Topics:
Get Started with Oracle WebCenter Sites 12c (12.2.1.4) on Marketplace
Create and View Oracle WebCenter Sites 12c (12.2.1.4) on Marketplace Instances
Create and View Oracle WebCenter Sites Satellite Server 12c (12.2.1.4) on Marketplace Instances
Get Started with Oracle WebCenter Sites 12c (12.2.1.4) on Marketplace
Here’s information about Oracle WebCenter Sites on Marketplace that will help you get started:
About Oracle WebCenter Sites on Marketplace
Oracle WebCenter Sites on Marketplace is provided as a VM-based solution on Oracle Cloud Infrastructure.
Oracle WebCenter Sites on Marketplace is available in two types of Marketplace offerings: Paid and BYOL. See About the License for Oracle WebCenter Sites on Marketplace.
Oracle WebCenter Sites on Marketplace helps customers to provision/set up the environment in few clicks and enables to deliver WebCenter Sites solutions on cloud.
About the License for Oracle WebCenter Sites on Marketplace
Oracle WebCenter Sites on Marketplace is based on Oracle WebCenter Sites 12c (12.2.1.4). Oracle WebCenter Sites on Marketplace is available in two types of Marketplace offerings:
Paid: Use the following Oracle WebCenter Sites (Paid) listing to use Universal Credits pricing:
Oracle WebCenter Sites 12c (Paid)
BYOL: Use the Oracle WebCenter Sites (BYOL) listing to Bring Your Own License using your existing Oracle WebCenter Sites 12c (12.2.1.4) on-premises license, or you can purchase a new license for Oracle WebCenter Sites 12c (12.2.1.4).
When you activate Oracle WebCenter Sites on Marketplace using the BYOL listing, you are charged only for the Oracle Cloud Infrastructure resources consumed. You must have sufficient supported on-premises licenses as required and specified in the Service Description for Oracle PaaS.
For the processor conversion ratios and license requirements for the BYOL offering, go to the Cloud Service Descriptions page and go to the Cloud Service Description PDF. In particular, note the following conversion ratios for BYOL:
For each supported Processor license, you may activate up to 2 OCPUs of the BYOL Cloud Service.
For every 10 supported Named User Plus licenses, you may activate 1 OCPU of the BYOL Cloud Service.
About Roles and User Accounts
Oracle WebCenter Sites on Marketplace uses roles to control access to tasks and resources. A role assigned to a user gives certain privileges to the user.
Access to Oracle WebCenter Sites on Marketplace is based on the roles and users set up for the Oracle Cloud Infrastructure console. You need OCI Administrator role to provision WebCenter Sites.
For information about how to add user accounts in Oracle Cloud, see:
Add Users to a Cloud Account with Identity Cloud Service in Getting Started with Oracle Cloud.
Managing Oracle Identity Cloud Service Users and Groups in the Oracle Cloud Infrastructure Console in the Oracle Cloud Infrastructure documentation.
Create and View Oracle WebCenter Sites 12c (12.2.1.4) on Marketplace Instances
The information in this chapter will help you create and view Oracle WebCenter Sites on Marketplace instances.
Before You Begin
Before you begin, you would need to complete the following tasks and prerequisites.
Sign in to Oracle Cloud Infrastructure Console
Complete the following steps to sign in to the Oracle Cloud Infrastructure console.
Go to http://cloud.oracle.com.
Enter your cloud account name and click Next.
Sign in to the Oracle Cloud Infrastructure console:
If your cloud account uses identity domains, sign in to the Oracle Cloud Infrastructure console as a user configured in Oracle Cloud Infrastructure Identity and Access Management (IAM).
Select the domain you normally use to log in to the OCI console.
If your cloud account does not use identity domains, sign in to the Oracle Cloud Infrastructure console as a user federated through Oracle Identity Cloud Service.
Under Single Sign-On (SSO) options, note the identity provider selected in the Identity Provider field and click Continue.
Enter the user name and password provided in the welcome email, and click Sign In. The Oracle Cloud Infrastructure console is shown.
Prerequisites
You'll need to complete the following prerequisites before provisioning the WebCenter Sites stack.
Configure Dynamic Groups and Policies for Non-Admin Delegated Users - This is required only when non-admin users need to provision the stack.
Setup DNS resolver to resolve Database domain - This is required only when VCNs used for Database and WebCenter Stack pre-exist and are different.
After completing the above prerequisites, you can proceed to provision the WebCenter Sites stack.
System Requirements
You require access to the following services to use Oracle WebCenter Sites on OCI.
Identity and Access Management (IAM)
Compute, Network, Block Storage, Block Volume
Vault, Key, Secret
Resource Manager
Database
Load Balancer
Tagging
Make sure you have the following minimum limits for the services in your Oracle Cloud Infrastructure tenancy, and if necessary, request for an increase of a service limit.
| Service | Minimum Limit |
|---|---|
| Identity and Access Management (IAM) Policy | 1 |
| Compute Shape VM.Standard.E4.Flex or VM.Standard.E5.Flex | 1 |
| Virtual Cloud Network | 1 |
| Block Storage | 1 TB |
| Block Volume | 50 GB |
| Vault & Key | 1 |
| Secrets | 1 |
| Load Balancer | Flexible Load Balancer |
In Oracle Cloud Infrastructure Vault (formerly known as Key Management), a standard vault is hosted on a hardware security module (HSM) partition with multiple tenants, and it uses a more cost-efficient, key-based metric for billing purposes. A virtual private vault provides greater isolation and performance by allocating a dedicated partition on HSM. Each type of vault has a separate service limit in your Oracle Cloud Infrastructure tenancy. The limit for secrets spans all the vaults.
See Service Limits in the Oracle Cloud Infrastructure documentation.
Generate SSH key pair
See Generate an SSH Key Pair for WebCenter for generating an SSH key pair.
This SSH key pair will be used for connecting to Bastion and Compute instances after stack execution.
Note: This will be used to create DB and WebCenter Sites nodes.
Create a Compartment
If your tenancy does not already include a compartment for your Oracle WebCenter Sites on Marketplace instances, you can create a new one.
Note: To create a compartment, your administrator must first add the following policy for your group: allow group groupName to manage compartments in tenancy
To create a compartment in Oracle Cloud Infrastructure:
Open the navigation menu and click Identity & Security. Under Identity, click Compartments. A list of the existing compartments in your tenancy is displayed.
Click Create Compartment.
Enter the following:
Name: Specify a name. For example, wcs-compartment. Restrictions for compartment names are: Maximum 100 characters, including letters, numbers, periods, hyphens, and underscores. The name must be unique across all the compartments in your tenancy.
