Redwood Experience for Preview HCM Data Security
Enrich the user experience with a new Preview HCM Data Security page developed using the Redwood toolset. This page is built from the ground up using Visual Builder Studio (VBS) to give you a unique experience of Oracle applications. Preview HCM Data Security still allows you to troubleshoot and analyze a specified user's data access based on all of their current roles and areas of responsibility.
Oracle Search-related access control list (ACL) attributes and calculations are more integrated in this page design.
Enhancements to this page include the following:
- Updated look and feel that's consistent with Oracle's latest Redwood patterns.
- Simplified page where the details of the Currently Assigned Roles, Assigned Areas of Responsibility, and Session-based Roles are moved to the User Summary panel drawer.
- The primary call to action of "Generate Diagnostic Log" button is easily available on the main page header.
- Additional actions are available under the Actions menu which is also found on the page header.
- For example, if Oracle Search is enabled, you can refresh the selected user's access control list (ACL).
- Additional actions now appear to support summarizing specific troubleshooting information from the larger, generated diagnostic log which simulates ACL computation. You can now generate and download specific portions, including:
- Access control list
- Access control list summary
- Index configuration summary
- New section to view access based on privilege, adding a new comment to inform users that either data security policy can be provided, or you can enter a privilege-data resource combination,
- New Preview Access button is enabled after the privilege information is provided.
- Latest user session details and available records details will appear.
- If Oracle Search is enabled, details of access control list size will appear.
- You can use the column management icon to modify the visible columns in the Secured Access table.
- Additional information about the role and its policies appears in a panel drawer when you click the Associated Role Name link.
- Prior "Direct/Indirect" column has been renamed to "Role Inheritance".
- Descriptive badges now appear in the Role Inheritance and Allowed Access columns.
Preview HCM Data Security lets you select a user name and perform analysis based on that user's assigned roles during their last session. For example, the user Veda Moss isn't able to search for a particular person, or conversely, has access to too many people. Here, we're interested in looking at the user, Veda Moss.
You must provide either a data security policy name, or the privilege and data resource combination. In this case, we're interested in the Manage Person privilege and Person Detail data resource.
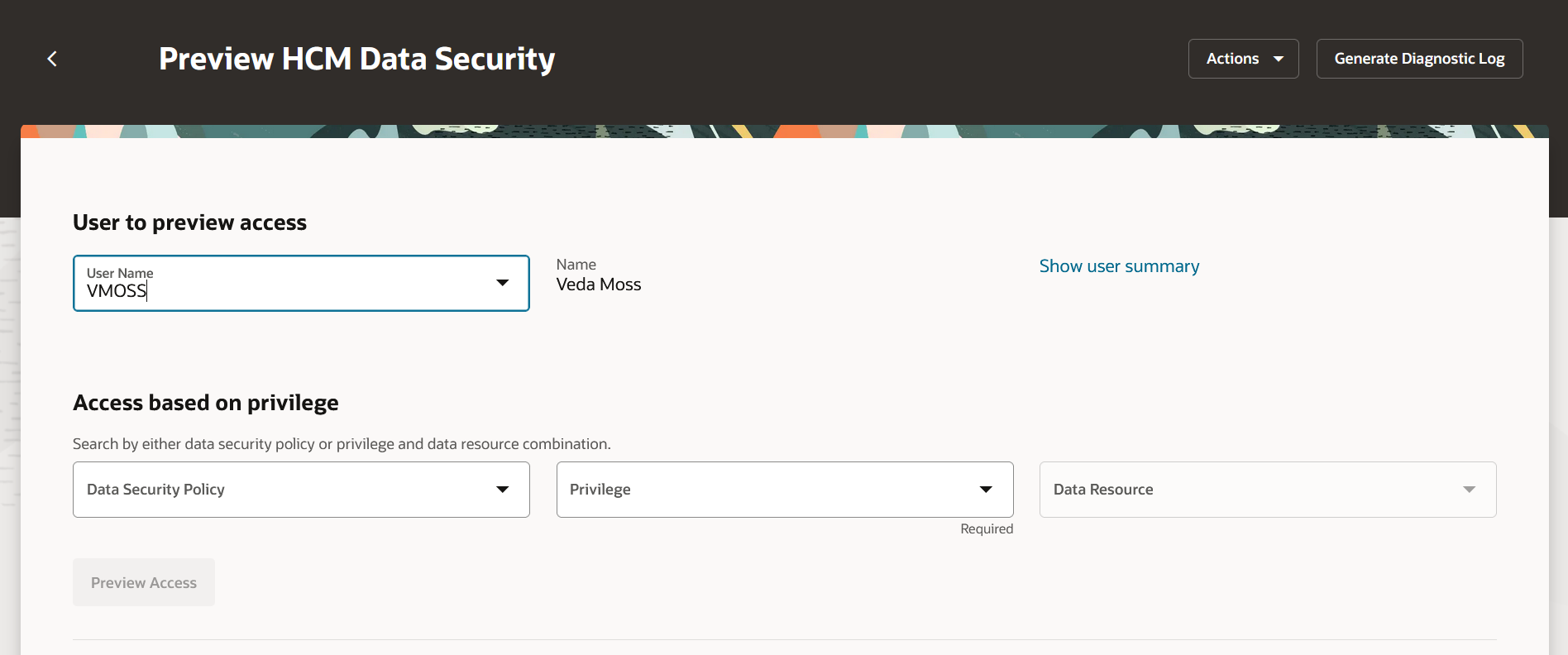
Search for user Veda Moss
Since we've streamlined the content on this page, you'll now find the user's currently assigned roles, assigned areas of responsibilities (AORs) and session-based roles from the Show user summary link.
