Single sign-on guidelines
Note: Third-party single sign-on (SSO) is an optional feature. If you would like to enable it for your account or have questions about it, contact My Oracle Support (MOS).
If enabled for your account, you can set up SSO between Oracle Maxymiser and a third-party SAML 2.0 identity provider (IdP). Once implemented, Maxymiser acts as a SAML service provider (SP) to trust authentication from your IdP. Your users gain access to Maxymiser with their SSO credentials or access it automatically if they are already logged in via SSO.
Establishing trust between Maxymiser and your SAML IdP partner
- Oracle Maxymiser supports an SP-initiated login flow. An IdP-initiated flow is not supported.
- An unsigned authentication request (
AuthnRequest) is sent via HTTP redirect binding. - Maxymiser uses an X.509 certificate to validate the SAML assertion issued by your IdP.
- Your IdP sends a metadata file that includes the following:
- IdP entity ID
- IdP endpoint URL to which the AuthnRequest is sent (
SingleSignOnService location) - IdP signing public certificate (
X509Certificate)
- Your IdP needs the following from Maxymiser:
- Issuer's
entityID, which varies based on the instance:- US: https://ui-us.maxymiser.com
- EMEA: https://ui-eu.maxymiser.com
- Assertion consumer service URL
- US: https://ui-us.maxymiser.com/Auth/PartnerLogin
- EMEA: https://ui-eu.maxymiser.com/Auth/PartnerLogin
- Issuer's
- Name ID format:
urn:oasis:names:tc:SAML:1.1:nameid-format:unspecifiedSample SP metadata using the correct issuer and consumer service URL:
<?xml version="1.0"?>
<md:EntityDescriptor xmlns:md="urn:oasis:names:tc:SAML:2.0:metadata" validUntil="2019-04-14T15:19:52Z"
cacheDuration="PT1464794392S" entityID="https://ui-us.maxymiser.com">
<md:SPSSODescriptor AuthnRequestsSigned="false" WantAssertionsSigned="true" protocolSupportEnumeration="urn:oasis:names:tc:SAML:2.0:protocol">
<md:NameIDFormat>urn:oasis:names:tc:SAML:1.1:nameid-format:unspecified</md:NameIDFormat>
<md:AssertionConsumerService Binding="urn:oasis:names:tc:SAML:2.0:bindings:HTTP-REDIRECT" Location=https://ui-us.maxymiser.com/Auth/PartnerLogin index="1" isDefault="true"/>
</md:SPSSODescriptor>
</md:EntityDescriptor>Setting up SSO
To set up SSO for your account:
- Contact My Oracle Support (MOS) to request SSO for a specific Maxymiser account.
- Provide MOS with your IdP's metadata and its account details. Oracle Maxymiser configures SSO for your account.
- An account administrator enables SSO settings for users.
- Users log in to Maxymiser via SSO by accessing the following URL
- US:
https://ui-us.maxymiser.com/?partner=%{IdpDomain}% - EMEA:
https://ui-eu.maxymiser.com/?partner=%{IdpDomain}%
Where
{IdpDomain}is replaced with the IdP's domain - US:
Enabling SSO for a user
Account administrators can enable SSO for each user by editing the user, selecting the SSO partner (IdP), and specifying the precise partner user identity for the user, such as their email address.
Important: Native Maxymiser authentication and SSO are mutually exclusive. Once SSO is enabled for a user, they can no longer log in to Maxymiser using their Maxymiser credentials.
To enable SSO for a user:
- In Oracle Maxymiser, click the navigator
 and select Admin
and select Admin  . The Admin tab is displayed.
. The Admin tab is displayed. - Click the Users. The Users page is displayed.
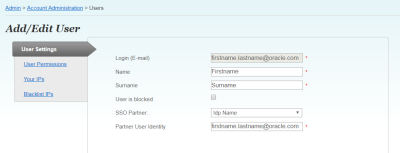
- Locate the user in the list and click the corresponding Edit link. The User Settings tab of the Add/Edit User page is displayed.
- From the SSO Partner list, select the IdP.
- In the Partner User Identity box, enter the user's partner user identity, such as their email address.
- Click Save.
Data privacy and security features