Description: A friendly description.
Parent Compartment: Select the parent compartment where you want the new compartment to be created. When the parent compartment is not selected, the new compartment is created under the root compartment.
Click Create Compartment.
Once the compartment is created, if you are not an administrator, ask your administrator to complete the following steps to grant you the permissions needed to perform the required tasks in the compartment:
Note: You can use any name (wcs-admins, wcs-compartment, and wcs-policy are examples).
Create an IAM group with the user that will do the Marketplace install.
Navigate to Identity & Security, and then Domains.
If not already selected, select the compartment where you’ll install the Marketplace product.
Click the domain where you’ll create the group.
Click Groups.
On the Create group page, provide the following information:
- Name: wcs-admins
- Description: Webcenter Sites Administrators
- Users: Add the user that will do the Marketplace installation.
Click Create.
Create a policy with the permissions to perform the required tasks in the compartment.
Navigate to Identity & Security, and then Policies.
Click Create Policy and provide a name (for example, wcs-policy).
Create a policy with the following statements.
allow group wcs-admins to manage instance-family in compartment wcs-compartment
allow group wcs-admins to manage virtual-network-family in compartment wcs-compartment
allow group wcs-admins to manage volume-family in compartment wcs-compartment
allow group wcs-admins to manage load-balancers in compartment wcs-compartment
allow group wcs-admins to manage orm-family in compartment wcs-compartment
where
wcs-adminsis the group name andwcs-compartmentis the compartment name.
Create Database
You can follow the below steps to create a new Oracle Database instance (or you can use an existing database too).
Note: Currently, Autonomous Database Serverless - Transaction Processing, Autonomous Database on Dedicated Exadata Infrastructure, Exadata Database Service on Dedicated Infrastructure, and Base Database are supported. For any additional questions, contact the Oracle Support team.
Complete the following to create a new DB service instance:
Create VCN
Complete the following to create a new DB system:
Log in to OCI Console, navigate to Networking, then to Virtual Cloud Networks.
Click Create VCN via Wizard.
Click Start VCN Wizard.
VCN name: Provide a name.
Compartment: Specify the compartment in which the VCN needs to be created.
VCN IPv4 CIDR block: Specify IPv4 CIDR block (for example, 10.0.0.0/16).
Select the Use DNS hostnames in this VCN check box.
In the Configure public subnet and Configure private subnet sections, specify the correct CIDR blocks and click Next.
Make sure to create the necessary gateways such as Internet gateway, NAT gateway, and Service gateway.
Click Create. The VCN is created.
Create a New Database
Follow the below OCI documentation links for creating OCI Database resources based on the preferred service.
Base Database (Single Node or RAC) : See Provision a Base Database Service for more information.
Autonomous Database Serverless (Transaction Processing) : See Provision an Autonomous Database Service for more information.
Autonomous Database on Dedicated Exadata Infrastructure : See Provision an Autonomous Database on Dedicated Exadata Infrastructure for more information.
Exadata Database Service on Dedicated Infrastructure: See Provision an Exadata Database Service on Dedicated Infrastructure for more information.
Create Vault Secrets
Log in to the OCI console and search for Vault, and then create a vault app.
Click Create Vault.
Provide a name and click Create Vault.
Click the vault app you created earlier. Create a master encryption key by specifying the compartment, protection mode, name, algorithm, length, and so on in the Create Key section.
Click Secrets on the left side and start adding secrets by specifying the compartment, name, key, secret type template, secret contents, and so on in the Create Secret section.
| Secret Name | Secret Description | Comment |
|---|---|---|
| wcs-admin-password | Secret for WebCenter Sites Admin Password | The Secret Contents field should be populated with the Weblogic password value. The password needs to meet the following password policy: The password must be at least 8 alphanumeric characters with at least one number or a special character. |
| db-system-sys-password | Secret for DB System SYS Password | SYS user password of DB created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Base Database. |
| db-system-ssh-private-key | Secret for DB System SSH private key | The Secret Contents field should be populated with the private key value that was used to create DB in the Create a New Database section. Required only if chosen database service is Base Database. |
| db-system-ssh-private-key-passphrase | Secret for DB System SSH private key’s passphrase | The Secret Contents field should be populated with the private key’s passphrase value that was used to create DB in the Create a New Database section. Required only if chosen database service is Base Database and Key is passphrase protected. |
| exadata-db-sys-password | Secret for Exadata Database SYS Password | SYS user password of Exadata database created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure. |
| exadata-db-ssh-private-key | Secret for Exadata Database SSH private key | The Secret Contents field should be populated with the private key value that was used to create DB in the Create a New Database section. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure. |
| exadata-db-ssh-private-key-passphrase | Secret for Exadata Database SSH private key’s passphrase | The Secret Contents field should be populated with the private key’s passphrase value that was used to create DB in the Create a New Database section. Required only if chosen database service is Exadata Database Service on Dedicated Infrastructure and Key is passphrase protected. |
| atp-db-password | Secret for Autonomous Database Admin Password | Admin user password of Autonomous database created in the Create a New Database section should be used in the Secret Contents field. Required only if chosen database service is Autonomous Database Serverless or Autonomous Database on Dedicated Exadata Infrastructure. |
| wcs-schema-password | Secret for Sites schema password. | The password needs to meet the following password policy: •The password must start with a letter. •The password must contain at least two digits. •The password must contain at least two uppercase letters. •The password must contain at least two lowercase letters. •The password must contain at least two special characters from the set [$#_]. •The password must be of at least 15 characters and maximum 30 characters in length. Example: OCI#db#456789123 |
Provision WebCenter Sites Stack
You can provision Oracle WebCenter Sites on a Marketplace instance in a selected compartment in Oracle Cloud Infrastructure.
| Note |
|---|
| In the Stack Configuration section, you can select the Quick Start check box to quickly provision a WebCenter environment using default values. See Quick Start for WebCenter for more information. |
To provision Oracle WebCenter Sites on a Marketplace instance:
Navigate to the WebCenter Sites listing on Marketplace by direct URL or by browsing in Oracle Cloud Infrastructure.
Using direct URL:
In your browser, enter https://cloudmarketplace.oracle.com/marketplace/en_US/homePage.jspx?tag=WebCenter+Sites.
The Marketplace listings for WebCenter Sites are displayed.
Click the title of the listing you want to use. The landing page of that listing is displayed.
Click Get App.
Select your Oracle Cloud Infrastructure region and click Sign In.
