Connect to Oracle Cloud Infrastructure GoldenGate using a private IP
Overview
OCI GoldenGate is only accessible using a private endpoint from within the OCI network, or through a bastion host that secures access to OCI resources. While this quickstart example uses OCI Bastion, it is possible for you to use your own bastion. This quickstart includes both options, so you can choose the one that works best for you.
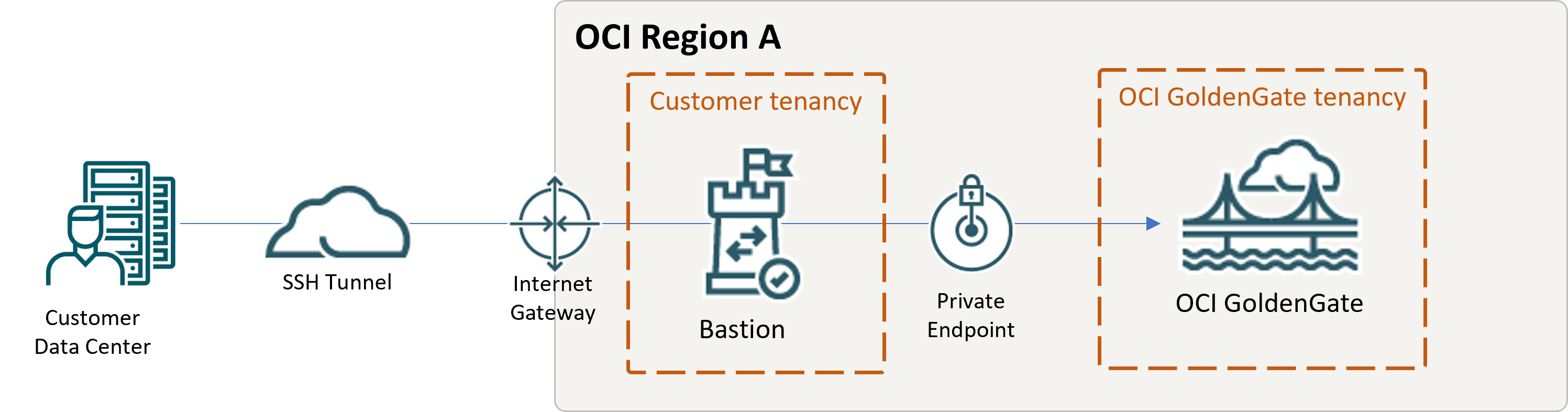
Description of the illustration qs-bastion.png
Before you begin
You must have the following in order to proceed:
- A free trial or paid Oracle Cloud Infrastructure account
- Access to OCI GoldenGate
- An OCI GoldenGate deployment in a private subnet and without a public endpoint
- For OCI Bastion:
- Access to the service
- Access to OCI Bastion or your own bastion on OCI Compute
- For your own bastion on OCI Compute:
- Access to OCI Compute
- Public and private subnets configured in each availability
domain
Note:
Oracle recommends creating a separate public subnet solely for bastion hosts to ensure that the appropriate security list is assigned to the correct host.
Option A: Use OCI Bastion
You can use OCI Bastion or use your own. This example uses OCI Bastion.
- Create a bastion. Ensure that
you:
- Use the same VCN as the target OCI GoldenGate deployment and
subnet.
Note:
The subnet can be the same as the OCI GoldenGate deployment or one that has access to the OCI GoldenGate subnet. - Include the IP addresses of the machines used to connect to OCI Bastion in the CIDR Block Allowlist.
- Use the same VCN as the target OCI GoldenGate deployment and
subnet.
- Create a SSH port forwarding
session.
- For IP Address, enter the OCI GoldenGate deployment's private IP. You can find the private IP on the deployment's Details page.
- For Port, enter
443. - Under Add SSH Key, provide the public key file of the SSH key pair to use for the session.
- After the session is created, from the session's Actions (three dots) menu, select Copy SSH Command.
- Paste the command into a text editor, and then replace the
<privateKey>and<localPort>placeholders with the path to the private key and port 443. - Run the command using the command line interface to create the tunnel.
- Open a web browser and go to
https://localhost.
Note:
- Ensure that you add an Ingress rule for the Bastion host in Private Subnet's security list. Learn more.
- If you encounter the following error message,
{"error":"invalid_redirect_uri","error_description":"Client xxdeploymentgoldengateusphoenix1ocioraclecloudcom_APPID requested an invalid redirect URL: https://localhost/services/adminsrvr/v2/authorization. ECID: cvSDu0r7B20000000"}then you must add an entry in your client machine hosts file to map 127.0.0.1 to your deployment FQDN. For example:
127.0.0.1 xx.deployment.goldengate.us-phoenix-1.oci.oraclecloud.com
Known issues
Invalid redirect url error when trying to access an IAM-enabled deployment using an IP
When attempting to access an IAM-enabled deployment using the deployment's IP address, you encounter the following error:
{"error":"invalid_redirect_uri","error_description":"Client
xxxxxxxx1ocioraclecloudcom_APPID requested an invalid redirect URL: https://192.x.x.x/services/adminsrvr/v2/authorization. ECID:
xxxx"}Workaround: You can do one of the following:
Option 1: Add the deployment IP address to your Identity Domain Application. To make this change, you must be part of the user group assigned to the application.
- In the Oracle Cloud navigation menu, select Identity & Security, then under Identity, click Domains.
- Select your domain from the Domains list.
- From the domain's Identity Domain resource menu, select Oracle Cloud Services.
- Select your application from the Oracle Cloud Services list. For
example, GGS INFRA Application for Deployment Id:
<deployment OCID>. - On the application page under OAuth configuration, click Edit OAuth configuration.
- For Redirect URL, enter the deployment's
Console URL with the deployment's IP in place of the domain. For example:
https://<deployment-ip>/services/adminsrvr/v2/authorization. - Save your changes.
127.0.0.1 to your deployment FQDN (replace
<region> with the appropriate region). For example:
127.0.0.1 xx.deployment.goldengate.<region>.oci.oraclecloud.com