Managing Roles in Oracle Permitting and Licensing
This topic introduces roles that are used to implement security and the general Oracle Cloud security role types. It also highlights key roles and configuration considerations to keep in mind when implementing Oracle Permitting and Licensing.
Role-Based Access Control
When you receive your Oracle Cloud application, access to its functionality and data is secured using the industry-standard framework for authorization, role-based access control. In a role-based access control model, users are assigned roles, and roles are assigned access privileges to protected resources. The relationship between users, roles, and privileges is shown in the following figure.
This diagram illustrates that users inherit privileges and security policy by way of roles assigned to them, which is described in the text that follows.
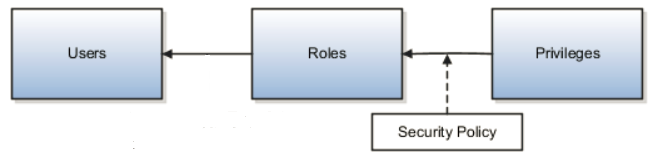
Users gain access to application data and functions when you assign them roles, which correspond to the job functions in your organization or the functions a pubic user in your municipality may perform.
Users can have any number of different roles concurrently, and this combination of roles determines the user's level of access to protected system resources. For example, a user might be assigned the Agency Staff role, the Permits Supervisor role, and the Permits Application Administrator role. In this case, the user has the following access:
With the Agency Staff role, the user can access functions and data suitable for agency staff members.
With the Permits Supervisor role, the user can access permits manager functions and data, and access and correct permit technician functions and data.
With the Permits Application Administrator role, the user can access permit configuration settings and make necessary changes.
When the user logs into Oracle Cloud and is successfully authenticated, a user session is established and all the roles assigned to the user are loaded into the session repository. Oracle Cloud determines the set of privileges to application resources that are provided by the roles, then grants the user the most permissive level of access.
Role Types
Oracle Cloud defines the following types of roles:
|
Role Type |
Description |
|---|---|
|
Job Roles |
Job roles represent the jobs that users perform in an organization. General Accountant and Accounts Receivables Manager are examples of predefined job roles. You can also create job roles. |
|
Abstract Roles |
Abstract roles represent people in the enterprise independently of the jobs they perform. Some predefined abstract roles in Oracle Applications Cloud include Employee and Transactional Business Intelligence Worker. You can also create abstract roles. All users are likely to have at least one abstract role that provides access to a set of standard functions. You may assign abstract roles directly to users. |
|
Duty Roles |
Duty roles represent a logical collection of privileges that grant access to tasks that someone performs as part of a job. Budget Review and Account Balance Review are examples of predefined duty roles. You can also create duty roles. Other characteristics of duty roles include:
Job and abstract roles may inherit duty roles either directly or indirectly. You don't assign duty roles directly to users. |
|
Aggregate Privileges |
Aggregate privileges are roles that combine the functional privilege for an individual task or duty with the relevant data security policies. Functions that aggregate privileges might grant access to include task flows, application pages, work areas, dashboards, reports, batch programs, and so on. Aggregate privileges differ from duty roles in these ways:
You can include the predefined aggregate privileges in your job and abstract roles. You assign aggregate privileges to these roles directly. You don't assign aggregate privileges directly to users. |
Duty Role Elements
Functional security privileges and data security policies are granted to duty roles. Duty roles may also inherit aggregate privileges and other duty roles.
|
Elements |
Description |
|---|---|
|
Data Security Policies |
For a given duty role, you may create any number of data security policies. Each policy selects a set of data required for the duty to be completed and actions that may be performed on that data. The duty role may also acquire data security policies indirectly from its aggregate privileges. Each data security policy combines:
|
|
Function Security Privileges |
Many function security privileges are granted directly to a duty role. It also acquires function security privileges indirectly from its aggregate privileges. Each function security privilege secures the code resources that make up the relevant pages, such as the Manage Grades and Manage Locations pages. Tip: The predefined duty
roles represent logical groupings of privileges that you may want
to manage as a group. They also represent real-world groups of tasks.
