Options for System Security
Implement application security options on the Manage System Security Options page. You can set the application security to align with your company's security policy.
You can set security options for encryption and tokenization of credit cards and bank accounts, as well as for masking the payment instrument. Both funds capture and disbursement processes use security options.
Ask yourself these security questions to improve the security of your sensitive data:
-
Which security practices do I want to employ?
-
Do I want to tokenize my credit card data?
-
Do I want to encrypt my bank account data?
-
Do I want to encrypt my credit card data?
-
How frequently do I want to rotate the master encryption key and the subkeys?
-
Do I want to mask credit card and bank account numbers? How do I accomplish that?
To set up application security options, go to Financials > Payments > Manage System Security Options in the Setup and Maintenance work area.
Best Security Practices
These actions are considered best security practices for payment processing:
-
Comply with the Payment Card Industry Data Security Standard (PCI DSS). PCI DSS is the security standard required for processing most types of credit cards.
-
Comply with all requirements for accepting credit card payments.
-
Minimize the risk of exposing sensitive customer data.
-
-
Create the master encryption key.
-
Rotate the master encryption key periodically.
-
Implementation Process of Master Encryption Key and Encryption
Before you can enable encryption for credit card or bank account data, you must automatically create a master encryption key. Oracle Platform Security Services stores your master encryption key. The application uses your master encryption key to encrypt your sensitive data.
Automatic creation of the master encryption key ensures that it's created and stored in the proper location and with all necessary permissions.
Credit Card Tokenization
If you tokenize your credit card data, you're complying with PCI DSS requirements. PCI DSS requires companies to use payment applications that are PCI DSS compliant.
Tokenization is the process of replacing sensitive data, such as credit card data, with a unique number, or token, that isn't considered sensitive. The process uses a third-party payment system that stores the sensitive information and generates tokens to replace sensitive data in the applications and database fields. Unlike encryption, tokens can't be mathematically reversed to derive the actual credit card number.
Click Edit Tokenization Payment System on the Manage System Security Options page to set up your tokenization payment system. Then, click Tokenize in the Credit Card Data section to activate tokenization for credit card data.
Credit Card Data Encryption
You can encrypt your credit card data to assist with your compliance of cardholder data protection requirements with these initiatives:
-
Payment Card Industry Data Security Standard
-
Visa's Cardholder Information Security Program
Credit card numbers entered in Oracle Receivables and Oracle Collections are automatically encrypted. Encryption is based on the credit card encryption setting you specify on the Manage System Security Options page.
Bank Account Data Encryption
You can encrypt your supplier and customer bank account numbers.
Bank account encryption doesn't affect internal bank account numbers. Internal bank accounts are set up in Cash Management. They are used as disbursement bank accounts in Payables and as remit-to bank accounts in Receivables.
Supplier, customer, and employee bank account numbers entered in Oracle applications are automatically encrypted. Encryption is based on the bank account encryption setting you specify on the Manage System Security Options page.
Master Encryption Key and Subkey Rotation
For payment instrument encryption, Payments uses a chain key approach. The chain key approach is used for data security where A encrypts B and B encrypts C. In Payments, the master encryption key encrypts the subkeys and the subkeys encrypt the payment instrument data. This approach enables easier rotation of the master encryption key.
The master encryption key is stored on Oracle Platform Security Services. Oracle Platform Security Services stores data in an encrypted format. The master encryption key can be rotated, or generated, which also encrypts subkeys, but doesn't result in encrypting the bank account numbers again.
If your installation has an existing master encryption key, click Rotate to automatically generate a new one.
You can also select the frequency with which new subkeys are automatically generated, based on usage or on the maximum number of days. To specify a subkey rotation policy, click Edit Subkey Rotation Policy.
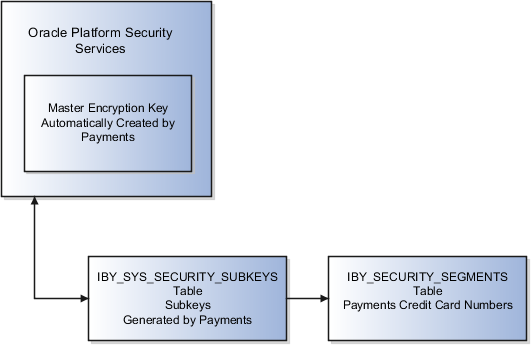
The security architecture for credit card data and bank account data encryption is composed of these components:
-
Oracle Platform Security Services
-
Payments master encryption key
-
Payments subkeys
-
Sensitive data encryption and storage
This figure illustrates the security architecture of the Oracle Platform Security Services repository, the master encryption key, and the subkeys.
Credit Card and Bank Account Number Masking
Payments serves as a payment data repository for customer and supplier information. It stores all of the customer and supplier payment information and their payment instruments, such as credit cards and bank accounts. It provides data security by letting you mask bank account numbers.
On the Manage System Security Options page, you can mask credit card numbers and external bank account numbers. You just have to select the number of digits to mask and display. For example, a bank account number of XX558012 displays the last six digits and masks all the rest. These settings specify masking for payment instrument numbers in the user interfaces of multiple applications.