Using the Tags Trust Scope
The Tags trust scope allows a trusted or confidential client application to acquire an access token that gives access to other resources based on the defined tags.
Note:
The option to define thetrustScope parameter is available to only trusted and confidential client applications. The option is not available to public client applications.
To use the Tags trust scope:
-
Assign the value of
Tagsto thetrustScopeparameter to enable the client application to access tags from other applications.Note:
ThetrustScopeattribute ofTagsis named Tagged in the Oracle Identity Cloud Service administrative console. -
Define the
key:valuepair for theAllowedTagsparameter.Note:
These steps assume that the appropriate Resource App has definedkey:valuepairs for theTagsattribute and that at least onekey:valuepair from the list of theallowedTagsattribute of the Client App match onekey:valuepair of theTagsattribute of the Resource App.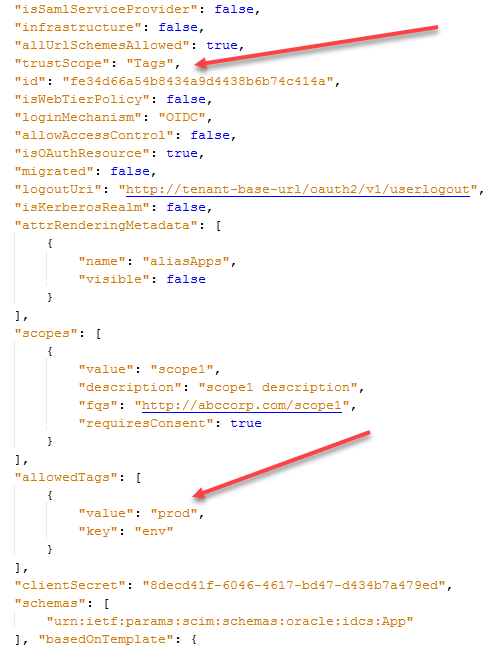
-
Request an access token using the trusted or confidential client and request the scope
urn:opc:resource:consumer::all.The access token in the response contains the audienceurn:opc:resource:scope:tag=<base64 encoded JSON>and the scopeurn:opc:resource:consumer::all,which gives access to Resource Apps that have tags that match the allowed tags specified in the Client App.
Note:
The requested scope should always exist and match, either directly or hierarchically, the client's defined allowed scopes to allow the client access to the resource.Using Fine-Grained Scopes
urn:opc:resource:consumer::all scope, you can also specify the following fine-grained scopes:
-
urn:opc:resource:consumer:paas::read -
urn:opc:resource:consumer:paas:stack::all -
urn:opc:resource:consumer:paas:analytics::read
urn:opc:resource:consumer:paas:analytics::read scope in its request for access to a resource. If the scope directly matches an allowed scope defined, then in the returned access token the audience is urn:opc:resource:scope:tag=<base64 encoded JSON> and the scope is urn:opc:resource:consumer:paas:analytics::read.If the allowed scope defined by the client is urn:opc:resource:consumer:paas::read, then the client app is allowed to access the resource hierarchically if the client requests one of the following scopes: urn:opc:resource:consumer:paas::read or urn:opc:resource:consumer:paas:analytics::read. However, if the requested scope is urn:opc:resource:consumer:paas:analytics::write, then the client isn't allowed access to the resource, since that isn't one of the allowed scopes defined by the client app.
Request and Response Examples
The following examples show request and response examples for the client credentials flow using the urn:opc:resource:consumer::all scope.
Request Example
curl -i
-H 'Authorization: Basic MjA3Mz....zllNjI2'
-H 'Content-Type: application/x-www-form-urlencoded; charset=utf-8'
--request POST 'https://tenant101.idcs.internal.oracle.com:8943/oauth2/v1/token' -d 'grant_type=client_credentials&scope=urn:opc:resource:consumer::all'Response Example
{
"access_token":"eyJ4NX....ZbDtAw",
"token_type":"Bearer",
"expires_in":3600
}Note:
The access token contains the audienceurn:opc:resource:scope:tag=<base64 encoded JSON> and the scope urn:opc:resource:consumer::all. The following is an example of what a decoded audience looks like: aud:["urn:opc:resource:scope:tag=eyAidGFncyI6WyB7ICJrZXkiOiJjb2xvciIsInZhbHVlIjoiZ3JlZW4ifSAsICB7ICJrZXkiOiJjb2xvciIsInZhbHVlIjoiYmx1ZSJ9IF19"]The following examples show request and response examples for the client credentials flow using a fully-qualified scope.
Request Example
curl -i
-H 'Authorization: Basic MzRjYz....Q3OWVk'
-H 'Content-Type: application/x-www-form-urlencoded; charset=utf-8'
--request POST 'https://tenant-base-url/oauth2/v1/token' -d 'grant_type=client_credentials&scope=http://abccorp1.com/scope1'Response Example
{
"access_token":"eyJ4NXzF.....rT5SH7sUw",
"token_type":"Bearer",
"expires_in":3600
}