For example, the predefined General Accountant job role inherits the
General Ledger Reporting duty role. To create your own General Accountant
job role with no access to reporting structures, you could copy the
predefined job role and remove the General Ledger Reporting duty role
from the role hierarchy.
|
Aggregate Privileges
Aggregate privileges are a type of role. Each aggregate privilege combines a single function security privilege with related data security policies. All aggregate privileges are predefined. This topic describes how aggregate privileges are named and used.
Aggregate Privilege Names
An aggregate privilege takes its name from the function security privilege that it includes. For example, the Manage Accounts Payable Accounting Period Status aggregate privilege includes the Manage Accounting Period Status function security privilege.
Aggregate Privileges in the Role Hierarchy
Job roles and abstract roles inherit aggregate privileges directly. Duty roles may also inherit aggregate privileges. However, aggregate privileges can't inherit other roles of any type. As most function and data security in job and abstract roles is provided by aggregate privileges, the role hierarchy has few levels. This flat hierarchy is easy to manage.
Use of Aggregate Privileges in Custom Roles
You can include aggregate privileges in the role hierarchy of a custom role. Treat aggregate privileges as role building blocks.
Creating, Editing, or Copying Aggregate Privileges
You can't create, edit, or copy aggregate privileges, nor can you grant the privileges from an aggregate privilege to another role. The purpose of an aggregate privilege is to grant a function security privilege only in combination with a specific data security policy. Therefore, you must use the aggregate privilege as a single entity.
If you copy a job or abstract role, then the source role's aggregate privileges are never copied. Instead, role membership is added automatically to the aggregate privilege for the copied role.
Understanding Role Hierarchies and Inheritance
Almost every role is a hierarchy or collection of other roles.
Job and abstract roles inherit aggregate privileges. They may also inherit duty roles.
In addition to aggregate privileges and duty roles, job and abstract roles are granted many function security privileges and data security policies directly. You can explore the complete structure of a job or abstract role in the Security Console.
Duty roles can inherit other duty roles and aggregate privileges.
When you assign roles, users inherit all of the data and function security associated with those roles.
In Oracle Cloud, each role can be linked to other roles in a parent-child format to form a hierarchy of roles. As illustrated in the following figure, users are assigned job and abstract roles, which inherit duty roles and their associated privileges. Duty roles in turn can inherit privileges from subordinate duty roles. You can explore the complete structure of a job or abstract role on the Security Console.
This diagram illustrates the relationship between job roles, abstract roles, and duty roles, which is described in the text that follows.
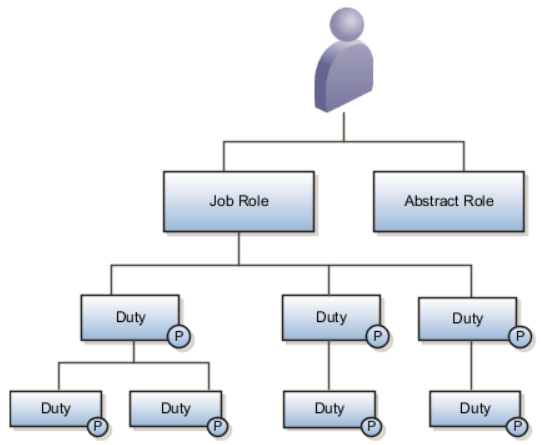
Role hierarchies allow privileges to be grouped to represent a feature set in Oracle Cloud, which simplifies feature management. Role hierarchies also provide privilege granularity and facilitate role reuse. For example, each role hierarchy beneath the job role represents a feature that is available through the job role to the user. Roles at lower levels of the hierarchy represent functionality that the feature requires. If this functionality is required by other features, the role that provides the functionality can be shared across roles.
This diagram illustrates a scenario of a user’s security roles and privileges and is described in the text that follows.
