Restrictions
Note the following current restrictions when creating Oracle Integration instances and using them in Oracle Cloud Infrastructure US Government Cloud environments.
-
US Government Cloud environments currently don't support export and import of design-time metadata between instances (see Import and Export Instances in Provisioning and Administering Oracle Integration 3), whether you use the Import/Export page or the REST API Clone command in US Government Cloud environments. Note that you can import and export packages and project deployments.
-
In US Government Cloud realm (realm key: OC2) accounts, you can use login credentials (username and password) for console-based login flows. However, you can't use these login credentials for programmatic API invocations.
-
To run a scheduled integration in an Oracle Cloud Infrastructure US Government Cloud environment, you must use a non-federated account. The user should ideally be a service account user profile, and not an actual in-person user account profile.
If you use a federated account, the scheduler cannot trigger jobs and intermittently errors out with a
Schedule request submittedmessage. - If you use the FTP Adapter with private keys (with a passphrase) in government environments, only OpenSSH-formatted keys are supported. RSA keys are not supported if the private key is associated with a passphrase.
- The Oracle Autonomous Transaction Processing Adapter, Oracle Autonomous Data Warehouse Adapter, and Oracle Database Cloud Service Adapter do not support using the JDBC Basic Authentication security policy (also known as Username Password Token) with direct connectivity. You must use a wallet security policy (JDBC Over SSL or JDBC With OCI Signature) if you want to directly connect to database endpoints.
-
For users working in Chrome incognito mode: Add your Oracle Integration service instance application domain for third-party cookies as shown below. This workaround ensures users are logged out of their sessions after signing out.
-
From an incognito browser window, click
 , then Settings.
, then Settings.
-
Select Privacy and Security from the left pane, then Cookies and other site data.
-
Click Add next to Sites that can always use cookies.
-
In the Add a site dialog that appears, enter your service instance application domain, leave the two check boxes deselected, and click Add.
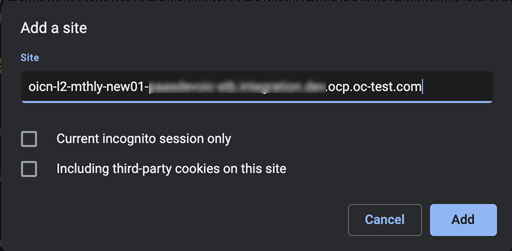
Description of the illustration incognito_cookies_workaround.png
This ensures users are logged out of their sessions after signing out.
-