Data Sovereignty Use Case
A large but imaginary financial institute, Shard Bank, wants to offer credit services to users in multiple counties. Each country where credit service will be provided has its own data privacy regulations and the Personally Identifiable Information (PII) data have to be stored in this country.
The access to the data has to be limited and data administrators in one country cannot see data in others. The solution for this use case is user-defined Sharding with shards configured in different countries and Real Application Security (RAS) or Virtual Private Database (VPD) for data access control.
Overview of the Data Sovereignty Solution
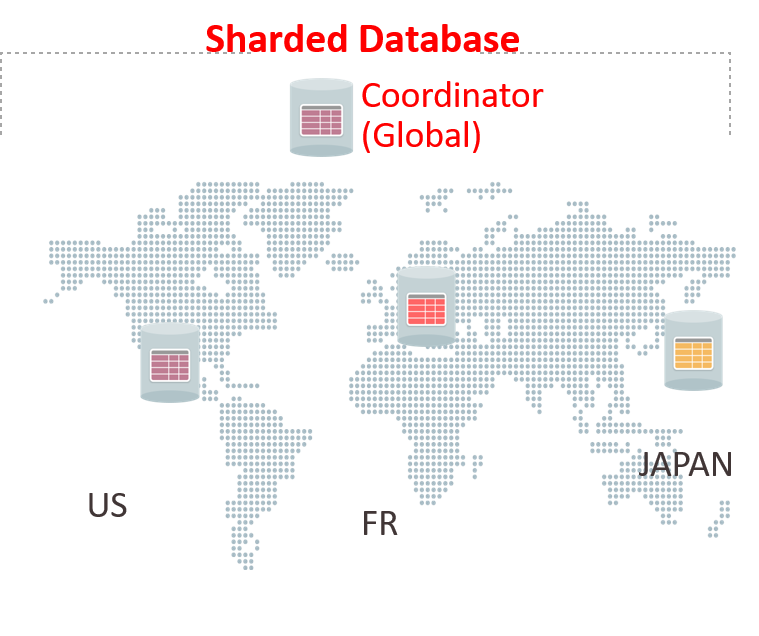
This data sovereignty solution provides you with in-country data storage, and still supports a global view of all the data.
The global distributed database is partitioned by a key indicating the country in which it must reside. In-country applications connect to the local database as usual, and all data is stored and processed locally.
Any multi-shard queries are directed to the shard coordinator. The coordinator rewrites the query and sends it to each shard (country) that has the required data. The coordinator processes and aggregates the results from all of the countries and returns result.
Oracle Globally Distributed AI Database makes this use case possible with the following capabilities:
- Direct-to-shard routing for in-country queries.
- The user-defined sharding method allows you to use a range or list of countries to partition data among the shards.
- Automatic configuration of replication using Oracle Active Data Guard, and constrain the replicas to be in-country.
- Data federation support (starting with Oracle Database 21c) for converting and adding existing databases into a distributed database. For more information, see Creating a Federated Distributed Database.
- Automatic derivation of sharding key (starting with Oracle Database 21c).
The benefits of this approach are:
- Each shard can be in a cloud or on-premises within the country.
- Shards can use different cloud providers (multi-cloud strategy) and replicas of a shard can be in a different cloud or on-premises.
- Online resharding allows you to move data between clouds, or to and from the cloud and on-premises.
- Strict enforcement of data sovereignty providing protection from inadvertent cross region data leak.
- Single Multimodel Big Data store with reduced volume of data duplication.
- Better fault isolation as planned/unplanned down time within one region/LOB does not impact other regions/LOBs.
- Ability to split busy partitions and shards as needed.
- Support for full ACID properties is critical for transactional applications.