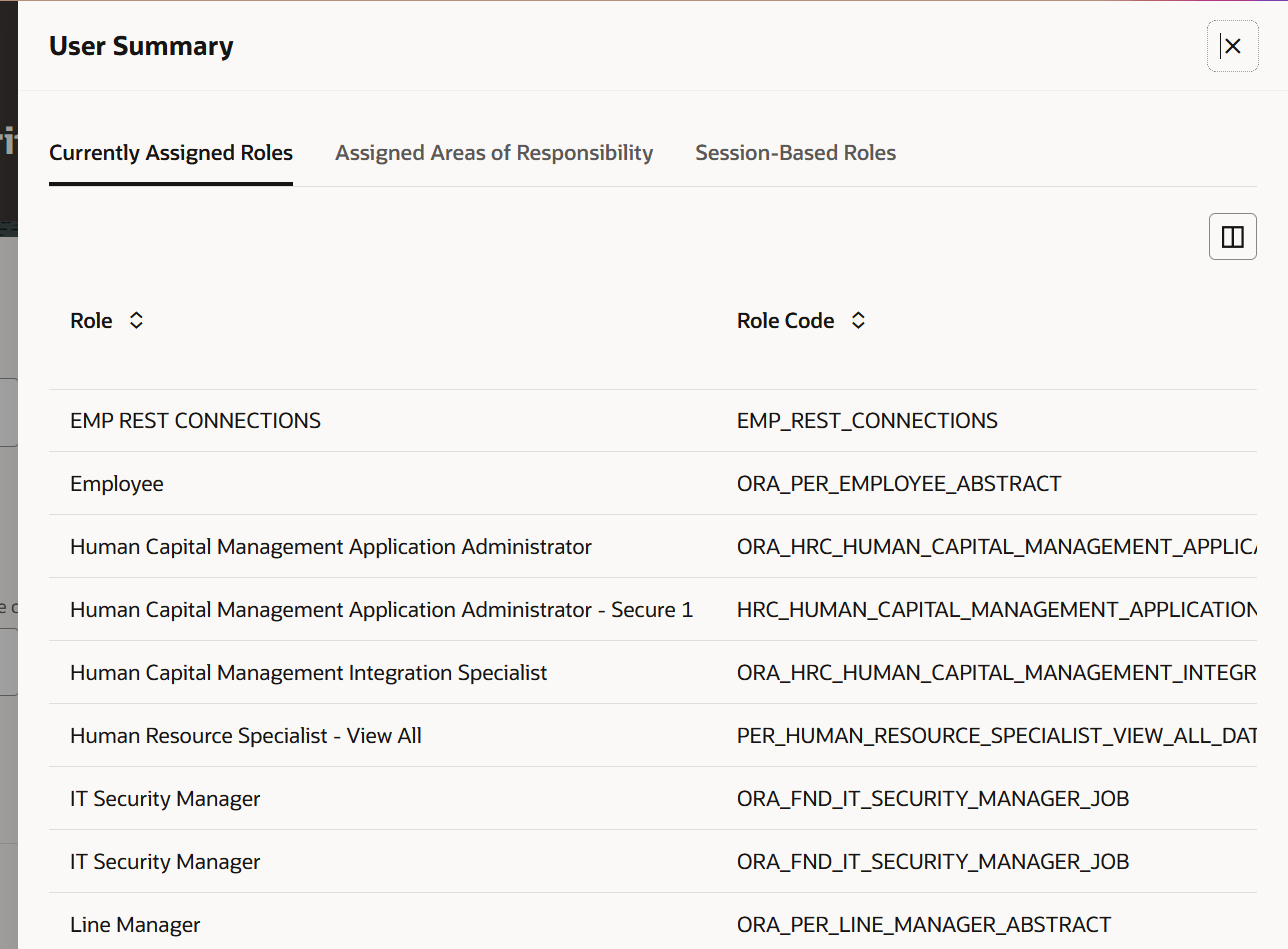
Show User Summary panel drawer content
If a user doesn't have access to certain objects or LOV content that you were expecting, you can choose Refresh Access Control List from the Actions menu. After the refresh is complete, a confirmation message appears on the page header.
