Add Security Rules
If you plan to connect to your database via an Oracle Data Safe private endpoint, prior to registering your database, you need to add security rules to your virtual cloud network (VCN) to allow communication between your database and Oracle Data Safe.
Overview
You can add the necessary security rules to your virtual cloud network's (VCN's) security lists or network security groups (NSGs). Both stateful and stateless security rules are allowed. In general, the security rules need to 1) allow your database to receive incoming traffic from Oracle Data Safe, and 2) allow Oracle Data Safe to send requests to the database.
There are two approaches that you can take when creating the security rules. The first approach is to allow communication between Oracle Data Safe and all IP addresses within the same subnet (0.0.0.0/0). With this configuration, Oracle Data Safe can connect to all of your databases in the subnet.
- In the NSG or security list for your database, add an ingress rule that allows your database's private endpoint IP address on the database's port to receive incoming traffic from Oracle Data Safe's private endpoint IP address from all ports.
- In the NSG or security list for your Oracle Data Safe private endpoint, add an egress rule that allows Oracle Data Safe's private endpoint IP address on all ports to send requests to the database's private endpoint IP address on the database's port. If the database has multiple IP addresses, you need configure an egress rule for each IP address. In the case of an On-Premises Oracle AI Database, you only need to configure an egress rule, and not an ingress rule.
For more information about security lists and network security groups, see Access and Security in the Oracle Cloud Infrastructure documentation.
Add Security Rules for Oracle Autonomous AI Database Serverless with Private VCN Access
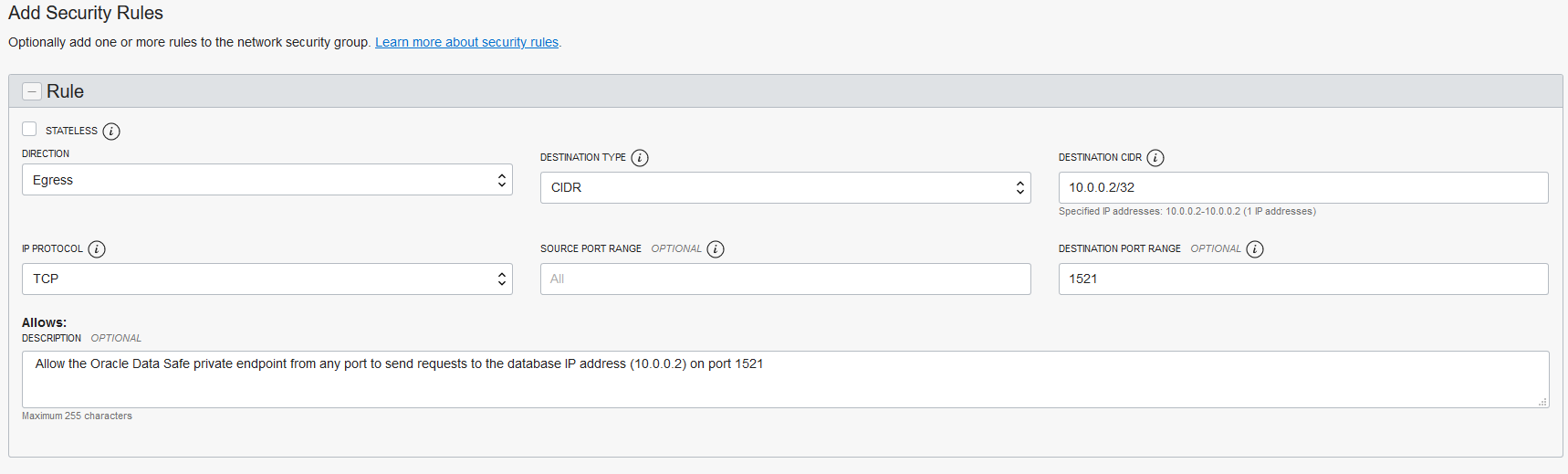
For Oracle Autonomous AI Database Serverless with Private VCN Access, you need to create an ingress rule and an egress rule in the database's virtual cloud network (VCN) in Oracle Cloud Infrastructure.