By browsing:
Open the navigation menu and click Marketplace. Under Marketplace, click All Applications.
In the Marketplace search field, enter WebCenter Sites. The Marketplace listings for WebCenter Sites are displayed.
Click the title of the listing you want to use and review the information on the Overview page.
Accept the terms and restrictions, and then click Launch Stack. The Create Stack wizard is displayed.
Provide information about the stack for the instance.
Stack information:
Enter name and description.
Create in Compartment: Select the compartment.
Terraform version: Specify the Terraform version and click Next.
Configure variables:
Stack Configuration
Resource Name Prefix: Enter a prefix (for example, Sites). The name of all compute and network resources will begin with this prefix. It must begin with a letter and it can contain only letters or numbers.
SSH Public key: Provide the SSH public key (created in Generate SSH key pair).
Quick Start: Select this check box to quickly provision a WebCenter Sites environment using default values. See Quick Start for WebCenter for more information.
OCI Policies: Select this check box if you need the stack to create policies to provision WebCenter Sites resources, configure Database Network, and read Vault Secrets. Deselecting this option is for Advanced users only. See Configure Dynamic Groups and Policies for Non-Admin Delegated Users for more information.
Enable Private Service: Select this check box if you need to provision service in private subnet for Fast Connect usage.
Secrets Key Management
OCI Vault compartment: Select the compartment for OCI vault.
Use pre-created OCI Vault Secrets: Select this check box if you need to use pre-created KMS Secrets. If not selected, a new KMS secret and KMS encryption key will be created in the given OCI vault. If selected, you need to pre-create vault secrets as mentioned in Create Vault Secrets.
OCI Vault to store secrets: Select the OCI vault to store new KMS secret. This option is visible when the Use pre-created OCI Vault Secrets check box is not selected.
OCI Vault to fetch secrets: Select the OCI vault to fetch pre-created KMS secrets. This option is visible when the Use pre-created OCI Vault Secrets check box is selected.
Virtual Cloud Network
If you're using an existing VCN, complete the following:
Network Compartment: Select the compartment you created earlier.
Existing WebCenter Sites Virtual Cloud Network: Select the VCN provisioned for WebCenter Sites.
If you need to use a new VCN, then select the Create the Virtual Cloud Network check box and complete the following:
Network Compartment: Select the compartment you created earlier.
Virtual Cloud Network Name: Specify a name for the new VCN to be created for this service.
Virtual Cloud Network CIDR: Specify a CIDR to assign to the new VCN.
Database Configuration:
Database Strategy: Select the type of database to use for provisioning. The supported databases are: Database System, Autonomous Transaction Processing Database, and Exadata Database.
If you selected Autonomous Transaction Processing Database as the Database Strategy, then complete the following that are displayed:
Select the value for Autonomous Database compartment.
Select the value for Autonomous Database.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
- Autonomous Database Admin Password: Provide the value for Autonomous Database Admin Password.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
- Secret for Autonomous Database Admin Password: Select the secret for Autonomous Database Admin Password.
If you selected Database System as the Database Strategy, then complete the following that are displayed:
Select the value for DB System compartment.
Select the value for DB System Instance Name.
PDB name: Provide the PDB name of the DB system.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
DB System Password: Provide the value of DB System password.
DB System SSH Private key: Upload the DB System SSH Private key which is created without passphrase.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Passphrase for DB System SSH Private key: Provide the value for DB System SSH key passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for DB System Password: Select the secret for DB system password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for DB System SSH Private key: Select the secret for DB System SSH private key.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Secret for DB System SSH Private key passphrase: Select the secret for DB System SSH private key’s passphrase.
If you selected Exadata Database as the Database Strategy, then complete the following that are displayed:
Select the value for Exadata Database compartment.
Exadata DB Home OCID: Provide the OCID of Exadata DB Home.
Select the value for Exadata Database.
Exadata Database PDB name: Provide the PDB name of the Exadata database.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Exadata Database Password: Provide the value of the PDB user password for the Exadata database.
Exadata Database SSH Private key: Upload the Exadata database SSH Private key created without passphrase.
Passphrase needed for Exadata Database SSH Private key: Check if the private key is passphrase protected.
Passphrase for Exadata Database SSH Private key: Provide the value for Exadata Database SSH key passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for Exadata Database Password: Select the secret for Exadata database password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for Exadata Database SSH Private key: Select the secret for Exadata Database SSH private key.
Passphrase needed for Exadata Database SSH Private key: Check if the private key is passphrase protected.
Secret for Exadata Database SSH Private key passphrase: Select the secret for Exadata Database SSH private key’s passphrase.
Database Schema Strategy: Select the database schema strategy to use for provisioning. The supported schema strategies are: Create New Database Schemas and Use existing Database Schemas. The option Create New Database Schemas will create new database schemas with the given schema prefix. The option Use existing Database Schemas will try to find and use existing database schemas with the given schema prefix and provisioning fails if database schemas matching the given schema prefix don’t pre-exist.
Database Schema Prefix: Provide a value for database schema prefix. It should not be longer than 11 characters and should start with a letter followed by uppercase alphabets and numeric characters.
Bastion Instance:
If you're using an existing VCN, complete the following:
Bastion Strategy: Select a bastion strategy from the drop-down list. The available options are Create New Bastion Instance, and Use Existing Bastion Instance.
If you selected Create New Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Existing Subnet for Bastion Host: Select an existing public subnet to use for a Bastion compute instance.
Bastion Host Shape: Select the appropriate Bastion host shape (keep the default value).
If you selected Use Existing Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Public IP of Bastion Instance: Provide the public IP of existing Bastion and make sure it is reachable for new WebCenter compute instances.
SSH Private Key Bastion Instance: Select the appropriate SSH Private key to access the bastion instance. This private key should not contain passphrase.
WebCenter Sites Compute Instance:
Compute Shape: Select the appropriate compute shape.
OCPU count: Select the OCPU count. The default value is 2.
If you're using an existing VCN, complete the following:
- Existing Subnet for WebCenter Sites Compute Instances: Select an existing subnet to use for WebCenter Sites compute instances.
File System:
Use Existing File System: Select this check box to use an existing File System and Mount Target.
If selected, you will need to select the compartment and availability domain of the existing File System and provide the File System OCID. The Mount Target must have security rules configured to allow traffic to the chosen VCN CIDR. See Configuring VCN Security Rules for File Storage.
File System Compartment: Choose the compartment where the WebCenter Sites stack will be created.
File System Availability Domain: Select the Availability Domain.
