3.1 Security Checking from Tuxedo to Mainframe
The following figure depicts the process flow for security verifications from TMA TCP Gateway on UNIX to a mainframe
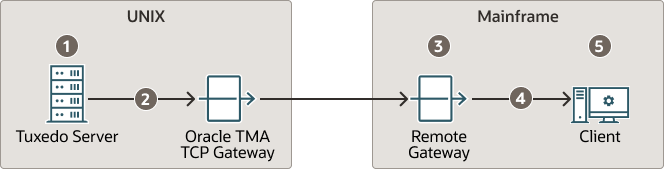
Figure 3-1 Security Checking for UNIX to Mainframe Transactions

- Verify the user is valid on UNIX. For valid users, access is given; for invalid users, access is rejected.
- Verify user name (reviewing the
tpusrfile), group (reviewing thetpgrpfile), and ACL (reviewing thetpaclfile). If all three pass, the transaction request processes. If any one of the three are rejected, the transaction request stops and a security violation occurs.Note:
The user IDs in these files must match in the Tuxedo and the mainframe environments or a security violation occurs. - Accept the transaction request at the mainframe gateway based on the request coming from a trusted source. No password is passed.
- Verify the user name associated with the transaction against the security system (such as RACF). If the user name is not valid, the request is rejected and a security violation occurs.
- Complete the transaction request to the server.