Tokenization
Tokenization is a process where physical or digital assets are represented by tokens, which can be transferred, tracked, and stored on a blockchain.
By representing assets as tokens, you can use the blockchain ledger to establish the state and ownership of an asset, and use standard blockchain platform functions to transfer ownership of an asset.
Blockchain App Builder includes tokenization support: token classes and methods are automatically generated, and additional token methods are provided so that developers can create complex business logic for tokens. The automatically generated project contains token lifecycle classes and functions, CRUD methods, and additional token SDK methods, and supports automatic validation of arguments, marshalling/unmarshalling, and transparent persistence capability. You can use these controller methods to initialize tokens, control access, set up accounts, manage roles, and manage the life cycle of tokens.
The following diagram shows the token architecture implemented by Blockchain
App Builder, including the token API and token SDK.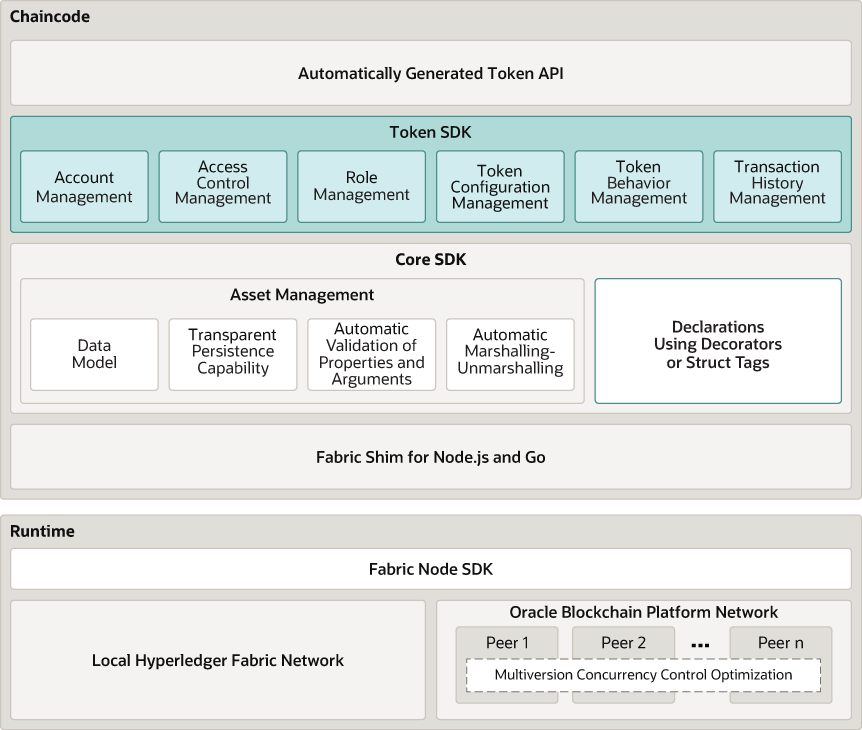
- Automatically Generated Token API
- Blockchain App Builder automatically generates methods to support tokens and token life cycles. You can use these methods to initialize tokens, manage roles and accounts, and complete other token lifecycle tasks without any additional coding.
- Token SDK
- The Token SDK includes methods that help you develop complex business logic for token applications.
- Multiversion Concurrency Control (MVCC) Optimization
- The MVCC optimization for token chaincode can reduce errors for transfer, mint, burn, and hold operations.
Tokens and the Account/Balance Model
Blockchain App Builder supports fungible and non-fungible tokens.
Fungible tokens have an interchangeable value. Any quantity of fungible tokens has the same value as any other equal quantity of the same class of token. Non-fungible tokens are unique. Tokens can also be either whole or fractional. Fractional tokens can be subdivided into smaller parts, based on a specified number of decimal places.
Tokens can also be described by behaviors. Supported behaviors for fungible
tokens include: mintable, transferable,
divisible, holdable, burnable,
and roles (minter, burner, and
holder). Supported behaviors for non-fungible tokens include:
mintable, transferable,
singleton, indivisible, burnable, and
roles (minter and burner).
The tokenization feature uses an account/balance model to represent tokenized assets as balances in an account. Accounts are similar to typical banking accounts, where deposits and transfers and other state transitions affect the balance of an account. The balance of every account is tracked globally, to ensure that transaction amounts are valid. The on-hold balance (for fungible tokens) and transaction history are also tracked.