Deployment Topology for Data Sovereignty
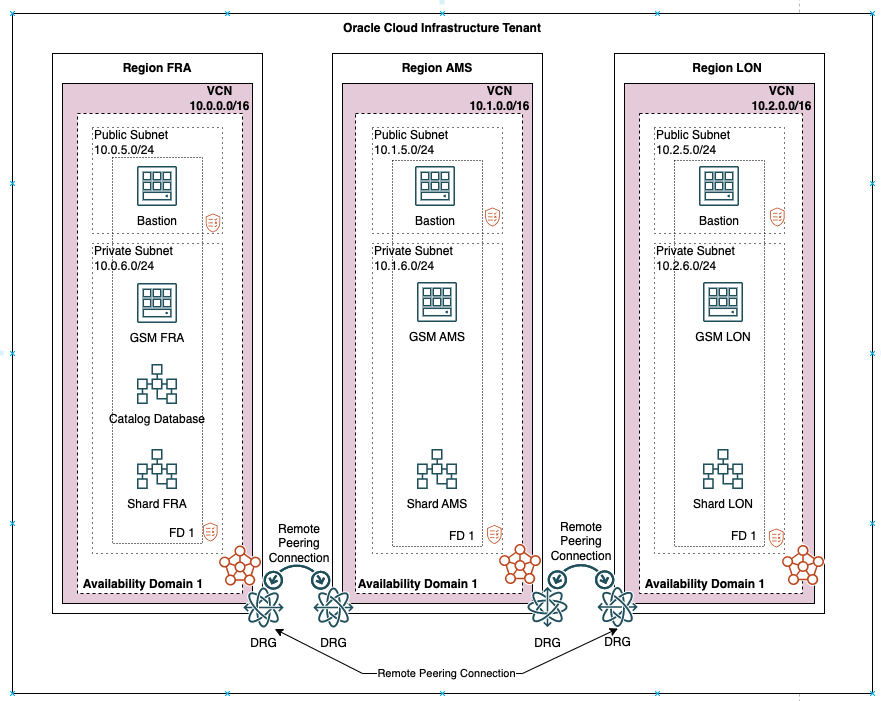
In this example use case, we create a distributed database on Oracle Cloud Infrastructure that spans three regions, Frankfurt (Region1 FRA), Amsterdam (Region 2 AMS), and London (Region 3 LON).
Figure 16-3 Deployment Topology of Data Sovereignty
Configuring the Data Sovereignty Use Case
Configure the Oracle Globally Distributed AI Database Data Sovereignty use case by performing the steps given in the following topics.
Configuring VCN Networks in All Three OCI Regions
In Oracle Cloud Infrastructure (OCI), a virtual cloud network is a virtual version of a traditional network on which your instances run. Deploy and configure a virtual cloud network (VCN) in each of our regions (FRA, AMS, and LON).
- Create new route table for private subnet and associate it with private subnet. The default route table should only be used for the public subnet and the private subnet should have a dedicated private route table.
- Create an internet gateway and associate it with default route table.
- Create a Network Address Translation (NAT) gateway, Service Gateway, and associate it with route table for private subnet.
- VCN Name/CIDER: Sharding VCN FRA 10.0.0.0/16
- Public Subnet name/CIDER: public_fra 10.0.5.0/24
- Private Subnet name/CIDER: private_fra 10.0.6.0/24
Note:
Repeat the steps in all regions used in the sharding deployment. The subnet CIDER must be different in each region and you must provide region prefix in the VCN/subnet name.Configuring Remote VCN Peering Between All Three Regions
Remote VCN peering is the process of connecting two VCNs in different regions, which allows the VCNs' resources to communicate using private IP addresses without routing the traffic over the internet.
Configuring Private DNS for Naming Resolution Between the Regions
You create private views for the public and private subnet for each domain in each region, resulting in a total of 6 private zones within 1 zone. Then all entries are added to each private zone configuration.
- See Private DNS to create and manage private DNS zones.
- Verify that all names are resolved correctly before you proceed with the next task.
Note:
These steps must be done in each region on all VCNs/VMs so that names can be correctly resolved.Installing a Global Service Manager in Each Region
Oracle Global Data Services global service manager (GSM) is used by Oracle Globally Distributed AI Database to route queries from the application to the correct shard in a distributed database.
- Download the global service manager (Oracle Database 19c) software into the bastion VM.
- Apply the latest version of OPatch.
- Apply the latest available Oracle Database Bundle Patch on the newly installed global service manager (Oracle Database 19c).
Collecting TNS Entries for the Shard Catalog and Shards
The collection of TNS entries is required to prepare GSM server for configuration of the shard catalog database and shard databases.
The shard catalog database requires access only to PDB that stores the shard catalog database objects. However for the shard databases, prepare the entries for each shard CDB and PDB that stores the application schemas.
Configuring the Shard Catalog
The shard catalog manages the metadata for Oracle Globally Distributed AI Database. Configure a database on Region 1 (FRA) which will be the shard catalog database.
Configuring the Shard Databases
Configure a database in each region which will be a shard in the distributed database configuration.
Creating the Oracle Globally Distributed AI Database
Configure the global service manager listener, create a shard catalog database, and add all of the shards to the configuration. The deployment step configures all shards as a single global database.
Related Topics
Implementing a Session-Based Application Context Policy
Add row-level data access control on the distributed database in conjunction with the Oracle Database virtual private database (VPD) feature for both single shard queries and multi-shard queries. Oracle Global Data Services global service manager (GSM) is used in Oracle Globally Distributed AI Database to route queries from the application to the correct shard in a distributed database.