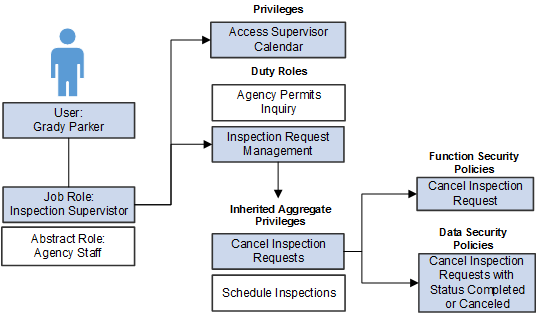
In the previous example, assume an inspection supervisor, Grady Parker.
Because Grady is employed by the agency, he is assigned the Agency Staff abstract role, and at least one job role, which is in the is case Inspection Supervisor.
Through the Inspection Supervisor job role, Grady inherits a set of duty roles, including the Inspection Request Management duty role. There is also a privilege unique to inspection supervisors, Access Supervisor Calendar, which is assigned directly to the job role.
The Inspection Request Management duty role contains other duty roles as well as a set of inherited aggregate privileges, including Cancel Inspection Requests and Schedule Inspections.
The Cancel Inspection Requests aggregate privilege is comprised of both a function security policy and data security policy.
Predefined Roles for Oracle Permitting and Licensing
Oracle Permitting and Licensing provides a set of predefined top-level roles that you can assign to users or clone to create additional roles. Oracle Cloud refers to the top-level roles in the system as top roles, because these are the roles at the top of the role hierarchy. Top roles can be job roles or abstract roles.
The following table lists a sample of the top roles in the Oracle Permitting and Licensing offering.
|
Role |
Role Type |
Description |
|---|---|---|
|
PSC Agency Staff |
Abstract |
Provides default privileges for any agency staff employee. |
|
PSC Registered Public User |
Abstract |
Provides default privileges for any end user who has completed the self registration process. |
|
PSC Building Inspector |
Job |
An agency staff position responsible for inspecting sites for permit approval. |
|
PSC Business Analyst |
Job |
A staff member that supports the agency in implementing and maintaining the applications. |
|
PSC Cashier |
Job |
Responsible for the sale and record keeping for various licenses and permits. |
|
PSC Chief Building Officer |
Job |
Manages a staff of permit technicians and inspectors. Oversees that the staff processes permits expeditiously and accurately and that all fees are collected and accounted. |
|
PSC Economic Development Officer |
Job |
Maintains various ledgers, registers, and journals according to established account classifications. Audits fees against department activity, researches discrepancies, and performs accounting clerical work. |
|
PSC Finance Administrator |
Job |
Reviews all incoming permit applications for accuracy and checks for any needed supporting documentation. Reviews the checklist to determine if they need further review or routing to other departments. |
|
PSC Geographical Information System Administrator |
Job |
Uses Geographical Information System software and related programs for provision of maps, charts, graphs, and other related information for visual displays, presentations or reports. |
|
PSC Inspections Supervisor |
Job |
Manages the workflow and staff to get through inspection jobs everyday. Keeps track of inspectors, districts and workload. |
|
PSC Permit Technician |
Job |
Performs permit technician duties, which includes processing applications, fee assessments, fee collections, documents, standardization, and permit issuance. |
|
PSC Permits Application Administrator |
Job |
An agency staff position that oversees the permit application. |
|
PSC Permits Supervisor |
Job |
Manages the workflow and staff to ensure that the permit applications are assigned and processed by the permit technicians. |
|
PSC Plan Reviewer |
Job |
Reviews plans for development, modification, alteration and demolition of commercial and residential properties. Checks compliance with applicable state and local zoning and building codes and related regulations. Calculates fees required for issuance of permits. |
|
PSC Planning Coordinator |
Job |
Coordinates plan review, permitting, and inspection of private construction projects in accordance with municipal ordinances and adopted building codes and code enforcement. |
|
PSC Principal Planner |
Job |
Reviews construction plans for compliance with all state and local development and zoning codes, regulations, and requirements. |
|
PSC System Administrator |
Job |
An agency staff position that has all access to configuration settings, security settings, and is able to access and solve issues for other users. |
