Group LDAP Mapper and Role Assignment
Group Mapper
The Group Mapper allows you to configure group mappings from LDAP into cncc-iam group mappings. Group mapper can be used to map LDAP groups from a particular branch of an LDAP tree into groups in cncc-iam. It also propagates user-group mappings from LDAP into user-group mappings in cncc-iam.
- Click Configure and select User Federation. Click
ldap (Console Display Name) and select the Mappers tab,
and click Create.
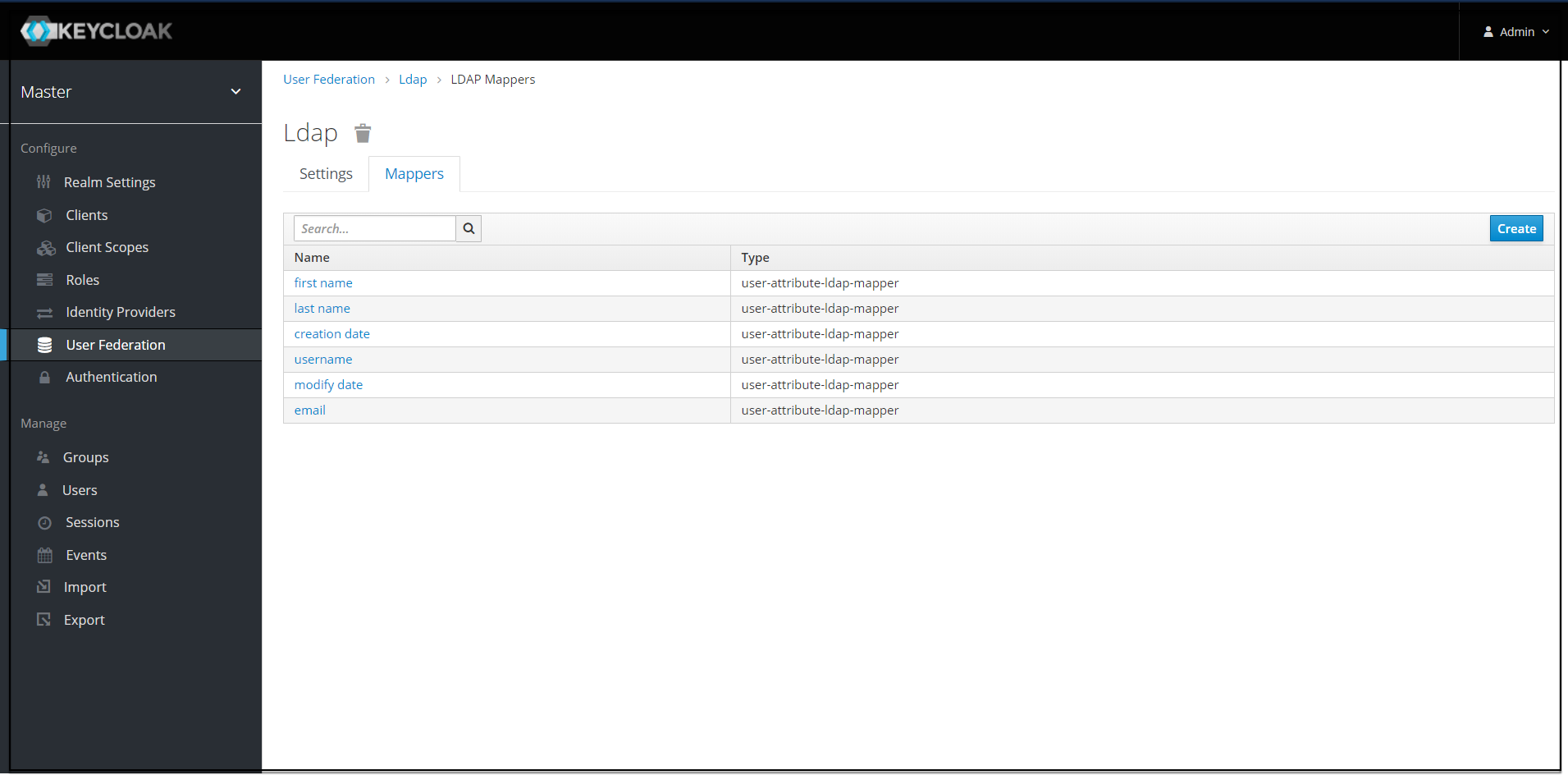
- The Add User
federation mapper page appears. Give an appropriate name for the
field Name. Select
'group-ldap-mapper' as Mapper Type drop down menu. Click Save.
