SAML SSO Authentication for Control Center
Overview
The Oracle CrowdTwist platform offers SAML Single Sign-On Authentication for Control Center users (program administrators). With this, a Control Center user can authenticate via their corporate account, rather than a Control Center password. Not only does this remove the need to manage another password, but access to CrowdTwist is now gated by a corporate account (if the corporate account is disabled, Control Center access is blocked).
Note: SAML is available only for authentication; an account with the same identifier (email address) must already be setup in Control Center with desired permissions.
Configuration Details
For SAML SSO Authentication to function, the client must configure CrowdTwist as an approved connection within their Single Sign-On application configuration. For this, CrowdTwist provides metadata details:
Metadata API Endpoint:
- https://[environment]control-center.crowdtwist.com/v2/sso/saml/metadata?siteId=2&clientId=[client_id]
Metadata Configuration Values:
|
Name |
Format |
Notes |
|
entityID |
https://[environment]control-center.crowdtwist.com/v2/sso/saml |
This is optional, for identification purposes. |
|
AssertionConsumerService |
https://[environment]control-center.crowdtwist.com/v2/sso/saml/login?siteId=2&clientId=[client_id] |
This is the login page or ACS. |
|
NameIDFormat |
urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress |
Login depends on the client passing the user's email address (not necessary in UI).
NameId Format must equal to urn:oasis:names:tc:SAML:1.1:nameid-format:emailAddress AND/OR an email attribute field with the name as emailAddress.
|
|
Attribute |
Name="emailAddress" |
Not required if the client passes the email as the NameID. |
|
Public Certificate |
On the metadata page, under <ds:X509Certificate> |
|
|
SingleLogoutService |
https://control-center.crowdtwist.com/v2/sso/saml/logout?siteId=2&clientId=<client_id> |
This is our logout page, could be optional. |
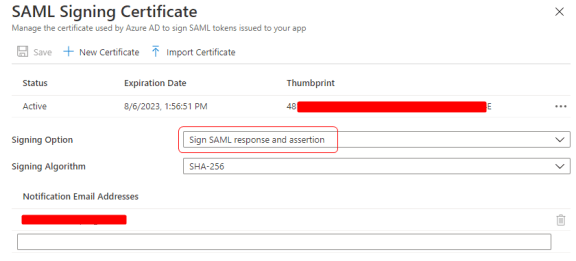
Note: Within the SSO Configuration, be sure to enable signing of the SAML Response & Assertion. Recommended algorithm: SHA-246.
Configuration Process
- Client configures their SAML SSO Application with details from above.
- Client provides Oracle CrowdTwist team with the following:
- An issuer URI (normally client's SAML metadata page)
- Clients public x509 certificate in the .pem file
- Login URL (Client’s AssertionConsumerServiceURL)
- Logout URL (Client’s SingleLogoutService)
- Oracle CrowdTwist configures SAML SSO Authentication with provided values.
- Client or Oracle CrowdTwist creates a new member configured with SSO Login Type for testing.
- Once SAML Authentication is configured and tested, existing members can be converted to SAML Authentication via the "Edit Control Center User" page in your instance
Note: The new SAML users’ emails must match the email address that is sent from the client’s SAML SSO setup.
Login Process
- Navigate to CrowdTwist Control Center login page.
- Click on SSO account.
- Enter [SAML user's email address] into the Email field.
- Click Continue.
- You will be redirected to the client’s corporate SSO login site.
- Login with your corporate SSO account.
- Click Sign In.
- Redirect back to CrowdTwist Control Center.
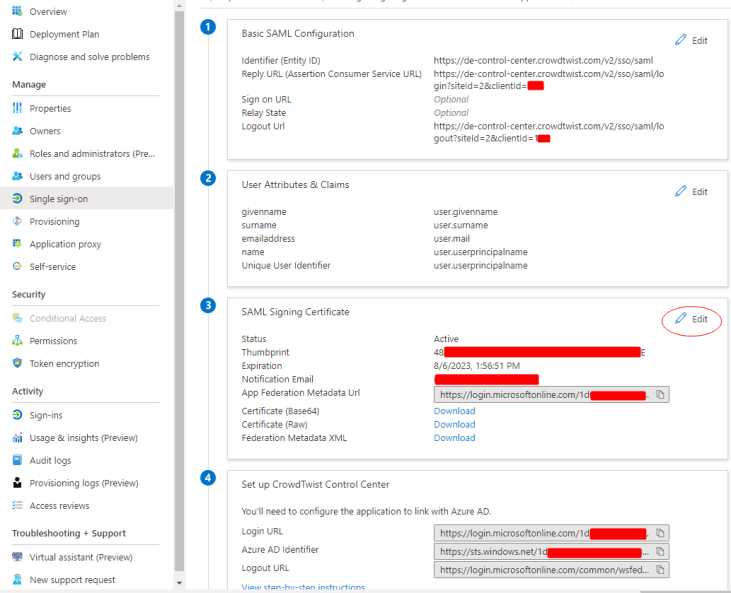
Hint: The following screenshots may be helpful when configuring for Microsoft Azure AD.
Microsoft Azure "Single sign-on" page
Microsoft Azure "SAML Signing Certificate" page