 Before You Begin
Before You Begin
This 15-minute tutorial shows you how to use Oracle Identity Cloud Service's GenericSCIM templates to synchronize users, groups, and user-to-group assignments between two Oracle Identity Cloud Service instances.
Background
Customers who are running multiple cloud environments (for example, Development, Test, and Production) or who need to migrate users from one Identity Cloud Service to another, can benefits from GenericScim templates to synchronize users between these instances.
The GenericSCIM templates are available from the App Catalog and help you to easily integrate two Oracle Identity Cloud Service instances for provisioning and synchronization purposes.
The following scenario demonstrate the use of the GenericScim - Client Credential template to synchronize users from an Oracle Identity Cloud Service instance to another one.
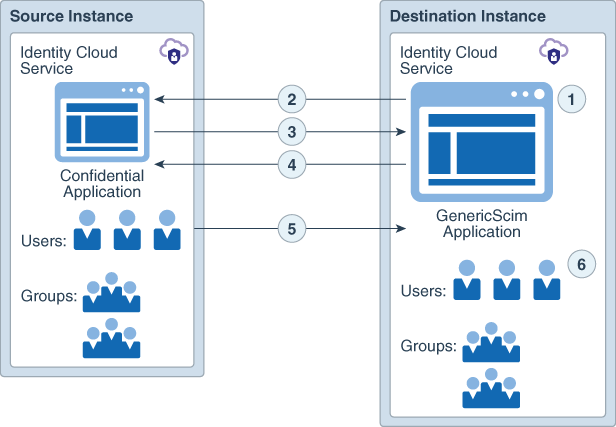
The user synchronization process consists of the following steps:
- Either an application administrator or scheduler triggers the GenericScim - Client Credential application to run the synchronization job.
- The GenericScim - Client Credential applicaiton requests an access token to the source instance of Oracle Identity Cloud Service by using the client id and secret from a confidential application.
- The confidential application issues an access token.
- The GenericScim - Client Credential application uses the access token to make subsequent REST API calls to the source instance.
- These REST API calls list all users, groups, and user-to-group assignments from the source instance.
- The respective users, groups, and user-to-group assignments are created in the destination instance of Oracle Identity Cloud Service.
These users are also assigned to the GenericScim - Client Credential application.
The GenericSCIM templates runs full synchronization between the source and destination. If any user is removed from the source, then next time the synchronization job runs the corresponding user will be removed from the destination instance.
What Do You Need?
You need access to two Oracle Identity Cloud Service instances.
- SOURCE_INSTANCE: This is the instance from where users are synchronized. You need user credentials assigned to User Administrator role to be able to create users and groups, and Application Administrator role to configure a client credential application.
- DESTINATION_INSTANCE: This is the instance to where users are synchronized. You need user credentials assigned to User Administrator and Application Administrator roles.
 Create Users and Groups in the Source Instance
Create Users and Groups in the Source Instance
There are many methods to create multiple users, groups, and groups assignments in Oracle Identity Cloud Service. This example uses Oracle Identity Cloud Service's REST endpoint /admin/v1/Bulk.
- Download the bulk_upload_users_groups.json file to your desktop.
- Register an confidential application and get an access token from the source Oracle Identity Cloud Service instance. See Make Your First REST API Call.
- Open a command prompt in the location where you downloaded the JSON file, and then run the following command to create multiple users:
curl -X POST -H "Content-Type:application/scim+json" -H "Authorization: Bearer ACCESS_TOKEN" -d @"bulk_upload_users.json" "https://SOURCE_INSTANCE/admin/v1/Bulk"Note: Replace the ACCESS_TOKEN and SOURCE_INSTANCE values in the above command before running.
- Sign in to the Identity Cloud Service console of the source instance as a user administrator.
- Expand the Navigation Drawer, click Users, and then verify the users from the JSON file were created.
