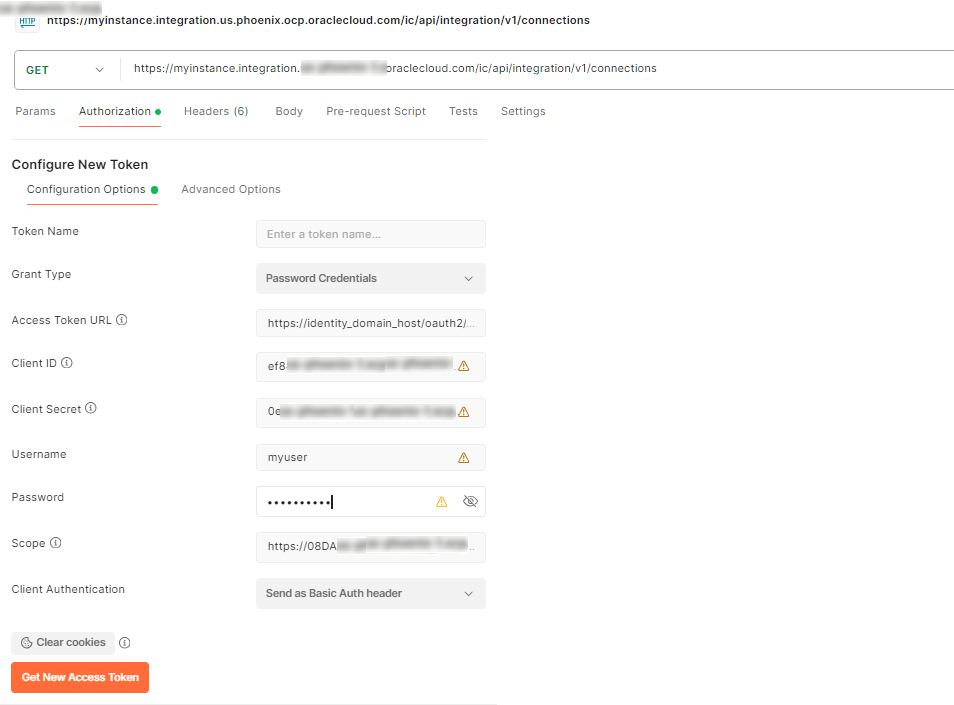
- Use the Design-time URL or Runtime URL depending on your use case. See Do You Use the Design-time or Runtime URL?.
Example Design-time URL with a call to the Oracle Integration Developer API for connections:
https://design-integration-region.oraclecloud.com/ic/api/integration/v1/connectionsExample Runtime URL:
https://myInstance-integration-region.oraclecloud.com/ic/api/integration/v1/connectionsNote:
If you use the Runtime URL, you'll need to configure Postman to Follow Authorization Header in the request settings. This is because if you call the Oracle Integration Developer APIs with the Runtime URL, Oracle Integration redirects to the Design-time URL for the Developer APIs and the call will fail if the authorization header is missing from the request header.
In cURL, use the
-loption to forward the authorization header during the redirection.To configure Postman to forward the authorization header when using the Runtime URL:- In the request, click Settings and enable Follow authorization header.