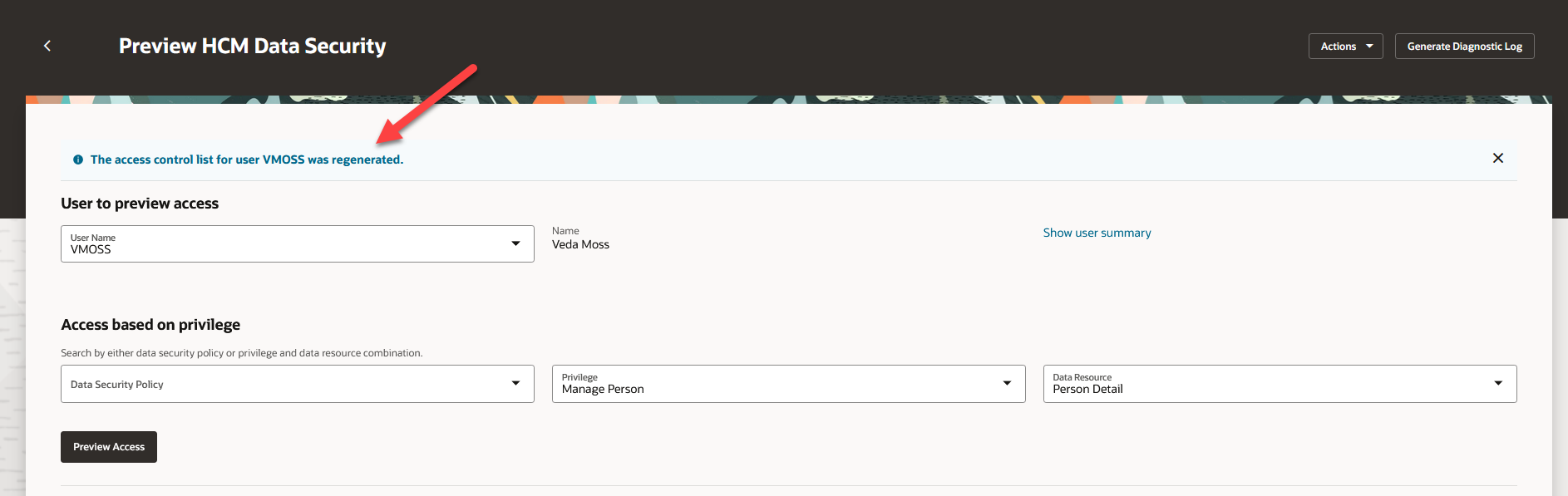
Refresh Access Control List confirmation message
After choosing the Preview Access button, you can simulate person search and verify which associated role is granting data access to a certain person.
Verify access button still allows you to search by object, depending on which privilege you are searching by. In the following example, you want to find out how the user, VMOSS, gets access to Kelly George. By providing the object name, in this case a person's name, Kelly George and then choosing the Verify button, you can see which of the roles from the user's last session allow access to this person. A "Yes" badge, means access is granted through the corresponding role.