Add Security Rules for Autonomous AI Database on Dedicated Exadata Infrastructure
Add Security Rules for an Oracle Cloud Database
For an Oracle Cloud Database, you need to create an ingress rule and an egress rule in the database's virtual cloud network (VCN) in Oracle Cloud Infrastructure.
Add Security Rules for an Oracle AI Database on Compute
If you plan to connect to your Oracle AI Database on Compute by using an Oracle Data Safe private endpoint, create an ingress rule and an egress rule on the database's virtual cloud network (VCN) in Oracle Cloud Infrastructure. If the database is in a non-Oracle cloud environment, configure the ingress rule in the non-Oracle Cloud environment.
- Obtain the IP address and the name of the NSG or security list for your database's private endpoint. You can find your database information in your database's Console in Oracle Cloud Infrastructure.
- Obtain the IP address and the name of the NSG or security list for the Oracle Data Safe private endpoint. You can find the Oracle Data Safe private endpoint information on the Private endpoint information page in the Oracle Data Safe service in Oracle Cloud Infrastructure.
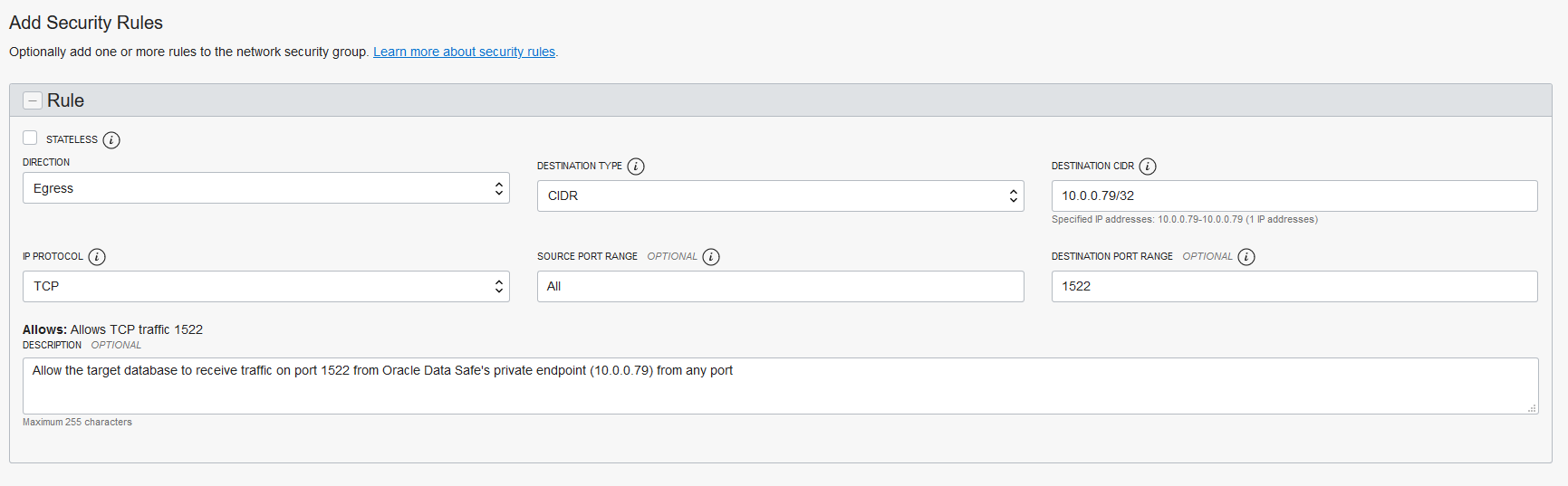
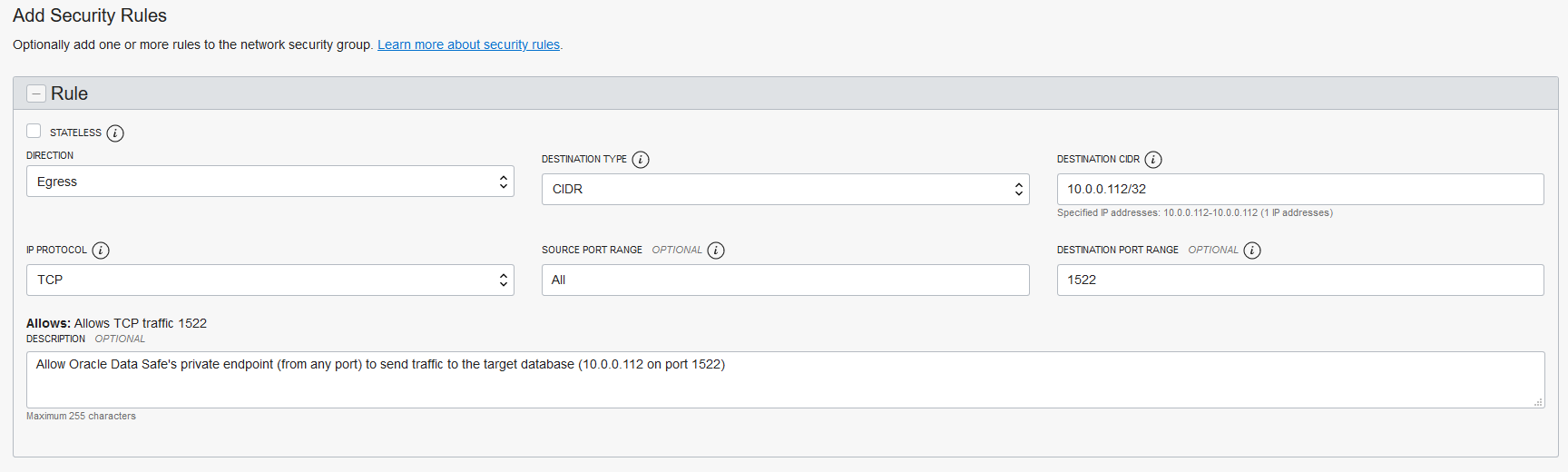
- Open the VCN for your database, either in Oracle Cloud Infrastructure or in a non-Oracle cloud environment. In the database's NSG or security list, create an ingress rule that allows your database's private endpoint IP address (for example, 10.0.0.112/32) on the database's port (for example, 1521) to receive incoming traffic from Oracle Data Safe's private endpoint IP address (for example, 10.0.0.79/32) from all ports.
- In Oracle Cloud Infrastructure, open the VCN for your Oracle Data Safe private endpoint. In the Oracle Data Safe private endpoint's NSG or security list, create an egress rule that allows Oracle Data Safe's private endpoint IP address (for example, 10.0.0.79/32) on all ports to send requests to the database's private endpoint IP address (for example, 10.0.0.112/32) on the database's port (for example, port 1521).