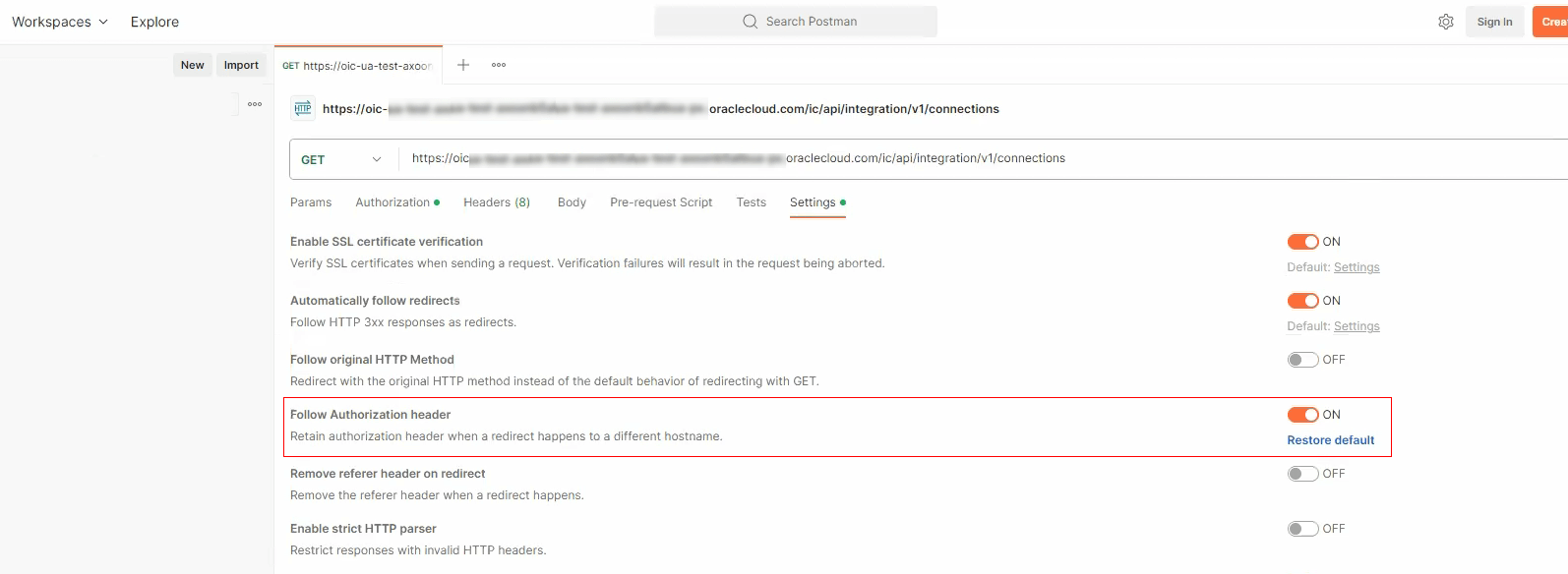
- In the request, click Settings and enable Follow authorization header.
- In the Authorization tab, fill in the required fields.
Field What to enter Authorization type
OAuth 2.0 Grant Type
Password credentials Access Token URL
Use the identity domain host you identified from your Domain URL. Example:
https://<identity_domain_host>/oauth2/v1/tokenClient ID
Add the client ID for the confidential application that you configured.
Client Secret
Add the client secret for the confidential application that you configured.
User Name and Password Provide a valid user name and password. This will generate the token with the resource owner password credentials. Scope
Add the same scope that you added to your confidential application.
Client Authentication
You can choose anything here, does not apply. - Click Get New Access Token.
- You are prompted to enter a user name and password.
This user must have been created in the IAM domain. You cannot use a single sign-on user name and password as this is a different authentication method. If you have single sign-on for your instance, you will need to copy the same users in IDCS and maintain a separate password for local IAM access.
- Click Use Token.
Your token is attached to your request in the Header section.
- Click Send to make the call to the API. You should get a list of connections.
cURL command for Resource Owner Password Credentials
- To fetch the access client, make a request with the user name and password in the payload. For example:
curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<identity_domain_host>/oauth2/v1/token -d 'grant_type=password&username=sampleUser&password=SamplePassword&scope=https://<Resource_APP_Audience>urn:opc:resource:consumer::all%20offline_access'Syntax:curl -i -H 'Authorization: Basic <base64Encoded_clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<Identity_Domain_Service_Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=password&username=<user-name>&password=<password>&scope=<App_Scope>%20offline_access'Where:<base64-clientid-secret>- Base 64 encode clientId:ClientSecret<username>- user for token needs to be issued (must be in serviceinvoker role).<password>- password for above user<app_scope>- Scope added while creating application in client configuration section (Ends with urn:opc:resource:consumer::all)
- Capture the
access_tokenandrefresh_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600, "refresh_token": "AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc=" } - Use the
access_tokenin the authorization header to invoke the Oracle Integration trigger endpoint.curl --location --request GET 'https://OIC host/OIC endpoint' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token, use the refresh token and make a request.
- Capture the
access_tokenandrefresh_tokenfrom the response for further use. For example:
Syntax:curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<Identity_Domain_Service_Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc='curl -i -H 'Authorization: Basic <base64-clientid-secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<Identity_Domain_Service_Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=<refresh_token>'