If you selected Use Existing File System, then complete the following that are displayed:
- Existing File System ID: Provide an existing File System OCID. The existing file system must be in the same availability domain as the existing mount target.
If you have not selected Use Existing File System, then complete the following that are displayed:
- Existing Subnet for Mount Target: Select an existing subnet to use for Mount Target.
Load Balancer:
If you're using an existing VCN, complete the following:
Existing Subnet for Load Balancer: Select an existing subnet to use for the load balancer.
Provide the value for Minimum Bandwidth for Flexible Load Balancer.
Provide the value for Maximum Bandwidth for Flexible Load Balancer.
WebCenter Sites WebLogic Domain Configuration:
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
WebCenter Sites Admin Password: Provide the value for WebCenter Sites Admin password.
WebCenter Sites Schema Password: Provide the value for WebCenter Sites Schema password.
If you have selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for WebCenter Sites Admin Password: Select the secret for WebCenter Sites administrator password.
Secret for the WebCenter Sites Schema Password: Select the secret for the WebCenter Sites schema password.
Click Next. Review all the configuration variables and then select the Run apply check box under Run apply on the created stack section. Click Create.
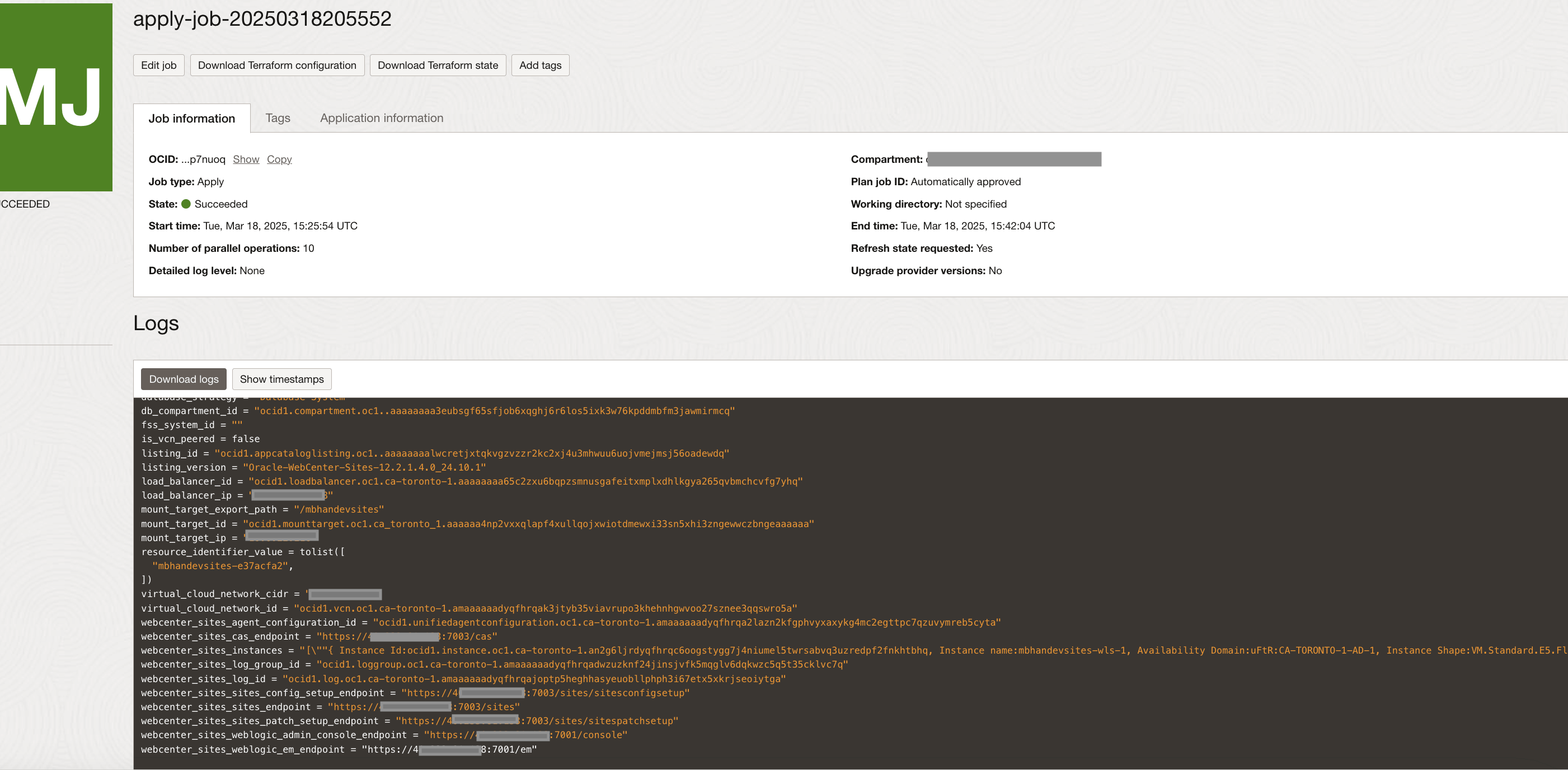
WebCenter Sites Endpoints
If everything goes as expected, then navigate to the WebCenter Sites stack and click the Application Information tab. You'll see all the provisioned end points for the services under section WebCenter Sites Endpoints:
WebCenter Sites WebLogic Administration Console:
"https://<lb-host-IP>:7001/console"WebCenter Sites Config Setup:
"https://<lb-host-IP>:7003/sites/sitesconfigsetup"WebCenter Sites Patch Setup:
"https://<lb-host-IP>:7003/sites/sitespatchsetup"WebCenter Sites:
"https://<lb-host-IP>:7003/sites"WebCenter Sites CAS:
"https://<lb-host-IP>:7003/cas"

To navigate to the WebCenter Sites stack:
In the side menu, select Developer Services, Resource Manager, and then Stacks.
Select your compartment and click the name of the WebCenter Sites stack you created.
If something goes wrong or if for any reason you want to do a clean-up of all the resources that were provisioned as part of the WebCenter Sites deployment, use Destroy Job to do the clean-up.
Set Up Load Balancer Certificate and DNS
For Oracle WebCenter Sites, See Set Up DNS and SSL Certificate for WebCenter to set up the load balancer certificate and DNS record.
Set Up WebCenter Sites Configurator
Access the WebCenter Sites Configurator URL
https://<DNS host>:7003/sites/sitesconfigsetupand click Begin.Retain the default values for WebCenter Sites Shared Directory section and click Next.
Retain the default value for Database Parameters section and click Next.