Add Security Rules for an Oracle On-Premises Database
For an On-Premises Oracle AI Database, you need to create an egress rule in the virtual cloud network (VCN) for your Oracle Data Safe private endpoint. You do not need to create an ingress rule.
Add Security Rules for an Oracle Exadata Database Service on Cloud@Customer Database
Update the security list for your virtual cloud network (VCN) in Oracle Cloud Infrastructure, and if implemented, the network security group for your database subnet, to allow traffic from the Oracle Data Safe private endpoint to your database. This step allows Oracle Data Safe to access your database. A security list acts as a virtual firewall for your database and consists of a set of ingress and egress security rules that apply to all the VNICs in any subnet that the security list is associated with. Both stateful and stateless security rules in the security list are allowed. For more information about security lists and network security groups, see Access and Security in the Oracle Cloud Infrastructure documentation.
By default, every deployment of an Oracle Exadata Database Service on Cloud@Customer database is associated with a Single Client Access Name (SCAN), and the SCAN is associated with 3 IP addresses. Each database system configuration contains compute nodes (database servers). There is one database server VIP address per compute node in the VM cluster.
When you use an Oracle Data Safe private endpoint to connect your Oracle Exadata Database Service on Cloud@Customer database to Oracle Data Safe, you need to create an egress security rule for the Oracle Data Safe private endpoint. Configure the rule to allow communication between the Oracle Data Safe private endpoint (from any port) and all database server VIPs and SCAN addresses (all three).
