How You Preview HCM Data Security
On occasion, users may report problems with accessing secured data, such as person and organization records. As users typically have multiple roles, diagnosing these problems can be challenging. To help you with this task, you can use the Preview HCM Data Security interface.
Using this interface, you can analyze a user's data access based on all of their current roles and areas of responsibility. This topic explains how to use the Preview HCM Data Security interface in the Workforce Structures work area.
Identifying the User
To start your analysis, you search for and select the user name. When you select the user, the following sections of the page are populated automatically.
|
Page Section |
Section Contents |
|---|---|
|
Currently Assigned Roles |
The job, abstract, and data roles that the user currently inherits directly. This section also identifies security profiles assigned to those roles. |
|
Currently Assigned Areas of Responsibility |
Details of the user's areas of responsibility, if any. You need this information when investigating access to person or position records if that access is secured by area of responsibility. |
|
Session-Based Roles |
The roles associated with the user's latest session. Both directly and indirectly inherited roles are listed. |
The user must have signed in at least once, as this information is taken from the user's latest session.
Identifying the Privileges
Most data-access problems are of one of the following types:
-
The user expects to access an instance of a secured object, such as a person record, but the record isn't found.
-
The user expects to perform an action, such as Promote Worker, but the action isn't available.
-
The user can access an instance of a secured object, such as a person record, but the record should not be accessible.
-
The user can perform an action, such as Promote Worker, but the action should not be available.
To investigate these types of problems, start by identifying what the user was trying to do. For example, the user may have found the required person record but couldn't select the Promote Worker action. You then identify the data security privilege and data resource that control this access. If you know the names of the data security privilege and data resource, then you can select them in the Access Based on Privilege section. Alternatively, you can search for the associated data security policy by aggregate privilege name, for example. When you select a value in the search results, the Privilege and Data Resource fields are completed automatically.
Previewing Access
When the fields in the Access Based on Privilege section are complete, you click Preview Access. The Access Verification section of the page is updated automatically to identify every instance of the data security policy that's granted to the user. In the Verify Access For field, you select the secured record that's the subject of this investigation and click Verify. For example, you select the person record of the person the user couldn't promote. The section is updated automatically to show:
-
The roles to which the data security policy is granted, and how the user inherits those roles
-
The security profiles, if any, assigned to those roles
-
Whether the roles make the record or action accessible to the user
This figure shows typical content of the Access Verification section.
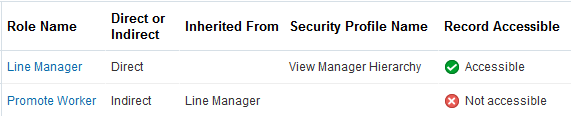
When you click an instance of the role name in the Access Verification section, you see data security policy details, including the SQL predicate. The information provided by all sections of the Preview HCM Data Security page should be sufficient for you to diagnose and resolve most data-access issues.