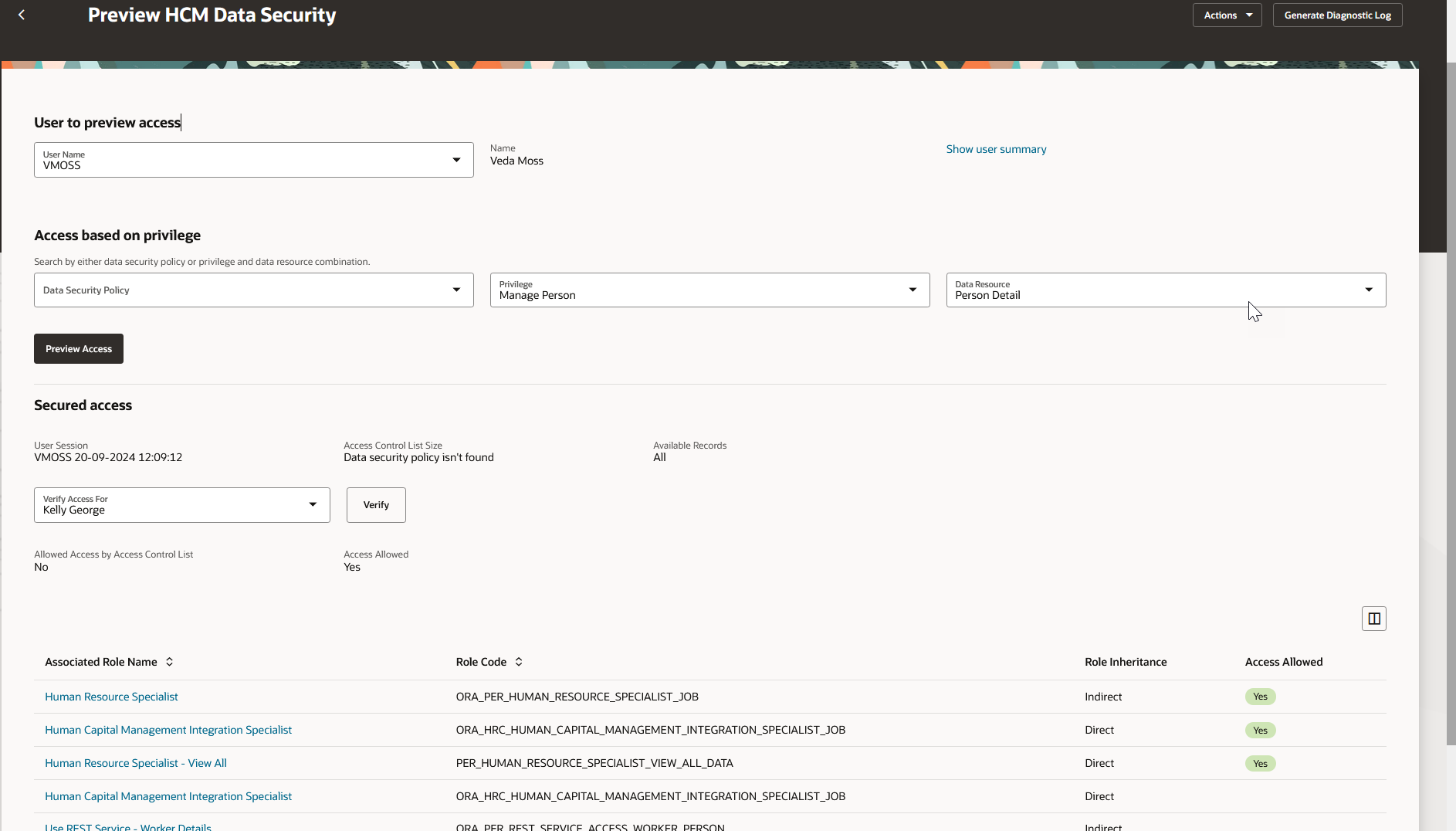
A badge in the Access Allowed column indicates which role gives access to the searched person
In this case, for the given privilege and data resource, the user (VMOSS) is not allowed access by the Access Control List (ACL), but does have access through the Database secured access.
The table results then reflect which of the associated roles give access to Kelly George. You can click on the associated role name to see additional role and policy information.
