Use JSON Web Token for Authorization
JSON Web Token (JWT) is a compact token format that lets you authorize yourself. A JWT has the username and the expiration period for the token, and is passed by your REST client application to Oracle B2C Service Knowledge Advanced REST APIs. Note that JWT is only a way to share username to the server, but not a way to authenticate the user. You get the JWT from your client application and it's a Base64url encoded value.
Here's a sample response with the JWT.
{
"sub": "webUser",
"aud": [
"/km/api/latest/",
"/srt/api/latest/"
],
"nbf": 1559280669,
"user_type": "CONTACT",
"iss": "http://www.exampleidp.com",
"tok_type": "AT",
"exp": 1559367069,
"iat": 1559280669,
"jti": "eb4c532c-2772-4857-9e5a-8102eb5b2931"
}The following claims are required which are used for validation:
- sub (subject)
The user login value.
- aud (audience)
The recepients of the JWT. The claim value can of the following:
- /km/api/latest/
- /srt/api/latest/
- iss(issuer)
The URL of the Oracle Identity Cloud Service or external identity provider. This value must match the value provided in the OAuth Identity Provider URL for validating OAuth token textbox.
- tok_type
The custom claim that identifies the token type. The value must be "AT".
- user_type
The custom claim that identifies the type of the user. The value can be either "CONTACT" or "ACCOUNT". The default value is "ACCOUNT". This claim is optional.
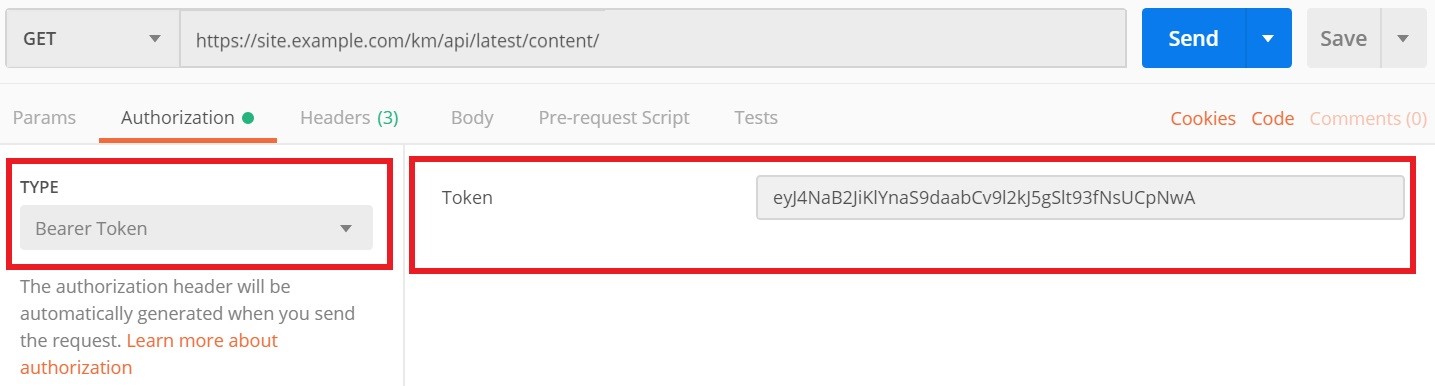
When passing a JWT in a REST client such as Postman, you must select the Authorization Type as Bearer Token and enter the token value in the Token field, as shown in this screenshot: