How You Get Started with Security Implementation in Oracle Fusion Cloud SCM
To start an Oracle Fusion Cloud SCM Cloud, you must set up one or more initial users using the super user that was created during installation and provisioning of the Oracle Applications Cloud environment, or using the initial administrator user provided by Oracle for Oracle
-
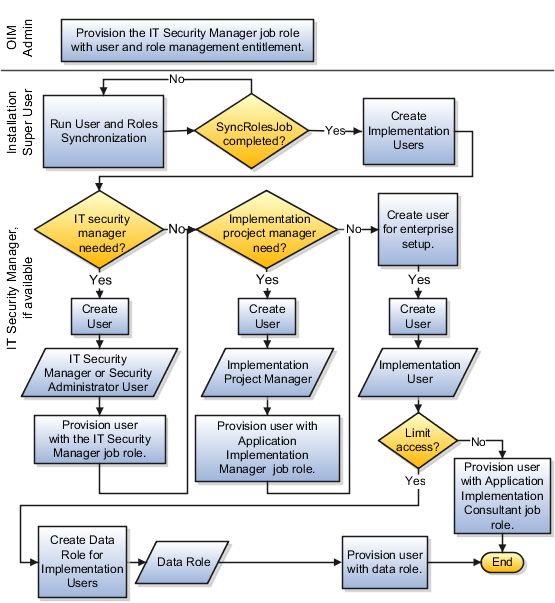
If you're not starting an Oracle Cloud implementation, sign in as the super user of the security console and provision the IT Security Manager job role with roles for user and role management. This enables the super user account, which is provisioned with the IT Security Manager job role, to create implementation users.
-
For starting all implementations, sign in as the user with initial access: either the Oracle Fusion Cloud SCM installation super user or the initial Oracle Cloud administrator user.
-
Select an offering and functional area to implement, and generate the setup tasks needed to implement the offering.
-
Perform the following security tasks:
-
Synchronize users and roles in the Lightweight Directory Access Protocol (LDAP) store with HCM user management by using the Run User and Roles Synchronization Process task.
-
Create an IT security manager user by using the Create Implementation Users task.
-
Provision the IT security manager with the IT Security Manager role by using the Provision Roles to Implementation Users task.
-
-
As the newly created IT security manager user, sign in to Oracle Fusion Cloud SCM and set up at least one implementation user for setting up enterprise structures.
-
Create an implementation user by using the Create Implementation Users task.
-
Provision the implementation user with the Application Implementation Manager job role or the Application Implementation Consultant job role. The Application Implementation Consultant job role inherits from all product-specific application administrators and entitles the necessary View All access to all secured objects.
-
Optionally, create a custom role for an implementation user who needs only the limited access of a product-specific Application Administrator by using the Supply Chain Application Administrator role. Then assign the resulting custom role to the implementation user by using the Provision Roles to Implementation Users task.
-