For Web Application Parameters section, specify the following and click Next:
Host name for WebCenter Sites: Specify the DNS host name.
Port number for WebCenter Sites: 7003
Are you installing over a secure connection?: Yes
For CAS Deployment Information section, specify the following and click Next:
Server host name: Specify the DNS host name.
Server port number: 7003
Server host name of internally accessible CAS: Specify the DNS host name
Server port number of internally accessible CAS: 7003
Server host name where CAS is actually deployed: DNS host name
For WebCenter Sites Administrator Accounts section, retain the default values or change the values if required, and then click Next.
For Sample Sites section, specify as needed and click Next.
In the Configuration Summary section, click Test. After the test is successful, click Start.
You'll see that the configuration is in progress. Once the configuration is completed, you'll see a message indicating that it has been completed.
Restart the WebCenter Sites server and access the WebCenter Sites URL
https://<DNS host>:7003/sites. Log in using the credentials (set in Step 6).Access
https://<DNS host>:7003/sites/sitespatchsetupand click Begin. Once the configuration is completed, you'll see a message indicating that it has been completed.Restart the WebCenter Sites server.
Set Up WebCenter Sites with Secondary cluster nodes
For Oracle WebCenter Sites, Use Scale Out operation as described in Set Up WebCenter Sites with Secondary cluster nodes to set up the secondary cluster nodes.
Set Up a WebCenter Sites Cluster
You can set up a WebCenter Sites cluster with a primary cluster node on one machine and one or more secondary cluster nodes on the same or different machines. The first WebCenter Sites managed server you create is the primary node, and any additional WebCenter Sites managed servers in the same domain are the secondary nodes.
To create a WebCenter Sites cluster:
Log in to WebCenter Sites (
https://<host-IP>:7003/sites). Navigate to Admin, System Tool, and then Cluster Management.Complete the following by choosing the Add option from the Choose Option drop-down menu:
Node name: Enter a name. For example: wcsites_server1.
Host name: The host IP address of wcsites_server1. The actual listener address of the node and not the load balancer.
Port number: 7003
Batch Host name: The IP address of the host where wcsites_server1 is running (wcsites_server1 is the dedicated batch host.)
Batch Port number: 7003
Are you installing over a secure connection?: No Click Add.
Note: The primary node wcsites_server1 must be registered first.
Complete the following for the secondary node:
Node name: Enter a name. For example: wcsites_server2.
Host name: The host IP address of wcsites_server2. The actual listener address of the node and not the load balancer.
Port number: 7003
Batch Host name: The IP address of the host where wcsites_server1 is running (wcsites_server1 is the dedicated batch host.)
Batch Port number: 7003
Are you installing over a secure connection?: No Click Add.
Create and View Oracle WebCenter Sites Satellite Server 12c (12.2.1.4) on Marketplace Instances
If you want to configure WebCenter Sites Satellite Server on Marketplace, complete the steps mentioned in this chapter. You can skip this chapter if you do not want to configure WebCenter Sites Satellite Server on Marketplace.
About the License for Oracle WebCenter Sites Satellite Server on Marketplace
Oracle WebCenter Sites Satellite Server on Marketplace is based on Oracle WebCenter Sites Satellite Server 12c (12.2.1.4). Oracle WebCenter Sites Satellite Server on Marketplace is available as a Paid offering:
Paid: Use the following Oracle WebCenter Sites Satellite Server (Paid) listing to use Universal Credits pricing:
- Oracle WebCenter Sites Satellite Server 12c (Paid)
Before You Begin
Before you begin, you would need to complete the following tasks and prerequisites.
Sign in to Oracle Cloud Infrastructure Console
Complete the following steps to sign in to the Oracle Cloud Infrastructure console.
Go to http://cloud.oracle.com.
Enter your cloud account name and click Next.
Sign in to the Oracle Cloud Infrastructure console:
If your cloud account uses identity domains, sign in to the Oracle Cloud Infrastructure console as a user configured in Oracle Cloud Infrastructure Identity and Access Management (IAM).
Select the default domain.
If your cloud account does not use identity domains, sign in to the Oracle Cloud Infrastructure console as a user federated through Oracle Identity Cloud Service.
Under Single Sign-On (SSO) options, note the identity provider selected in the Identity Provider field and click Continue.
Enter the user name and password provided in the welcome email, and click Sign In. The Oracle Cloud Infrastructure console is shown.
Prerequisites
You'll need to complete the following prerequisites before provisioning the WebCenter Sites Satellite Server stack.
After completing the above prerequisites, you can proceed to provision the WebCenter Sites Satellite Server stack.
System Requirements
You require access to the following services to use Oracle WebCenter Sites Satellite Server on OCI.
Identity and Access Management (IAM)
Compute, Network, Block Storage
Vault, Key, Secret
Resource Manager
Database
Load Balancer
Tagging
Make sure you have the following minimum limits for the services in your Oracle Cloud Infrastructure tenancy, and if necessary, request for an increase of a service limit.
| Service | Minimum Limit |
|---|---|
| Identity and Access Management (IAM) Policy | 1 |
| Compute Shape VM.Standard.E4.Flex or VM.Standard.E5.Flex | 1 |
| Virtual Cloud Network | 1 |
| Block Storage | 1 TB |
| Vault & Key | 1 |
| Secrets | 4 |
| Load Balancer | Flexible Load Balancer |
In Oracle Cloud Infrastructure Vault (formerly known as Key Management), a standard vault is hosted on a hardware security module (HSM) partition with multiple tenants, and it uses a more cost-efficient, key-based metric for billing purposes. A virtual private vault provides greater isolation and performance by allocating a dedicated partition on HSM. Each type of vault has a separate service limit in your Oracle Cloud Infrastructure tenancy. The limit for secrets spans all the vaults.
See Service Limits in the Oracle Cloud Infrastructure documentation.
Generate SSH key pair
See Generate an SSH Key Pair for WebCenter for generating an SSH key pair.
Create a Compartment
If your tenancy does not already include a compartment for your Oracle WebCenter Sites Satellite Server on Marketplace instances, you can create a new one.
Note: To create a compartment, your administrator must first add the following policy for your group: allow group groupName to manage compartments in tenancy
To create a compartment in Oracle Cloud Infrastructure:
Open the navigation menu and click Identity & Security. Under Identity, click Compartments. A list of the existing compartments in your tenancy is displayed.
Click Create Compartment.
Enter the following:
Name: Specify a name. For example, wcss-compartment. Restrictions for compartment names are: Maximum 100 characters, including letters, numbers, periods, hyphens, and underscores. The name must be unique across all the compartments in your tenancy.