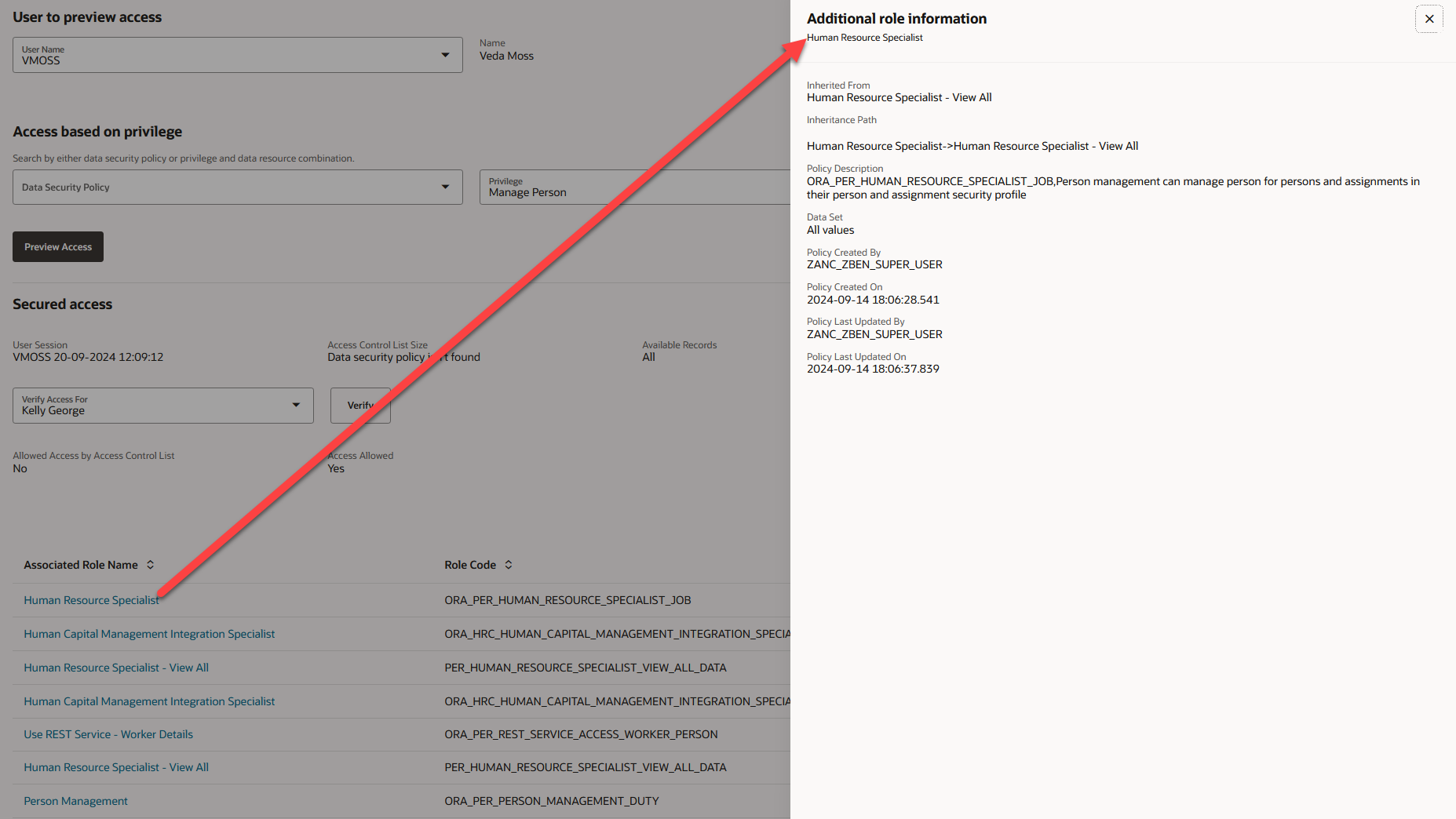
View additional role information by clicking on the associated role name
Updated look and feel that's consistent with the latest Redwood patterns.
Steps to Enable
Enable the following profile options:
- ORA_HCM_VBCS_PWA_ENABLED (Enable VBCS Progressive Web Application User Interface)
- ORA_PER_PREVIEW_HCM_DATA_SECURITY_REDWOOD_ENABLED (Redwood Preview HCM Data Security Enabled)
To enable the profile options, navigate to the Setup and Maintenance work area:
- Search for and click the Manage Administrator Profile Values task.
- Search for and select the profile option.
- Select the Level as Site.
- Enter Yes in the Profile Value field.
- Click Save and Close.
Tips And Considerations
- Make sure the user has signed in recently! All data access details are still based on the user's most recent signed-in session information.
- If you've selected a user without a valid session, the Preview Access button won't be activated.
- When Oracle Search is enabled, additional read-only attributes are displayed that are related to access control list (ACL) computations.
- Since the buttons at the top of the page are based on the provided user, these buttons are hidden until a user is selected.
- This page is not integrated with VB Studio, so no customizing is allowed.
- To find the privilege in question, perform the following steps:
- Navigate to the page where the user's data access is an issue.
- Open Developer Tools.
- Choose the Network tab and filter by LOV name, such as "worker".
Key Resources
- HCM Redwood Pages with Profile Options (Doc ID 2922407.1)
- How You Preview HCM Data Security
Access Requirements
IT SECURITY MANAGER