Role-Based Security
In Oracle Fusion Applications, users have roles through which they gain access to functions and data. Users can have any number of roles.
In this figure, user Lynda Jones has three roles.
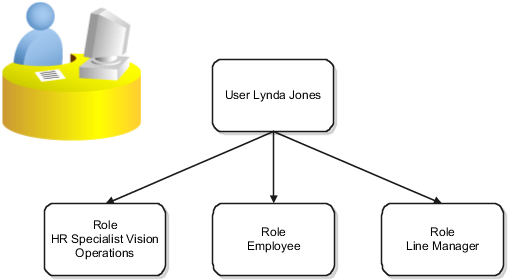
When Lynda signs in to Oracle Human Capital Management Cloud (Oracle HCM Cloud), she doesn't have to select a role. All of these roles are active concurrently.
The functions and data that Lynda can access are determined by this combination of roles.
-
As an employee, Lynda can access employee functions and data.
-
As a line manager, Lynda can access line-manager functions and data.
-
As a human resource specialist (HR specialist), Lynda can access HR specialist functions and data for Vision Operations.
Role-Based Access Control
Role-based security in Oracle Fusion Applications controls who can do what on which data.
This table summarizes role-based access.
|
Component |
Description |
|---|---|
|
Who |
Is a role assigned to a user |
|
What |
Is a function that users with the role can perform |
|
Which Data |
Is the set of data that users with the role can access when performing the function |
This table provides some examples of role-based access.
|
Who |
What |
Which Data |
|---|---|---|
|
Line managers |
Can create performance documents |
For workers in their reporting hierarchies |
|
Employees |
Can view payslips |
For themselves |
|
Payroll managers |
Can report payroll balances |
For specified payrolls |
|
HR specialists |
Can transfer workers |
For workers in specified organizations |