Overview of Advanced Access Requests
Advanced Access Requests implements a self-service workflow for requesting and assigning ERP roles. If access controls are active, then this workflow begins with the controls analyzing role requests for separation-of-duties and sensitive-access issues, and adding results of their analysis to the request records. If no access controls are active, no risk analysis takes place. In either case, however, users complete a review-and-approval process for each role request.
Your current provisioning process might involve four manual steps: First, use the Security Console to assign Fusion roles to ERP users. Second, use the Manage Data Access for Users task in Functional Setup Manager to set data security for the role assignments. Third, check for SOD and sensitive-access policy violations. And last, document business-owner approvals, for example via email.
But Advanced Access Requests replaces these steps. Here's how it works:
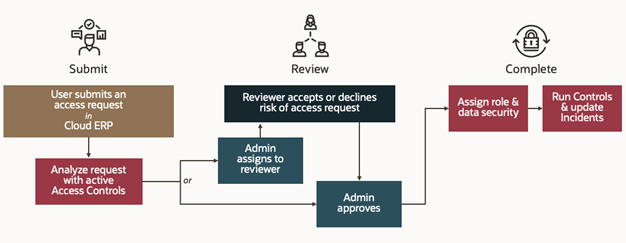
You request one or more roles either for yourself or for another user. You can request any role that can be assigned directly to a user, such as a job, data, or abstract role. Along with the role, you may make data requests, which define a set of data records the user can create or work with. For example, these might be records associated with a business unit you specify. If the request were to be granted, the user's authorization for the role would apply only to those records.
An Advanced Access Request Analysis job then runs, processing all requests that have accumulated since its previous run. The job runs on a schedule, although you can also run it on demand in the Scheduling page of Risk Management Setup and Administration. Its results depend on whether active access controls are in place:
-
If one or more access controls are active, the job runs them to uncover SOD and sensitive-access issues. Requested controls may conflict either with each other or with a user's already-assigned roles. When the job finishes running, Advanced Access Requests reports the number of control violations for each role request. It also names the controls that have found violations, identifies the roles that conflict, and provides related data.
-
If no access controls are active, the job processes pending requests, but performs no access-risk analysis. In pages displaying records of these requests, Advanced Access Requests displays a banner message stating that controls need to be activated for risk analysis to be performed.
The person who makes final decisions about requests is known as a "request approver." But before deciding on a given request, the approver may select a reviewer for it. This person judges whether the risk (or the absence of risk analysis) is acceptable, and therefore if the request should be granted or refused. By default the reviewer is the manager of the user for whom the role has been requested. However, the request approver may select another person with an interest in the work the user would be doing. In any case, the reviewer's judgment isn't binding, and the review process is optional.
Regardless of whether the review step takes place, the request approver determines whether to approve or reject the role for the user. For each approved role, Advanced Access Requests automatically completes these tasks:
- Updates the user's record in the Security Console to add the requested role. This happens whenever a role assignment is approved.
- Creates a new record in the Manage Data Access for Users task of Functional Setup Manager. This record associates the user, role, and data request with one another. This happens only when an approved request includes a data request.
- Creates incidents in the Results work area to track control violations, if the request has generated any.
The request approver can also remove roles from users to whom they're assigned. The approver may be responding to requests by business owners or to removal reports generated by analysis in Oracle Fusion Cloud Access Certifications.