Description: A friendly description.
Click Create Compartment.
Once the compartment is created, if you are not an administrator, ask your administrator to complete the following steps to grant you the permissions needed to perform the required tasks in the compartment:
Note: You can use any name (wcss-admins, wcss-compartment, and wcss-policy are examples).
Create an IAM group with the user that will do the Marketplace install.
Navigate to Identity & Security, and then Domains.
If not already selected, select the compartment where you’ll install the Marketplace product.
Click the domain where you’ll create the group.
Click Groups.
On the Create group page, provide the following information:
- Name: wcss-admins
- Description: WebCenter Sites Satellite Server Administrators
- Users: Add the user that will do the Marketplace installation.
Click Create.
Create a policy with the permissions to perform the required tasks in the compartment.
Navigate to Identity & Security, and then Policies.
Click Create Policy and provide a name (for example, wcss-policy).
Create a policy with the following statements.
allow group wcss-admins to manage instance-family in compartment wcss-compartment
allow group wcss-admins to manage virtual-network-family in compartment wcss-compartment
allow group wcss-admins to manage volume-family in compartment wcss-compartment
allow group wcss-admins to manage load-balancers in compartment wcss-compartment
allow group wcss-admins to manage orm-family in compartment wcss-compartment
where
wcss-adminsis the group name andwcss-compartmentis the compartment name.
Create Database
You can follow the below steps to create a new Oracle Database instance or you can use an existing database too.
Note: Currently Autonomous Database Serverless - Transaction Processing, Autonomous Database on Dedicated Exadata Infrastructure, Exadata Database Service on Dedicated Infrastructure & Base Database are supported. For any additional questions, contact the Oracle Support team.
Complete the following to create a new DB service instance:
Create VCN
Complete the following to create a new DB system:
Log in to OCI Console, navigate to Networking, then to Virtual Cloud Networks.
Click Create VCN via Wizard.
Click Start VCN Wizard.
VCN name: Provide a name.
Compartment: Specify the compartment in which the VCN needs to be created.
VCN IPv4 CIDR block: Specify IPv4 CIDR block (for example, 10.0.0.0/16).
Select the Use DNS hostnames in this VCN check box.
In the Configure public subnet and Configure private subnet sections, specify the correct CIDR blocks and click Next.
Make sure to create the necessary gateways such as Internet gateway, NAT gateway, and Service gateway.
Click Create. The VCN is created.
Create a new Database
Follow the below OCI documentation links for creating OCI Database resources based on the preferred service.
Base Database (Single Node or RAC) : See Provision an Base Database Service for more information.
Autonomous Database Serverless (Transaction Processing) : See Provision an Autonomous Database Service for more information.
Autonomous Database on Dedicated Exadata Infrastructure : See Provision an Autonomous Database on Dedicated Exadata Infrastructure for more information.
Exadata Database Service on Dedicated Infrastructure: See Provision an Exadata Database Service on Dedicated Infrastructure for more information.
Create Vault Secrets
Log in to the OCI console and search for Vault, and then create a vault app.
Click Create Vault.
Provide a name and click Create Vault.
Click the vault app you created earlier. Create a master encryption key by specifying the compartment, protection mode, name, algorithm, length, and so on in the Create Key section.
Click Secrets on the left side and start adding secrets by specifying the compartment, name, key, secret type template, secret contents, and so on in the Create Secret section.
| Secret Name | Secret Description | Comment |
|---|---|---|
| wcss-admin-password | Secret for WebCenter Sites Satellite Server Admin Password | The Secret Contents field should be populated with the Weblogic password value. The password needs to meet the following password policy: The password must be at least 8 alphanumeric characters with at least one number or a special character. |
| db-system-sys-password | Secret for DB System SYS Password | SYS user password of DB created in the Create a New DB System section should be used in the Secret Contents field. |
| db-system-ssh-private-key | Secret for DB System SSH private key | The Secret Contents field should be populated with the private key value that was used to create DB in the Create a New DB System section. |
| wcssat-schema-password | Secret for WebCenter Sites Satellite Server schema password. | The password needs to meet the following password policy: •The password must start with a letter. •The password must contain at least two digits. •The password must contain at least two uppercase letters. •The password must contain at least two lowercase letters. •The password must contain at least two special characters from the set [$#_]. •The password must be at least 15 characters long. Example: OCI#db#456789123 |
Provision WebCenter Sites Satellite Server
You can provision Oracle WebCenter Sites Satellite Server on a Marketplace instance in a selected compartment in Oracle Cloud Infrastructure.
To provision Oracle WebCenter Sites Satellite Server on a Marketplace instance:
Navigate to the WebCenter Sites Satellite Server listing on Marketplace by direct URL or by browsing in Oracle Cloud Infrastructure.
Using direct URL:
In your browser, enter https://cloudmarketplace.oracle.com/marketplace/en_US/homePage.jspx?tag=WebCenter+Sites+Satellite+Server.
The Marketplace listings for WebCenter Sites Satellite Server are displayed.
Click the title of the listing you want to use. The landing page of that listing is displayed.
Click Get App.
Select your Oracle Cloud Infrastructure region and click Sign In.
By browsing:
Open the navigation menu and click Marketplace. Under Marketplace, click All Applications.
In the Marketplace search field, enter WebCenter Sites Satellite Server.
The Marketplace listings for WebCenter Sites Satellite Server are displayed.
Click the title of the listing you want to use and review the information on the Overview page.
Accept the terms and restrictions, and then click Launch Stack. The Create Stack wizard is displayed.
Provide information about the stack for the instance.
Stack information:
Enter name and description.
Create in Compartment: Select the compartment.
Terraform version: Specify the Terraform version and click Next.
Configure variables:
Stack Configuration
Resource Name Prefix: Enter a prefix (for example, Sites). The name of all compute and network resources will begin with this prefix. It must begin with a letter and it can contain only letters or numbers.
SSH Public key: Provide the SSH public key (created in Generate SSH key pair).
Quick Start: Select this check box to quickly provision a WebCenter Sites environment using default values. See Quick Start for WebCenter for more information.
OCI Policies: Select this check box if you need the stack to create policies to provision WebCenter Sites resources, configure Database Network, and read Vault Secrets. Deselecting this option is for Advanced users only. See Configure Dynamic Groups and Policies for Non-Admin Delegated Users for more information.
Enable Private Service: Select this check box if you need to provision service in private subnet for Fast Connect usage.
Secrets Key Management
OCI Vault compartment: Select the compartment for OCI vault.