|
PSC Zoning Administrator |
Job |
Responsible for administering and enforcing the Planning Code. Provides written interpretations and clarifications of the Planning Code. Advises the Planning Director on amendments to the Planning Code. Monitors and maintains data related to the ongoing implementation of the Planning Code. Manages planners to ensure Planning and Zoning Code compliance. |
|
PSC Associate Planner |
Job |
Prepares assessments on projects submitted for approval. Assists in the evaluation of projects submitted. Checks plans for zoning compliance. |
|
PSC Principal Planner |
Job |
Reviews construction plans for compliance with all state and local development and zoning codes, regulations, and requirements. |
|
PSC Planning Assistant |
Job |
Performs planning work involving the research, organization, and graphic presentation of zoning and planning data. Assists planners in compiling data, and assembling and distributing packets for board meetings. |
|
PSC Planning and Zoning Application Administrator |
Job |
Administers, manages, configures the Planning and Zoning offering. |
|
PSC Code Enforcement Application Administrator |
Job |
An agency staff position that oversees the Code Enforcement application. |
|
PSC Code Enforcement Officer |
Job |
Enforces municipal code, follows the route to assigned cases, records notes and statuses, issues citations, records cases in the field if violations are found, researches history of address, parcel, owner, and past violations. |
|
PSC Code Enforcement Supervisor |
Job |
Supervises, assigns, reviews, and participates in the operations and activities of an agency code enforcement program, including implementing activities related to setting and ensuring compliance with applicable ordinances, codes, and related regulations. The Supervisor ensures work quality and adherence to established policies and procedures, performs the more technical and complex tasks relative to assigned area of responsibility, and conducts field inspections and participates in hearings. |
|
PSC Code Enforcement Technician |
Job |
Serves as a gatekeeper for all code enforcement incidents, assigns inspections to code officers, responds to direct communications, manages noticing procedures, and supports escalations where necessary. |
|
PSC Auditor |
Job |
Responsible for developing, planning, implementing, and directing the city's comprehensive audit programs in order to evaluate the adequacy of the design and effectiveness of internal controls and the management of business risks within all departments. Works with management to assist in ensuring fiscal integrity of operational and financial assets in accordance with policies, procedures, and applicable laws and regulations. |
|
PSC Business License Manager |
Job |
Administers the business licensing program. Prepares annual business license bills. Prints and mails licensing bills for registered businesses, responds to inquiries from business owners and the general public, researches and resolves problem situations. Administers and enforces the provisions of the Alcohol Beverage Ordinance. Acts as a liaison between departments regarding privileged license information. |
|
PSC Business License Specialist |
Job |
Assists the public with general information as well as in completing required licensing forms, provides information to the public pertaining to licensing of businesses, and creates and maintains information sheets and other documentation for distribution to the public concerning business licenses. |
|
PSC Treasury Administrator |
Job |
Plans, develops, administers, and supervises the city's revenue collection and cash handling activities, including the collection and counting of revenues. Supervises, assigns, and reviews the work of supervisory, lead, technical, and clerical support staff. |
|
PSC Treasury Supervisor |
Job |
Responsible for managing the cash position of the city, which includes overseeing the city's revenue collection processes and procedures, ensuring daily liquidity and cash position, overseeing cash management services including bank accounts and banking products, account analysis, and armored car services. |
The remainder of the delivered roles are lower-level child roles that group privileges and link privileges to the top-level roles.
