2.3 Running Helidon Server in SSL/ TLS
- Extract your GGSA distribution
- Set the following variables in the
osa-base/etc/osa-ssl/ssl.conffile, to manage the SSL certificates:- NEED_SSL - This variable is a flag to enable SSL for GGSA product. Value true/false
- OSA_SERVER_CRT_P12 - This variable stores the path to the P12 server certificate file which you have. Example - /yourPath/server.p12
- OSA_SERVER_CRT_PWD - This variable stores the passphrase/ key for
the certificate. This needs to be stored in encrypted form.
To generate the encrypted for of the certificate password run the following command:
cd osa-base/bin/ ./osa-secure-tool.sh <certificatePassword> - OSA_SERVER_CRT_GENERATED_BY - This variable is just stores if the certificate is generated by the app for demo or testing purpose or the user. We can set this to either user or app if the self signed certificate is generated for testing or demo purpose of the app. Please note it is not recommended to use app generated certificate in production.
- OSA_SERVER_CRT_FAIL_ON_VALIDATIONS - This flag fails startup of
application if validations issues have been identified in the specified
certificate. If false, it will still run validations print out issues on
console and proceed running the application with warnings.The followings
things are currently being validated in the certificate -
- Validation Public Key
- Validate Private Key
- Validate Public Private Key match
- Certificate expiry checks
- Weak Algorithms usage
- Self signed certificates usage
-
Once the variables are setup for SSL connection, we need to run the GGSA application as usual.
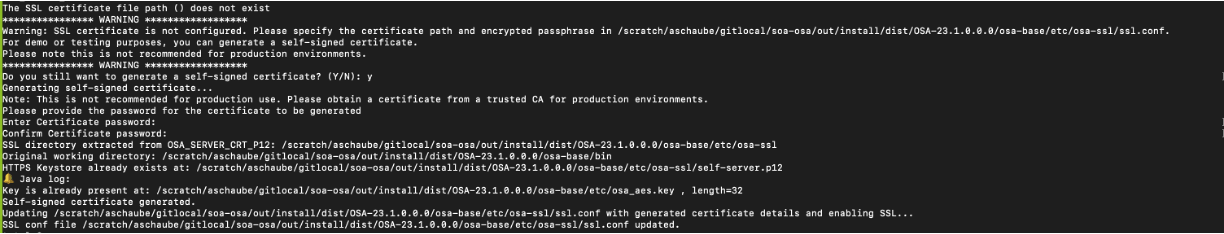
Please note that if no OSA_SERVER_CRT_P12 is specified but NEED_SSL is true, then the program asks for a prompt to the user if they want to generate a self-signed certificate ( with warnings of not to use it in production environments).
If prompt response is 'y' then It asks for the certificate passphrase and updates the conf.ssl file with the generated certificate details.