Extend Your On-Premises Network with a VCN on Oracle Cloud Infrastructure
![]() This topic does not apply to Oracle Cloud Infrastructure Classic.
This topic does not apply to Oracle Cloud Infrastructure Classic.
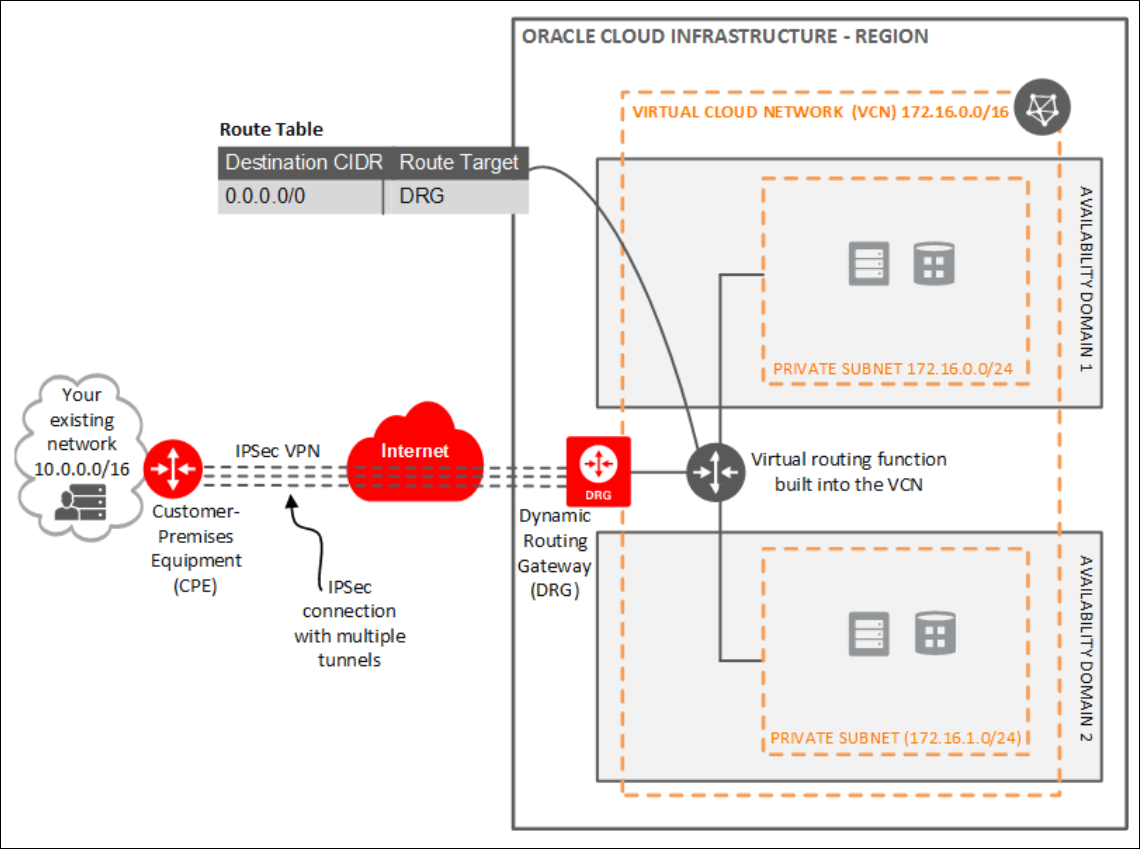
One way to connect your on-premises network and your VCN is to use an Internet Protocol Security (IPSec) VPN. IPSec is a protocol suite that encrypts the entire IP traffic before the packets are transferred from the source to the destination. This topic provides instructions for setting up and managing an IPSec VPN for your VCN for PaaS services. This topic applies to all PAAS services.
In summary, the process for creating an IPSec VPN comprises the following steps:
-
Create your VCN.
-
Create a subnet in the VCN.
-
Create a Dynamic Routing Gateway (DRG).
-
Attach the DRG to your VCN.
-
Create a Customer Premises Equipment (CPE) object and provide your router's public IP address.
-
From your DRG, create an IPSec connection to the CPE object and provide your static routes.
-
Get the IPSec tunnel information
-
Configure the IPSec connection on the remote end.
-
Create a route table and route rule for the DRG.
-
Create a security list and required rules.
-
Create PaaS Policies.
Description of the illustration ipsec_for_vcn.png