Key Duty Roles in Oracle Permitting and Licensing
The following table highlights a set of key duty roles to illustrate some delivered, predefined duty roles.
|
Duty Role |
Description |
|---|---|
|
PSC Apply Permit |
Provides all the access required for an applicant, such as being able to access a permit, fill in and submit a permit application, add comments to the permit during the application process, and so on. |
|
PSC Agency Permits Inquiry |
Provides the read only access for the agency staff members so that they can review and process permit applications. |
|
PSC Anonymous Permit Application Inquiry |
Provides read-only access for viewing a permit application. Note: Oracle Fusion Applications
do not allow modification of any anonymous roles.
|
|
PSC Apply Planning Application |
Provides all the access required for an applicant, such as being able to access a planning application, fill in and submit a planning application, add comments to the planning application during the application process, and so on. |
|
PSC Agency Planning Application Inquiry |
Provides the read only access for the agency staff members so that they can review and process applications. |
|
PSC Anonymous Planning Application Inquiry |
Provides read-only access for viewing a planning application. Note: Oracle Fusion Applications
do not allow modification of any anonymous roles.
|
|
PSC Report Code Enforcement Issue Duty |
Provides all the access required for reporting an issue for Code Enforcement, such as being able to access issue subtype, fill in and submit an issue intake form, add comments to the report during the process, and so on. |
|
PSC Agency Code Enforcement Case Inquiry |
Provides the read only access for the agency staff members so that they can review and process cases. |
|
PSC Agency Code Enforcement Incident Inquiry |
Provides the read only access for the agency staff members so that they can review and process incidents. |
|
PSC Anonymous Code Enforcement Incident Inquiry |
Provides the read only access for anonymous users so that they can review reported incidents. |
|
PSC Agency Business Consultation Inquiry |
Provides the read only access for the agency staff members so that they can review and process business license consultations. |
|
PSC Agency Business License Inquiry |
Provides the read only access for the agency staff members so that they can review and process business licenses. |
|
PSC Anonymous Business License Inquiry |
Provides the read only access for anonymous users so that they can review business licenses. |
|
PSC Business Entity Inquiry |
Allows users to view business entities. |
|
PSC Apply Business License |
Allows users to apply for business licenses. |
|
PSC Business License Application Administrator |
Enables the administration of the Business Licenses offering. |
Working with Aggregate Privileges in Oracle Permitting and Licensing
All aggregate privileges are predefined. Aggregate privileges combine a single functional security privilege with related data security policies.
In many cases with roles in the Oracle Permitting and Licensing Cloud, you see a pattern, where one aggregate role provides the general, default behavior, such as allowing a user to insert comments and update only their own comments. Then there is a counterpart aggregate role that would provide more far reaching privileges, such as updating the comments for others.
For example, consider these aggregate roles:
PSC Update Inspection Comments added by self
PSC Update Inspection Attachments added by self
PSC Update Inspection Comments added by others and self
PSC Update Inspection Attachments added by others and self
For example, with the comments and attachments, most roles provide you with the ability to add comments or attachments and update comments or attachments inserted by yourself. However, by assigning to the user another aggregate role (with the phrase “by others and self” in the role title), that user could update comments or attachments added by others. A supervisor in the permit processing department could update comments in a permit added by one of their permit technicians if they have the following role assigned to their user account: PSC Update Inspection Comments added by others and self.
By default, the ”by others and self” aggregate privileges are assigned only to system administrators.
Modifying Delivered Roles
If the delivered top roles do not meet your business requirements, you can create custom roles by cloning a delivered job or abstract role, and then modifying the custom role as needed. When cloning a role, this also copies the role hierarchy, which you can modify as needed by either adding or removing elements of the hierarchy.
When creating custom roles, it is highly recommended to modify a role’s access through aggregate privileges, rather than attempting to modify a job, abstract, or duty role manually. Modifying access using aggregate privileges is efficient and a more robust approach. Keep in mind that aggregate privileges contain both the functional security and the data security policy for an action. By adding or removing an aggregate privilege, you make one change, but adjust both aspects of security simultaneously.
If you update a duty role manually, you will need to always make sure you’ve added or removed the functional and data security counterparts. Otherwise, you may not be providing or restricting the access you intend, while in other cases, you may be creating security holes, unintentionally.