Configure OAuth Token Generation for Invoking IDCS-Based Process Service Instance Endpoints
The Oracle Cloud Infrastructure Process Automation REST services support token-based authorization, and are not accessible using only the user name and password. This topic gives an overview of how to invoke the Developer API for Oracle Cloud Infrastructure Process Automation with an OAuth2 access token using Resource Owner access grant type.
Main Configuration Steps
To acquire the OAuth token from Oracle IDCS, you must first:
-
Sign in to the IDCS administration console using an administrator user name and password.
-
Create an OAuth client application with resource owner grant type and note its client ID and client secret.
-
Use the client ID and client secret to request an access token from the Oracle IDCS OAuth Service.
-
Include the access token in the appropriate HTTP header when you make the Developer API for Oracle Cloud Infrastructure Process Automation calls.
You can obtain an OAuth token in one of these ways:
-
Directly: Maintain Oracle IDCS app client information as part of your client (for example, a mobile app) and then directly invoke IDCS to obtain the OAuth token.
-
With an intermediate layer: The client ID and client secret are protected information and so the consumer (your web or mobile app) can make use of an intermediate layer (for example, a Relay Servlet) on the server that has safe access to the client ID and client secret. The intermediate layer can then fetch the IDCS token and relay it back to the consumer.
Create and Register a Client Application
Refer Configure a Confidential Application to Authenticate with OAuth.
Generate OAuth Access Tokens Using Resource Owner Grant Flow
The following steps show how you can access a token using curl commands for development purposes. You can follow the same steps by using a REST client to fetch the token. In production scenarios, you can code a relay servlet to fetch the token using http client APIs.
Note:
IDCS also supports various other grant flows, and you can choose an appropriate type based on your use case. For more information please refer this linklink. TheDeveloper APIs for Oracle Cloud Infrastructure Process Automation do not support Client Credentials and Device Code Grant Type grant flow, and they can be invoked only using an end user's token.
-
Get Client ID and Client Secret from the IDCS Admin Console and note them.
-
Generate the OAuth access token.
-
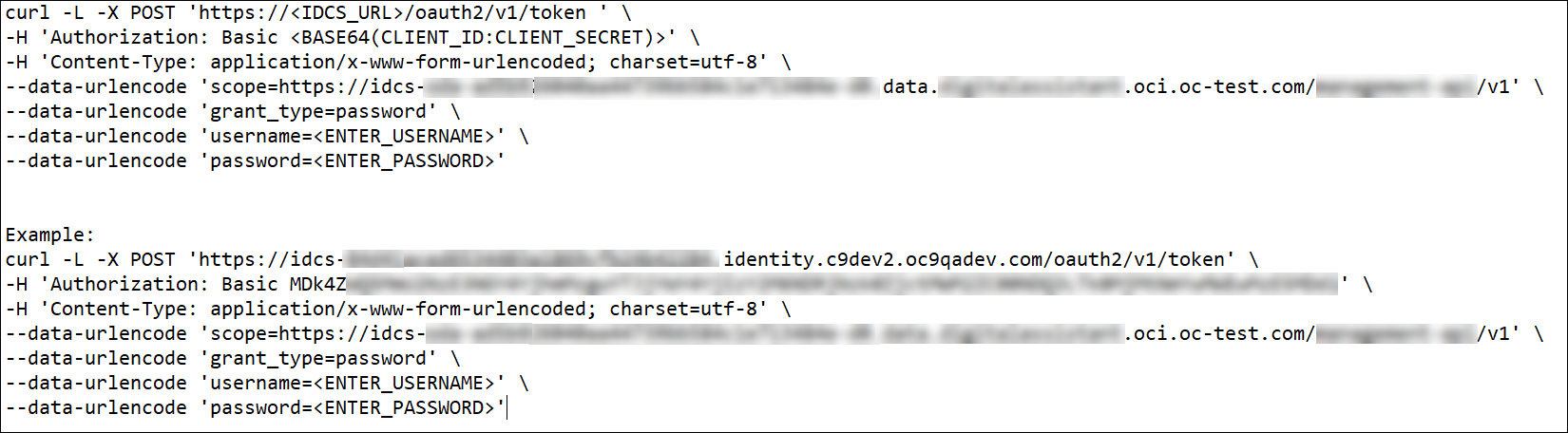
Invoke the following REST API.