Use pre-created OCI Vault Secrets: Select this check box if you need to use pre-created KMS Secrets. If not selected, a new KMS secret and KMS encryption key will be created in the given OCI vault. If selected, you need to pre-create vault secrets as mentioned in Create Vault Secrets.
OCI Vault to store secrets: Select the OCI vault to store new KMS secret. This option is visible when the Use pre-created OCI Vault Secrets check box is not selected.
OCI Vault to fetch secrets: Select the OCI vault to fetch pre-created KMS secrets. This option is visible when the Use pre-created OCI Vault Secrets check box is selected.
Virtual Cloud Network
If you're using an existing VCN, complete the following:
Network Compartment: Select the compartment you created earlier.
Existing WebCenter Sites Virtual Cloud Network: Select the VCN provisioned for WebCenter Sites.
If you need to use a new VCN, then select the Create the Virtual Cloud Network check box and complete the following:
Network Compartment: Select the compartment you created earlier.
Virtual Cloud Network Name: Specify a name for the new VCN to be created for this service.
Virtual Cloud Network CIDR: Specify a CIDR to assign to the new VCN.
Database Configuration:
Database Strategy: Select the type of database to use for provisioning. The supported databases are: Database System, Autonomous Transaction Processing Database, and Exadata Database.
If you selected Autonomous Transaction Processing Database as the Database Strategy, then complete the following that are displayed:
Select the value for Autonomous Database compartment.
Select the value for Autonomous Database.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
- Autonomous Database Admin Password: Provide the value for Autonomous Database Admin Password.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
- Secret for Autonomous Database Admin Password: Select the secret for Autonomous Database Admin Password.
If you selected Database System as the Database Strategy, then complete the following that are displayed:
Select the value for DB System compartment.
Select the value for DB System Instance Name.
PDB name: Provide the PDB name of the DB system.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
DB System Password: Provide the value of DB System password.
DB System SSH Private key: Upload the DB System SSH Private key which is created.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Passphrase for DB System SSH Private key: Provide the value for DB System SSH key passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for DB System Password: Select the secret for DB system password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for DB System SSH Private key: Select the secret for DB System SSH private key.
Passphrase needed for DB System SSH Private key: Check if the private key is passphrase protected.
Secret for DB System SSH Private key passphrase: Select the secret for DB System SSH private key’s passphrase.
If you selected Exadata Database as the Database Strategy, then complete the following that are displayed:
Select the value for Exadata Database compartment.
Exadata DB Home OCID: Provide the OCID of Exadata DB Home.
Select the value for Exadata Database.
Exadata Database PDB name: Provide the PDB name of the Exadata database.
Exadata Database PDB User: Leave the value 'sys' as is. Do not change this user name.
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Exadata Database Password: Provide the value of the PDB user password for the Exadata database.
Exadata Database SSH Private key: Upload the Exadata database SSH Private key created without passphrase.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for Exadata Database Password: Select the secret for Exadata database password. When defining the secret key, you must have specified a user-friendly name for each secret. Use the same name here so that it is easy.
Secret for Exadata Database SSH Private key: Select the secret for Exadata Database SSH private key.
Database Schema Strategy: Select the database schema strategy to use for provisioning. The supported schema strategies are: Create New Database Schemas and Use existing Database Schemas. The option Create New Database Schemas will create new database schemas with the given schema prefix. The option Use existing Database Schemas will try to find and use existing database schemas with the given schema prefix and provisioning will fail if database schemas matching the given schema prefix don’t pre-exist.
Database Schema Prefix: Provide a value for database schema prefix. It should not be longer than 12 characters and should start with a letter followed by uppercase alphabets and numeric characters.
Bastion Instance:
If you're using an existing VCN, complete the following:
Bastion Strategy: Select a bastion strategy from the drop-down list. The available options are Create New Bastion Instance, and Use Existing Bastion Instance.
If you selected Create New Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Existing Subnet for Bastion Host: Select an existing public subnet to use for a Bastion compute instance.
Bastion Host Shape: Select the appropriate Bastion host shape (keep the default value).
If you selected Use Existing Bastion Instance as the Bastion Strategy, then complete the following that are displayed:
Public IP of Bastion Instance: Provide the public IP of existing Bastion and make sure it is reachable for new WebCenter compute instances.
SSH Private Key Bastion Instance: Select the appropriate SSH Private key to access the bastion instance. This private key should not contain passphrase.
WebCenter Sites Satellite Server Compute Instance:
Compute Shape: Select the appropriate compute shape.
OCPU count: Select the OCPU count. The default value is 2.
Existing Subnet for WebCenter Sites Satellite Server Compute Instances: If you're using an existing VCN, Select an existing subnet to use for WebCenter Sites Satellite Server compute instances.
Load Balancer:
Existing Subnet for Load Balancer: If you're using an existing VCN, Select an existing subnet to use for the load balancer.
Provide the value for Minimum Bandwidth for Flexible Load Balancer.
Provide the value for Maximum Bandwidth for Flexible Load Balancer.
WebCenter Sites Satellite Server WebLogic Domain Configuration:
If you have not selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
WebCenter Sites Satellite Server Admin Password: Provide the value for WebCenter Content Admin password.
WebCenter Sites Satellite Server Schema Password: Provide the value for WebCenter Content Schema password.
If you selected Use pre-created OCI Vault Secrets, then complete the following that are displayed.
Secret for WebCenter Sites Satellite Server Admin Password: Select the secret for WebCenter Sites Satellite Server administrator password.
Secret for the WebCenter Sites Satellite Server Schema Password: Select the secret for the WebCenter Sites Satellite Server schema password.
Click Next. Review all the configuration variables and then select the Run apply check box under Run apply on the created stack section. Click Create.