 Configure a Confidential Application in the Source Instance
Configure a Confidential Application in the Source Instance
Create a confidential application so that the GenericScim - Client Credential template in the Oracle Identity Cloud Service destination instance can connect to the source instance.
- Sign in to the Identity Cloud Service console of the source instance as an application administrator.
- Expand the Navigation Drawer, click Applications, and then click Add.
- In the Add Application window, click Confidential Application.
- Enter name as
SCIM Client Credentialand then click Next. - In the Client pane, click Configure this application as client now, and select Client Credentials as Allowed Grant Types
- Scroll down, click the Add button below Grant the client access to Identity Cloud Service Admin APIs.
- In the Add App Role window, select User Administrator role and then click Add.
- Click Next in the Client pane and in the following panes until you reach the last pane. Then click Finish.
- In the Application Added dialog box, make a note of the Client ID and Client Secret values (because the GenericScim template from the destination Identity Cloud Service needs these values), and then click Close.
- To activate the application, click Activate.
 Configure the GenericSCIM Template in the Destination Instance
Configure the GenericSCIM Template in the Destination Instance
Configure a GenericSCIM Template in your Oracle Identity Cloud Service destination instance to synchronize users from the source instance.
- Sign in to the Identity Cloud Service console of the destination instance as an application administrator.
- Expand the Navigation Drawer, click Applications, and then click Add.
- In the Add Application window, click App Catalog.
- In the App Catalog page, search for
GenericScim, and then click Add for the GenericScim - Client Credentials row. - In the Add GenericScim - Client Credentials page, enter name as
Source Identity Cloud Service. - In the Provisioning pane, click Enable Provisioning, and then click Continue in the Grant Consent window.
- In the Configure Connectivity section, provide the following information:
- Host Name: For example,
idcs-source.identity.oraclecloud.com - Base URI:
/admin/v1 - Client Id: Enter the Client ID you made note from the confidential application.
- Client Secret: Enter the Client Secret you made note from the confidential application.
- Scope:
urn:opc:idm:__myscopes__ - Authentication Server Url: For example,
https://idcs-source.identity.oraclecloud.com/oauth2/v1/token - Click Test Connectivity to test the communication between the two Oracle Identity Cloud Service instances.
- In Select Provisioning Operations section, click Authoritative Sync.
- Click Enable Synchronization, and then click Save.
- Click Activate to activate the application.
The success message Connection successful appears.
 Use the GenericSCIM Template to Import Users, Groups, and Groups Assignments
Use the GenericSCIM Template to Import Users, Groups, and Groups Assignments
Import users from one Oracle Identity Cloud Service instance to another.
- In the Source Identity Cloud Service application page, click the Import tab, and then click Import.
- Click Refresh until the job status changes to status Succeeded.
- For every user in the list, verify the Synchronization Status is Confirmed.
The message Your job for importing accounts is running. appears.
After the job finishes, the list of users synchronized from the source Identity Cloud Service appears.
 Verify Users are Synchronized to Oracle Identity Cloud Service Destination Instance
Verify Users are Synchronized to Oracle Identity Cloud Service Destination Instance
Verify the users are created in the destination Oracle Identity Cloud Service.
- Sign in to the Identity Cloud Service console of the destination instance as a user administrator.
- Expand the Navigation Drawer, click Users.
- Verify the users from the source Identity Cloud Service were created.
 Remove Users and Groups from the Source Instance
Remove Users and Groups from the Source Instance
To demonstrate the GenericScim template full synchronization feature, remove the users and groups from the source instance, and run the import in the destination instance.
Remove Users and Groups from the Source Instance
- Sign in to the Identity Cloud Service console of the source instance as a user administrator.
- Expand the Navigation Drawer, and then click Users.
- In the Users page, select the users from User01 Test to User10 Test, click More, and then click Remove.
- In the confirmation window, click OK.
- In the Navigation Drawer, click Groups.
- In the Groups page, select the groups from Group A to Group D, and then click Remove.
- Sign out from the source instance.