Any user who possesses tokens or completes token-related operations at any
point must have an account on the network. Every account is identified by a unique ID
(account_id). The account ID is created by combining a user name or
email ID (user_id) of the instance owner or the user who is logged in
to the instance with the membership service provider ID (org_id) of the
user in the current network organization. Ready-to-use methods are provided for account
creation. Because the account ID includes the organization ID, users can be supported
across multiple organizations.
Token Standards
Blockchain App Builder extends the standards and classifications of the Token Taxonomy Framework, the ERC-721 standard, and the ERC-1155 standard to define the anatomy and behavior of tokens.
ERC-1155 is a standard that supports both fungible and non-fungible tokens (NFTs). ERC-721 is a standard for NFTs. The Token Taxonomy Framework was developed by the Token Taxonomy Initiative. For more information, see Token Taxonomy Framework.
| Standard | Supported Token Types |
|---|---|
| Token Taxonomy Framework |
|
| ERC-721 |
|
| ERC-1155 |
|
Tokenization Flow
Because Blockchain App Builder supports tokenization by extending the input specification file syntax, you create token-specific projects the same way that you create other projects, either by using the CLI or in Visual Studio Code.
For more information about creating projects with Blockchain App Builder, see Input Specification File.
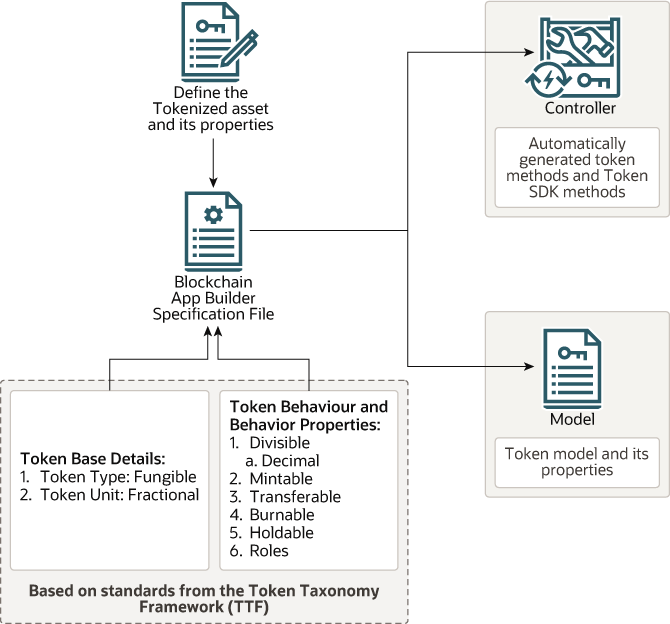
- Decide which token standard to use.
- Decide what token behaviors to specify (
mintable,transferable,divisible,indivisible,singleton,holdable,burnable, androles). - Define the token asset and its properties in the input specification file.
- Scaffold the chaincode project from the input specification file. This creates a scaffolded project, including a model that contains the token asset definition and its properties and a controller that contains the token's behavior and methods.
- Deploy and test the chaincode project.
- A token chaincode is deployed; the users in the list passed to the initialization method become
Token Adminusers of the chaincode. - A tokenized asset is initialized, which creates the
token_id, a unique identifier for that particular instance of token. - Accounts must be created for every user who will possess tokens or complete token-related operations.
- If the
rolesbehavior is specified for the token, then roles must be assigned to users before they can complete token-related operations. - Token lifecycle methods can then be used, based on the behaviors that were specified for the token asset. For example, you can call a method to mint tokens for an account.
Access Control
Tokenization support includes an access control feature that supports both role-based and ownership-based control mechanisms.
