OAuth 2.0 Support for Integrations
Oracle Integration Cloud (OIC) is a complete and secure integration solution that enables you to connect your applications in the cloud. OIC simplifies the connectivity between your applications that live in the cloud and your applications that still live on premises.
OAuth 2.0 Support for Input Interfaces
Before you build an integration, you need to create a connection to the applications that provides minimal connectivity information for each system.
While setting up a connection in Oracle Integration Cloud (OIC) to connect to Warehouse Management (WMS) using the REST adapter, you can use one of the following security policies:
- Basic Authentication: For basic authentication, the username and password of the user in the WMS application are required.
- OAuth2.0: There is support in WMS to perform token-based authentication using
OAuth2.0 with the following two grant types.
- Resource Owner Password Credentials – You can log in to the application with the Password credentials.
- Authorization Code – You will be redirected to the mentioned URL every time to get an authentication code.
Configuring the OAuth2.0 Authentication in WMS
Complete the following steps to configure OAuth2.0 in WMS:
- Create a screen using module 'api/oauth2/applications' (Screen Type
UI-HTML-PP).
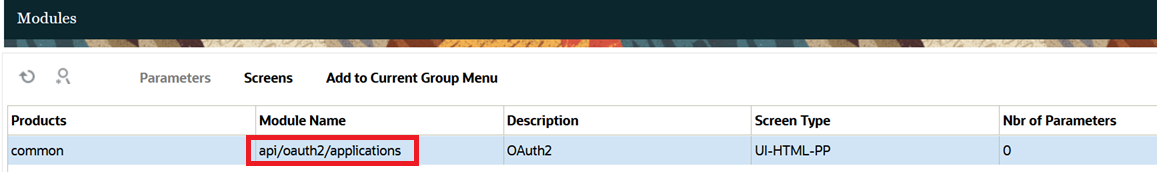
- Navigate to the created screen and click the Click here hyperlink to register a new application.
- Use the created screen to configure client applications that will connect to WMS
using OAuth2.0 to access REST APIs and click Save.
Customers can have different applications to connect to integration tools, OIC is one of these.
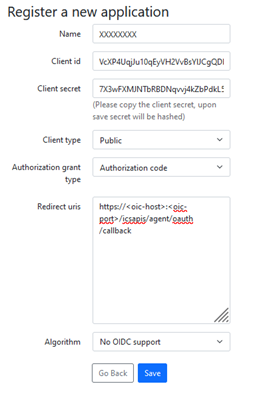 Note:
Note:- A Client Id and a Client Secret will be generated for every application configured. If the authorization grant type selected is ‘Authorization Code’, then a redirect URI must be provided. For OIC, the Redirect URI will be – https://<oic-host>:<oic-port>/icsapis/agent/oauth/callback.
- If you are not an admin user in WMS, you will not be able to access the created screen even if the screen is assigned to your group’s menu. You need to be part of a group that has been given permission ‘OAuth2 / Manage OAuth2 Applications’ to manage OAuth2.0 client applications.
Configuring the REST Connection’s Security Policy in OIC
For configuring a REST Connection Security Policy, do the following:
- Log into the Oracle Integration application.
- On the dashboard, click “View Integrations” button.
- Click Show/Hide navigation menu icon.

- Click Connections and then click Create button.

- In the search box, search for REST Adapter connection and in the search results, click on the REST.
- Enter the details and click Create.
- On the connection screen, do the following and click Save:
- Select a Connection Type.
- Enter the Connection URL that corresponds to the selected Connection Type.
- Select a Security Policy and enter the fields that pops-up based on the
selected Security Policy.Note: Based on the type of Security Policy selected in configuring a connection, the fields to enter will vary.
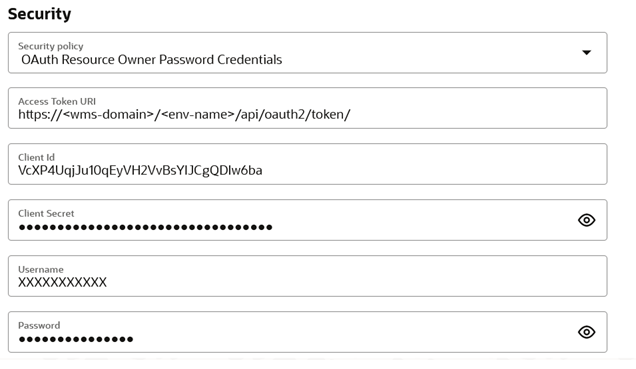
You can configure OAuth Resource Owner Password Credentials with the following fields:
- Access Token URI: https://<wms-domain>/<env-name>/api/oauth2/token/
- Client Id: Client Id generated when configuring an application as described in in the above section.