Run Import and Verify Users and Groups in the Destination Instance
- Sign in to the Identity Cloud Service console of the destination instance as an application administrator.
- Expand the Navigation Drawer, click Applications, and then click the Source Identity Cloud Service application.
- In the Source Identity Cloud Service application page, click the Import tab, and then click Import.
- Click Refresh until the job status changes to Succeeded.
After the job finishes, the GenericScim template lists the users synchronized from the source Identity Cloud Service.
- Verify users from User01 Test to User10 Test don't appear in the list.
- In the Navigation Drawer, click Users.
- Verify the users from User01 Test to User10 Test don't appear in the list.
- In the Navigation Drawer, click Groups.
- Verify the groups from Group A to Group D don't appear in the list.
 (Optional) Modify the Default Attribute Mapping
(Optional) Modify the Default Attribute Mapping
You can change the GenericScim template's default attribute mapping between the two instances of Oracle Identity Cloud Service.
- Sign in to the Identity Cloud Service console of the destination instance as an application administrator.
- Expand the Navigation Drawer, and then click Applications.
- In the Application page, click Source Identity Cloud Service.
- In the Source Identity Cloud Service page, click the Provisioning tab, scroll down, and then click Attribute Mapping.
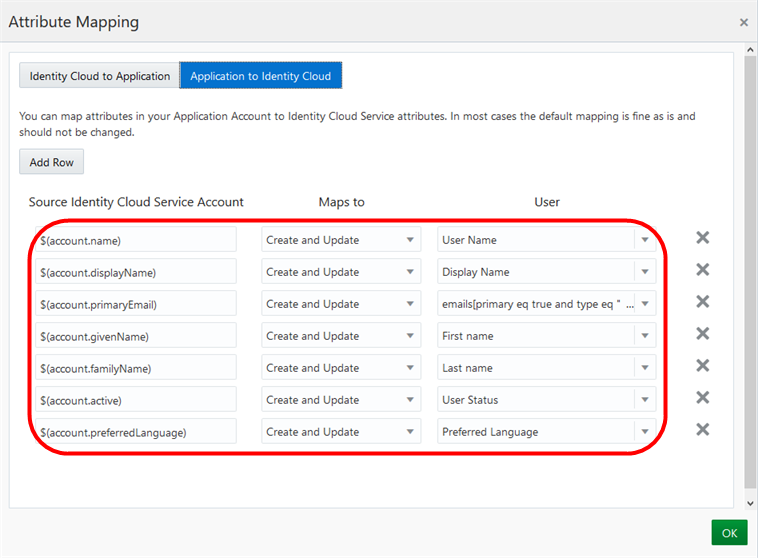
- In the Attribute Mapping page, click the Application to Identity Cloud tab, and then verify the default attribute mapping doesn't map the Title field from the source Oracle Identity Cloud Service.
- Click Add Row, to add a new entry to map the Title field.
- In the newly created row, provide the following values, and then click OK:
- Source Identity Cloud Service Account:
$(account.title) - Maps to: Select Create and Update.
- User: select Title.
- In the Source Identity Cloud Service application page, click the Import tab, and then click Import.
- Click Refresh until the job status changes to status Succeeded.
- For every user in the list, verify the Synchronization Status as Confirmed.
- In the Navigation Drawer, click Users.
- Verify that each user have the Title field with value.
 Want to Learn More?
Want to Learn More?
- Tutorial: Onboard users and groups
- Tutorial: Make Your First REST API Call
- Video: Use SCIM Templates to Provision and Synchronize Users to Applications
- Documentation: Use the SCIM Interface to Integrate Oracle Identity Cloud Service with Custom Applications
- Documentation: Create a Bulk Request
- Documentation: About Multiple Instances
- A-Team blog: Identity Cloud Service Migration/Sync Strategy
 Synchronize Users and Groups Between Oracle Identity Cloud Service Instances
Synchronize Users and Groups Between Oracle Identity Cloud Service Instances