Guidelines for Securing Person Records
This topic describes ways of securing access to both public and managed person records. The recommended approaches minimize administration and improve security performance.
Securing Public Person Records
Public person records are those that all workers must access in a worker directory, for example. Use the View All Workers predefined security profile to provide this access. View All Workers provides access to:
-
Employees, contingent workers, nonworkers, and pending workers with currently active or suspended assignments
-
The signed-in user's own record
-
Shared person information
View All Workers doesn't provide access to future-dated person records.
Securing Person Records by Manager Hierarchy
Managers must access the person records of the workers in their manager hierarchies. To provide this access, you secure person records by manager hierarchy. Use the predefined View Manager Hierarchy security profile wherever possible. This table summarizes the View Manager Hierarchy security profile. The values shown here are also the default values for these fields.
|
Field |
Value |
|---|---|
|
Person or Assignment Level |
Person |
|
Maximum Levels in Hierarchy |
No maximum |
|
Manager Type |
Line Manager |
|
Hierarchy Content |
Manager Hierarchy |
View Manager Hierarchy includes shared person information but not future-dated person records.
For nonstandard requirements, create person security profiles. For example, if your enterprise has a custom Project Manager job role, then you can create a security profile for that manager type. Include it in an HCM data role and provision that role to all users who have the Project Manager job role.
Securing Person Records by Area of Responsibility
When you secure person records by area of responsibility, the set of records that a user can access is calculated dynamically. The calculation is based on the user's assigned areas of responsibility. This approach has several advantages:
-
It reduces the number of person security profiles and HCM data roles that you must manage.
-
It improves security performance.
-
You don't have to update security profiles when responsibilities change.
For example, consider the human resource (HR) specialists shown in this table. They perform the same job role but for workers in different business units.
|
HR Specialist |
Job Role |
Business Unit |
|---|---|---|
|
Fen Lee |
Human Resource Specialist |
USA1 BU |
|
John Gorman |
Human Resource Specialist |
USA2 BU |
|
Jenna Markum |
Human Resource Specialist |
USA3 BU |
To provide access to person records in each business unit, you:
-
Define an area of responsibility for each HR specialist, where the scope of responsibility is the relevant business unit.
-
Create a single person security profile that restricts access by area of responsibility and where Scope of Responsibility is Business unit.
-
Create a single HCM data role to include the person security profile and assign it to all three HR specialists.
This figure summarizes the approach.
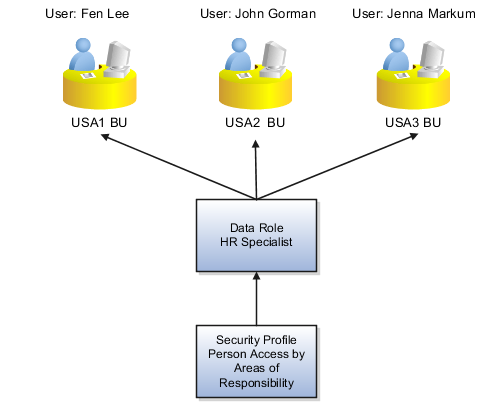
When you secure access to person records by area of responsibility, the user doesn't see all of the worker's assignments. Instead:
-
For current workers, authorized users can see current and suspended assignments only. Access to terminated assignments, such as those that were active before a global transfer, is prevented.
-
For terminated workers, authorized users can see the most recently terminated assignment only.
You can also include up to three exclusion rules. These rules exclude selected person records from the set of records that the security profile identifies.
Securing Access to Imported Candidates
You can secure access to the records of candidates imported from Oracle Talent Acquisition Cloud. Set the Purpose field in the Basic Details section of the person security profile to one of these values:
-
Imported Candidate Access
-
Person and Imported Candidate Access
You can secure access to imported candidates by either area of responsibility or manager hierarchy.
The Purpose field is available only if the Recruiting Integration enterprise option is set to one of these values:
-
Integrated with Oracle Integration Cloud
-
Fixed and Integrated with Oracle Integration Cloud
Otherwise, the Purpose field doesn't appear.