About Network Access Options
Provides an overview of the network access options available when you provision or clone Autonomous AI Database.
Note:
For all of these options, the connections to your Autonomous AI Database use certificate-based authentication and Secure Sockets Layer (SSL).When you provision or clone your Autonomous AI Database you specify one of the following network access options:
-
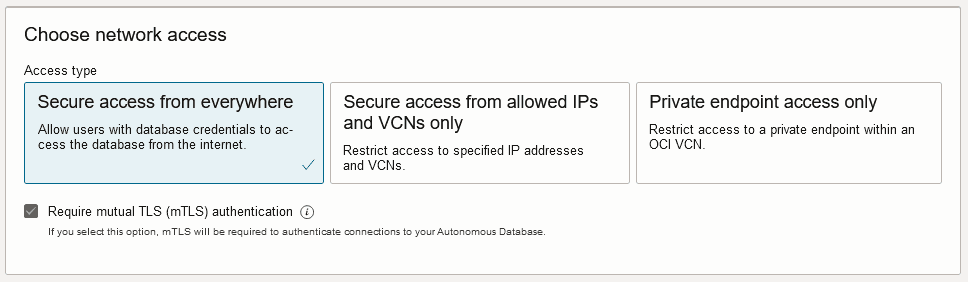
Secure access from everywhere: This option assigns a public endpoint, public IP and hostname, to your database. With this selection you have two options:
-
The database is accessible from all IP addresses: this is the default option when you provision or clone Autonomous AI Database.
If you configure your database with the Secure access from everywhere option, you can add, modify, or remove ACLs after you provision or clone the database.
See Overview of Restricting Access with ACLs for more information.
-
-
Secure access from allowed IPs and VCNs only: This option assigns a public endpoint, public IP and hostname, to your database. With this selection you must configure access control rules to restrict access by defining access control rules in an Access Control List (ACL). By specifying an ACL, the database will be accessible from allowed set of IP addresses or VCNs.
If you configure your database with the Secure access from everywhere option, you can add, modify, or remove ACLs after you provision or clone the database.
See Overview of Restricting Access with ACLs for more information.
-
Private endpoint access only: This option assigns a private endpoint, private IP, and hostname to your database. Specifying this option allows traffic only from the VCN you specify; access to the database from all public IPs or VCNs is blocked. This allows you to define security rules, ingress/egress, at the Network Security Group (NSG) level and to control traffic to your Autonomous AI Database.
See Configure Private Endpoints When You Provision or Clone an Instance for more information.
Note:
After you provision or clone your database, you can change the selection you make.See Configure Network Access with Access Control Rules (ACLs) and Private Endpoints for more information.