Example 3-3 Configure a stateful security rule for an Oracle Exadata Database Service on Cloud@Customer database and an Oracle Data Safe private endpoint
This example shows a stateful security rule for an Oracle Exadata Database Service on Cloud@Customer database and an Oracle Data Safe private endpoint. The egress security rule on the virtual cloud network (VCN) in Oracle Cloud Infrastructure allows the private endpoint (from any port) to send requests to two database server VIPs ( 1.1.1.3 and 1.1.1.5) and three SCAN addresses (1.1.1.6, 1.1.1.7, and 1.1.1.8) on port 1521. Always include the database server VIPs in the egress security rule.
The following diagram illustrates the Oracle Data Safe private endpoint, the database, and the egress security rule.
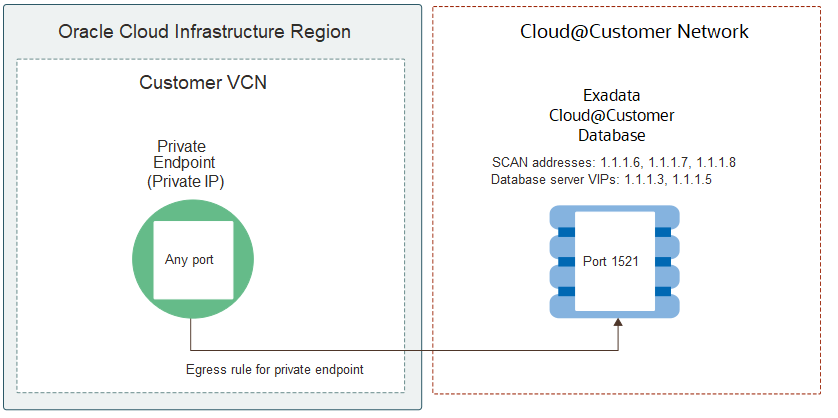
Description of the illustration exacc-egress-rule.png
The following screenshot shows you the Oracle Exadata Database Service on Cloud@Customer network configuration for the VM cluster in Oracle Cloud Infrastructure, where you can find the SCAN addresses and database server VIPs.
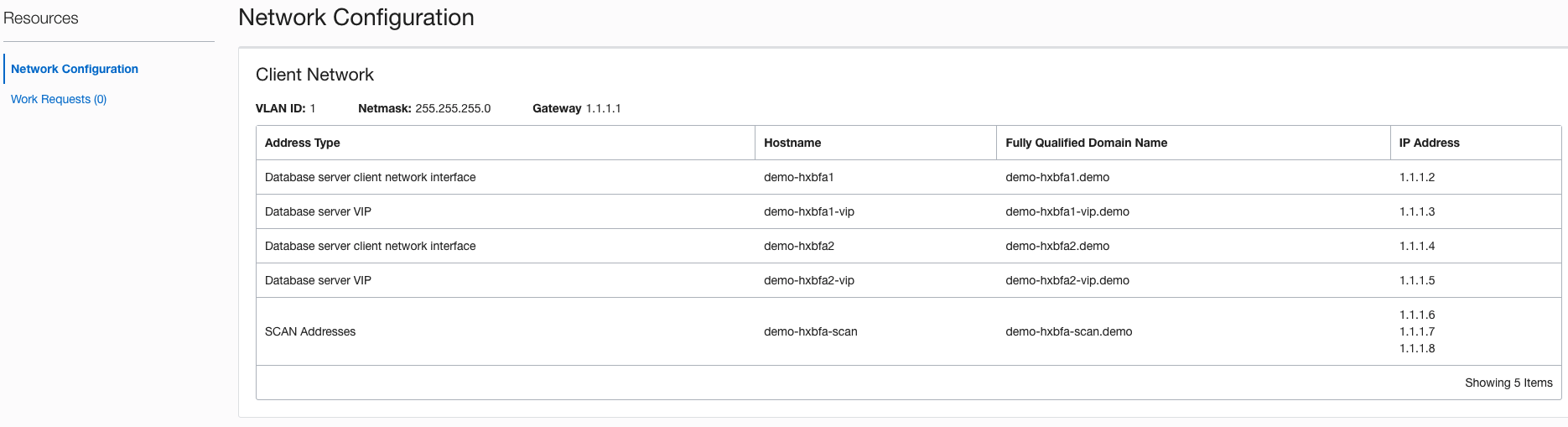
Description of the illustration exacc-network-configuration.png