- Client Secret: Client Secret generated when configuring an application as described in the above section.
- Username: Username of WMS user.
- Password: Password of WMS user.
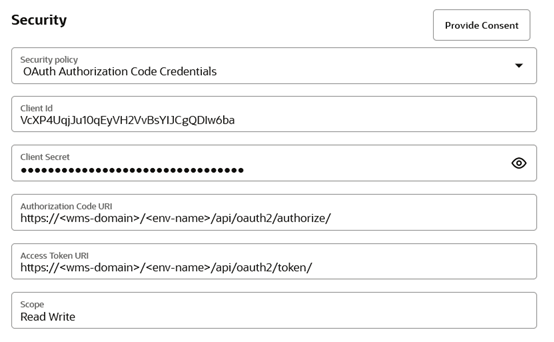
You can configure OAuth Authorization Code Credentials with the following fields:
- Client Id: Client Id generated when configuring an application as described in the above section
- Client Secret: Client Secret generated when configuring an application as described in the above section
- Authorization Code URI: https://<wms-domain>/<env-name>/api/oauth2/authorize/
- Access Token URI: https://<wms-domain>/<env-name>/api/oauth2/token/
- Scope: Is not supported by WMS as of now. Enter “Read Write” as it is a required field.
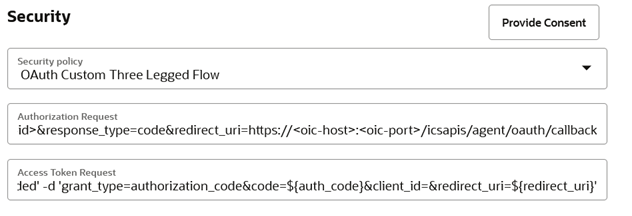
You can configure the Custom Three-Legged flow with the following fields:
- Authorization Request: https://<wms-domain>/<env-name>/api/oauth2/authorize/?client_id=<client-id>&response_type=code&redirect_uri=https://<oic-host>:<oic-port>/icsapis/agent/oauth/callback
- Access Token Request: -X POST https://<wms-domain>/<env-name>/api/oauth2/token/ -H 'content-type: application/x-www-form-urlencoded' -d 'grant_type=authorization_code&code=${auth_code}&client_id=&redirect_uri=${redirect_uri}'
OAuth 2.0 Support for Output Interfaces
When Warehouse Management receives information, such as Purchase Orders, ASNs, etc., from external applications, the authentication protocols are supported using OAuth 2.0.
OAuth acts as an intermediary on behalf of you by providing the service with an access token that authorizes the information to be shared.
To allow you to configure, validate, and transfer data to external systems, the OAuth2.0 fields are available on the Output Interface Configuration Detail UI.
OAuth2.0 supported fields are available on the Create and Edit pane of the detail page for every interface type. The columns are hidden by default. You can add the fields to your UI view as needed.
For example, to add OAuth2.0 authentication protocol for one of the output interfaces, do the following:
- Go to the Output Interface Configuration UI.
- Select a record and click Output Interface Target (same as details icon)
icon.Note: OAuth2.0 fields are not applicable for "Bill of Lading" and "Commercial Invoice" interface types, as e-mail and printer are the only two protocols supported "Bill of Lading" and "Commercial Invoice" interface types.
- On the Create or Edit pane, Select REST Web Service as Interface
Protocol, and add the following authentication fields to support OAuth2.0
Protocol.
Field Name
Field Type
Mandatory
Values
Comments
Interface Authentication Type ID Drop-down Yes - Basic Auth
- OAuth2.0 - Client Credentials (CC)
- OAuth2.0 - Password
Drop-down to select the authentication type. Client ID Text Field Conditional Yes Mandatory if the grant type is one of the following:
- OAuth2.0 - Client Credentials
- OAuth2.0 - Password
Client Secret Text Field Conditional Yes Mandatory if the grant type is one of the following:
- OAuth2.0 - Client Credentials
- OAuth2.0 - Password
Token URL Text Field Conditional Yes Mandatory if the grant type is one of the following:
- OAuth2.0 - Client Credentials
- OAuth2.0 - Password
Scope Text Field Conditional Yes Mandatory if the grant type is one of the following:
- OAuth2.0 - Client Credentials
- OAuth2.0 - Password