Token Admin or Token Minter. With
ownership-based control, you can restrict users from accessing assets that they do not
own. With ownership-based access control, specific methods can be called by the users
who own the assets, such as the Token Owner or Account
Owner. For specific information on access control for methods, see the
individual entries for the methods documented in the following topics:
- Token Admin
Token Adminusers can be assigned when a token chaincode is deployed. TheToken Adminuser information is saved in the state database. AToken Adminuser can grant and removeToken Adminprivileges for other users. AToken Adminuser cannot remove their ownToken Adminprivileges. AToken Adminuser can assign theOrg Admin, minter, burner, or notary role to any user.- Org Admin
- The extended Token Taxonomy Framework methods support the
Org Adminrole. AToken Adminuser can assign theOrg Adminrole to any user.Org Adminusers have administrative privileges, but only within their organization. They can create accounts or see account balances, but only for users in their organization.Org Adminusers who have a minter, burner, or notary role can assign that role to other users in their organization. - Token Minter
- A user who is assigned the minter role is a
Token Minter, and can mint tokens. - Token Burner
- A user who is assigned the burner role is a
Token Burner, and can burn tokens. - Token Notary
- A user who is assigned the notary role is a
Token Notary. AToken Notaryacts as a third party in transactions between payers and payees. AToken Notarycan either trigger the completion of a token transfer from a payer to a payee, or can instead return the tokens to the payer's account. - Vault Manager
- A user who is assigned the vault role is the
Vault Manager. TheVault Managercan unlock a locked NFT. The vault role is applicable only for the extended ERC-721 and ERC-1155 standards. Assigning the vault role to a user is a prerequisite for locking NFTs. Only one user per chaincode can be assigned the vault role. - Token Auditor
- Digital Assets Edition only: The extended Token Taxonomy Framework methods support the
Token Auditorrole. This role is similar to theToken Adminrole, but with read access only. - Org Auditor
- Digital Assets Edition only: The extended Token Taxonomy Framework methods support the
Org Auditorrole. This role is similar to theOrg Adminrole, but with read access only.
Role-based access control and ownership-based access control are also combined in some methods. For example, role-based access control lets a user with the minter role create tokens. With ownership-based access control, a non-fungible token owner can modify the custom properties of a token, but cannot modify the token metadata. When a user with the minter role creates a non-fungible token (NFT), they become the owner of the NFT. As the owner of that NFT, they can modify the custom properties (for an art collection token, the token price is a custom property). After the token creator transfers the NFT to another user, the second user becomes the owner, and the user who created the token is no longer the owner of the token. Because of ownership-based access control, the new owner can now update a custom property value, but the previous owner no longer can. Because of role-based access control, the previous owner can still mint an NFT, but the new user cannot.
You can also write your own access control functions, or disable access control. The automatically generated code that controls access is shown in the following examples.
await this.Ctx.<Token Standard>Auth.checkAuthorization(...)auth, err := t.Ctx.<Token Standard>Auth.CheckAuthorization(...)Note:
To remove the automatically generated access control function, remove the previous line of code from your TypeScript or Go project.MVCC Optimization
Hyperledger Fabric databases use multi-version concurrency control (MVCC) to avoid double-spending and data inconsistency.
When the same state is updated, a new version of the record overwrites the old version. If there are concurrent requests to update the same key in a block, an MVCC_READ_CONFLICT error might be generated.
To reduce MVCC errors for transfer, mint, burn, and hold operations, you can enable the MVCC optimization for token chaincode. This optimization works on Oracle Blockchain Platform only. By default, the optimization is disabled. To enable the optimization, complete the applicable following step.
- CLI: Specify the Boolean
-mor--enable_mvcc_optimizationparameter with theochain initcommand. By default, the parameter is set tofalse. To enable the optimization, add-m trueto theochain initcommand line. - Visual Studio Code: When you create a chaincode, select Enable MVCC optimization on the Create Chaincode window.
To use the optimization with chaincode created in previous versions of Blockchain App Builder, complete the following steps:
- After you install the latest version of Blockchain App Builder, upgrade the chaincode as described in Upgrading Chaincode Projects in the CLI and Upgrading Chaincode Projects in Visual Studio Code.
- Edit the
.ochain.jsonfile in the root folder of the chaincode to setenableMvccOptimizationtotrue. - Synchronize the chaincode, which adds the optimization and creates two
new folders in the root folder of the the chaincode:
statedbandtokens. For more information about synchronization, see Synchronize Specification File Changes With Generated Source Code and Synchronize Specification File Changes With Generated Source Code.
Other methods to work around MVCC_READ_CONFLICT errors include having the client application retry requests when this error is generated, or using a queue to capture concurrent requests before they are sent to the blockchain network. For more information, see Read-Write set semantics in the Hyperledger Fabric documentation.
Note:
The MVCC optimization does not work on hybrid networks that include both Oracle Blockchain Platform and Hyperledger Fabric peers, or when testing on a local Hyperledger Fabric network. Do not enable the MVCC optimization on hybrid networks, as this might lead to inconsistencies between peers.