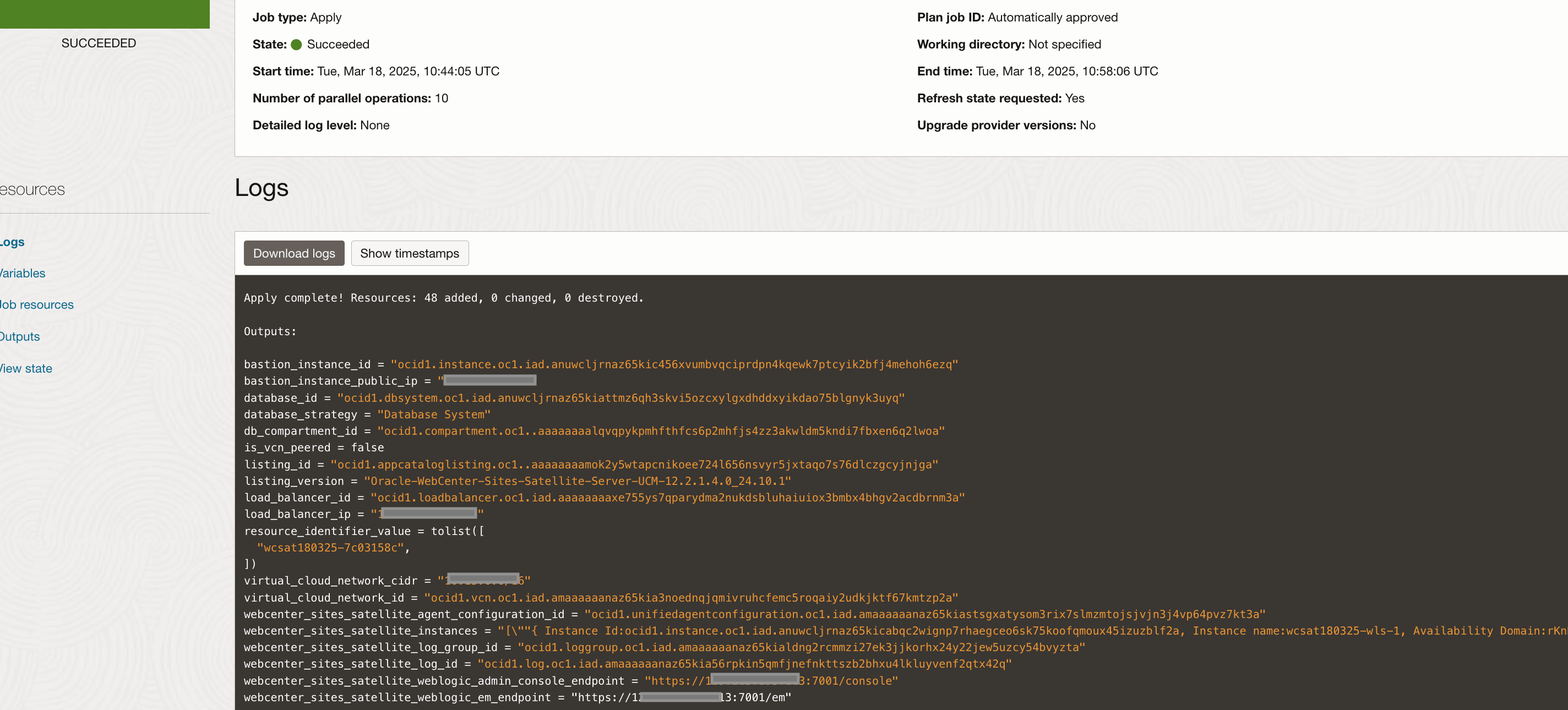
WebCenter Sites Satellite Server Endpoints
If everything goes as expected, then navigate to the WebCenter Sites Satellite Server stack and click the Application Information tab. You'll see all the provisioned end points for the services under section WebCenter Sites Satellite Server Endpoints:
WebCenter Sites Satellite Server WebLogic Administration Console:
"https://<lb-host-IP>:7001/console"WebCenter Sites Satellite Server WebLogic EM:
"https://<lb-host-IP>:7001/em"
To navigate to the WebCenter Sites Satellite Server stack:
In the side menu, select Developer Services, Resource Manager, and then Stacks.
Select your compartment and click the name of the WebCenter Sites Satellite Server stack you created.
Note: If provisioning fails, check the log at: /u01/data/domains/logs/provisioning.log.
After the stack is created, complete the following steps:
Connect to the bastion instance as the opc user.
ssh -i path_to_private_key opc@bastion_public_ipConnect to the weblogic admin server compute instance which has a name ending with ‘wls-1’.
ssh -i path_to_private_key opc@compute_wls-1_private_ipChange to ‘oracle’ user.
[opc@**-wls-1 ~]$ sudo su - oracleUpdate the values for the following properties in the file
wcs_satelliteserver_properties_bootstrap.iniat the location:/u01/data/domains/wcs_domain/wcsites/satelliteserver/config.oracle.wcsites.hostname ### associated WebCenter Sites DNS host name oracle.wcsites.portnumber ### associated WebCenter Sites port number(Default is 7003) oracle.wcsites.system.admin.user ### associated WebCenter Sites user name oracle.wcsites.system.admin.password ### associated WebCenter Sites password oracle.wcsites.cas.portnumber ### associated WebCenter Sites port number(Default is 7003) oracle.wcsites.cas.internal.hostname ### associated WebCenter Sites DNS host name oracle.wcsites.cas.internal.portnumber ### associated WebCenter Sites port number(Default is 7003) oracle.wcsites.satelliteserver.user ### satellite server user name oracle.wcsites.satelliteserver.password ### satellite server passwordExecute the following command to run the configuration of the satellite server in silent mode:
java -jar /u01/app/oracle/middleware/wcsites/satelliteserver/satellite-configurator.jar \ -silent /u01/data/domains/wcs_domain/wcsites/satelliteserver/config ############### Example Output: SatelliteServer config directory will be configured at: /u01/data/domains/wcs_domain/wcsites/satelliteserver/config/ Satellite Server Configuration is successful. Please complete Web Application Deployment steps and Start application server.Start the satellite server using Weblogic Admin Console. (
https://<Host IP>:7003/ss/cachetool/inventory.jsp).Tail the following out file and make sure that the server starts without any issue:
tail -f /u01/data/domains/logs/satellite_server1/satellite_server1.outAlso tail the sites log, to make sure that the registration is successful.
tail -f /u01/data/domains/wcs_domain/servers/satellite_server1/logs/sites.logThe log information in the sites log for successful registration should look similar to the following:
[2024-03-19T13:57:41.949+00:00] [satellite_server1] [NOTIFICATION] [] [oracle.wcsites.rest.registration] [tid: 28] [userId: <anonymous>] [ecid: 319dd37c-3332-4da6-9ab2-03325e5a9726-00000006,0] [APP: satelliteserver] [partition-name: DOMAIN] [tenant-name: GLOBAL] [SatelliteServerRegistrationImpl] Registration successful with id : 1700061855642
Using Oracle WebCenter Sites 12c (12.2.1.4) on Marketplace in Oracle Cloud Infrastructure
G10780-13
Last updated: June 2025
Copyright © 2025, Oracle and/or its affiliates.
Primary Author: Oracle Corporation