curl -L -X POST 'https://<IDCS_URL>/oauth2/v1/token '\ -H 'Authorization: Basic <BASE64(CLIENT_ID:CLIENT_SECRET)>'\ -H 'Content-Type: application/x-www-form-urlencoded; charset=utf-8'\ --data-urlencode 'scope=https://idcs-opa-ad5b91234567890.data.processautomation.oci.oc-test.com/process/v1'\--data-urlencode 'grant_type=password'\ --data-urlencode 'username=<ENTER_USERNAME>'\ --data-urlencode 'password=<ENTER_PASSWORD>' Example:curl -L -X POST 'https://idcs-84d41xyz1234567890.identity.c9dev2.oc9qadev.com/oauth2/v1/token'\ -H 'Authorization: Basic MDk4ZASDFGHJKL1234556788'\ -H 'Content-Type: application/x-www-form-urlencoded; charset=utf-8'\ --data-urlencode 'scope=https://idcs-opa-ad5b921234567890.data.processautomation.oci.oc-test.com/process/v1'\ --data-urlencode 'grant_type=password'\--data-urlencode 'username=<ENTER_USERNAME>'\ --data-urlencode 'password=<ENTER_PASSWORD>'Note:
- Encode the client ID and client secret in Base64 using the format = CLIENT_ID:CLIENT_SECRET and use it as the authorization header parameter.
- Ensure that the user name and password is the same as that of the Admin Console credentials and is passed as a form parameter.
- Ensure that the scope is the same URL as added in the client configuration of the IDCS client application.
-
Get the OAuth access token from the response.

-
-
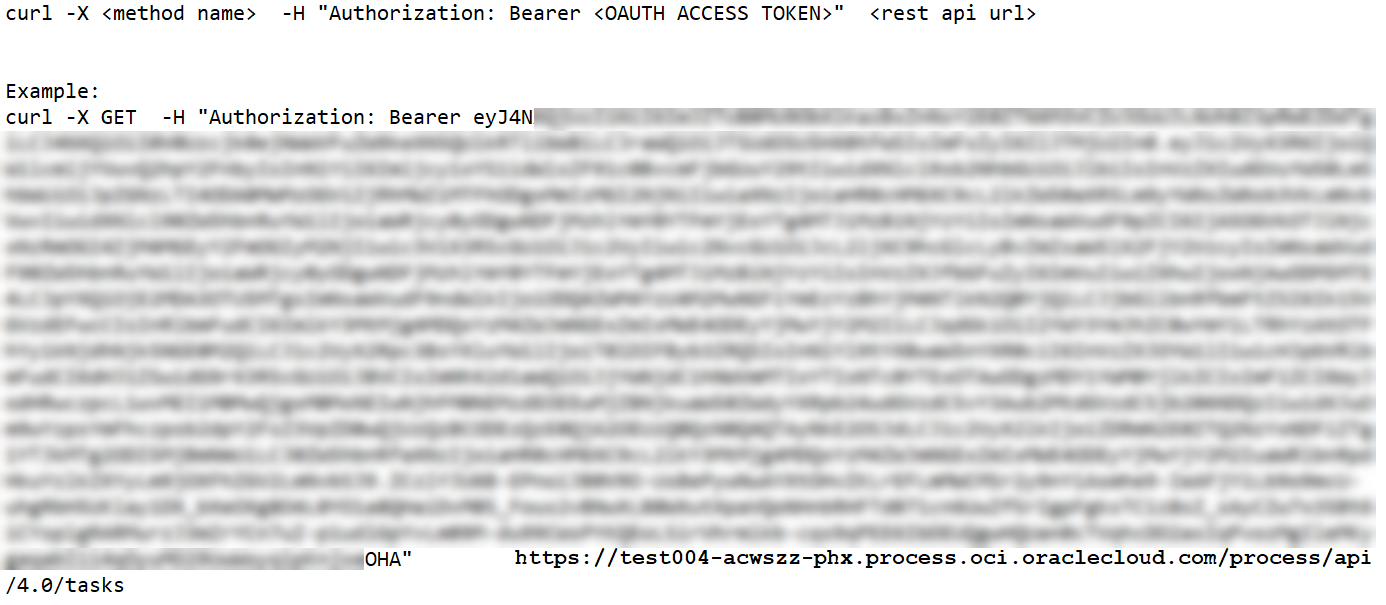
Access REST API using the OAuth access token.
You can access REST APIs in the allowed scope by using the OAuth access token in the Authorization Bearer header.