The following screen appears.
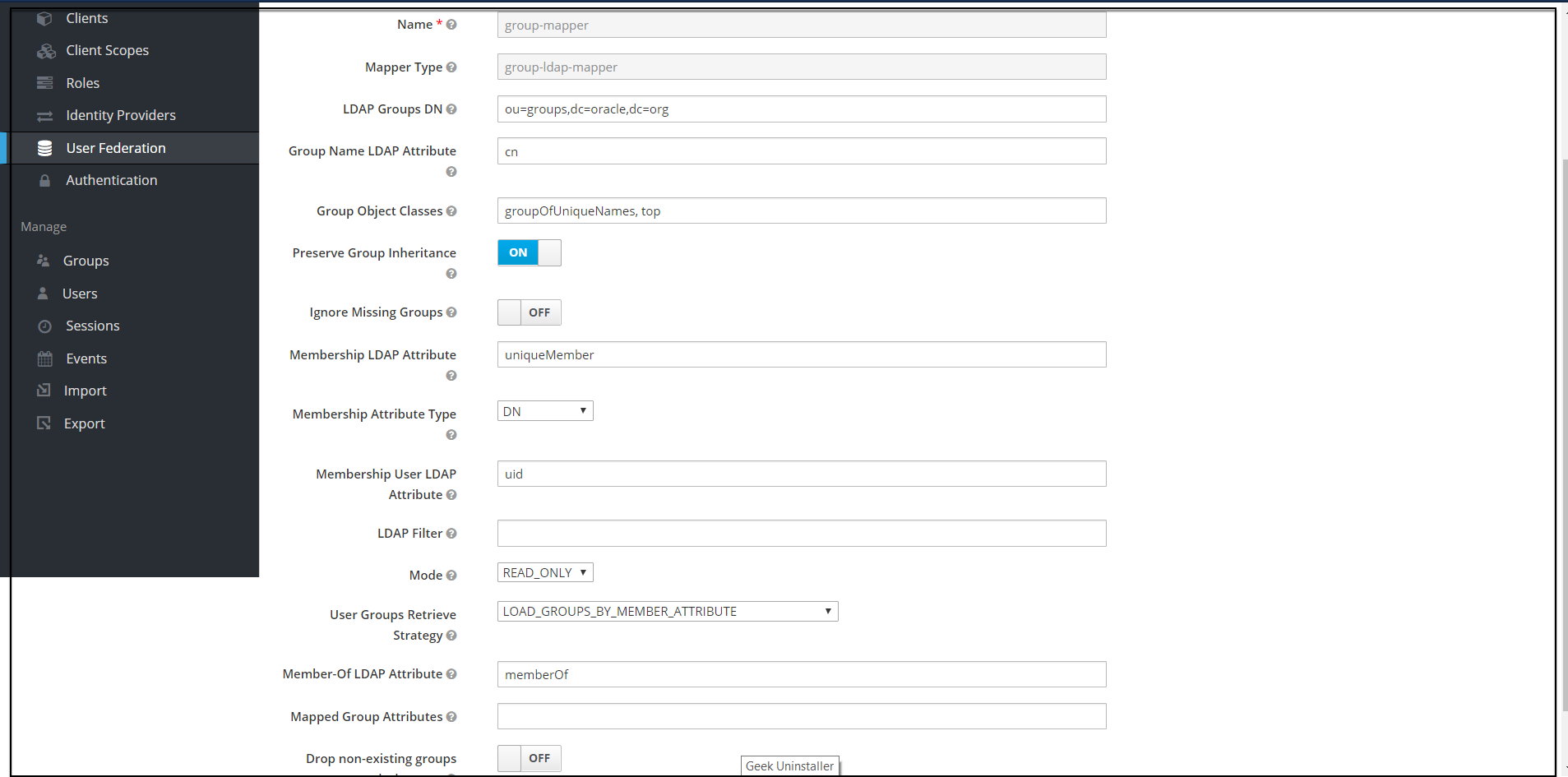
Note:
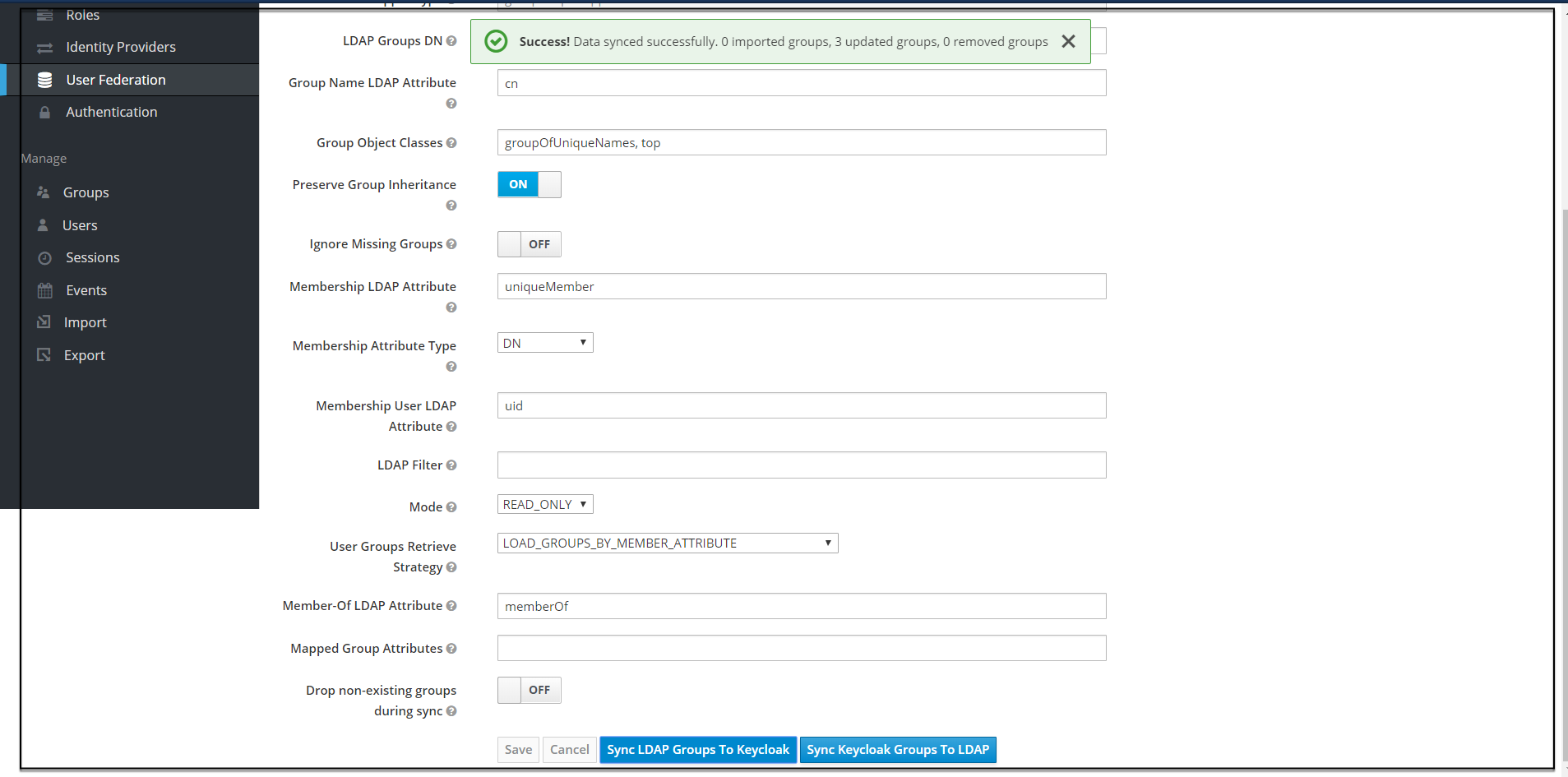
When selected, default values will be set by cncc-iam. But you need change some values based on your ldap records. - Click Save. New buttons appears next to the Save and Cancel. They are Synchronize LDAP Groups
to Keyclaok and Synchronize Keyclaok Groups to LDAP.
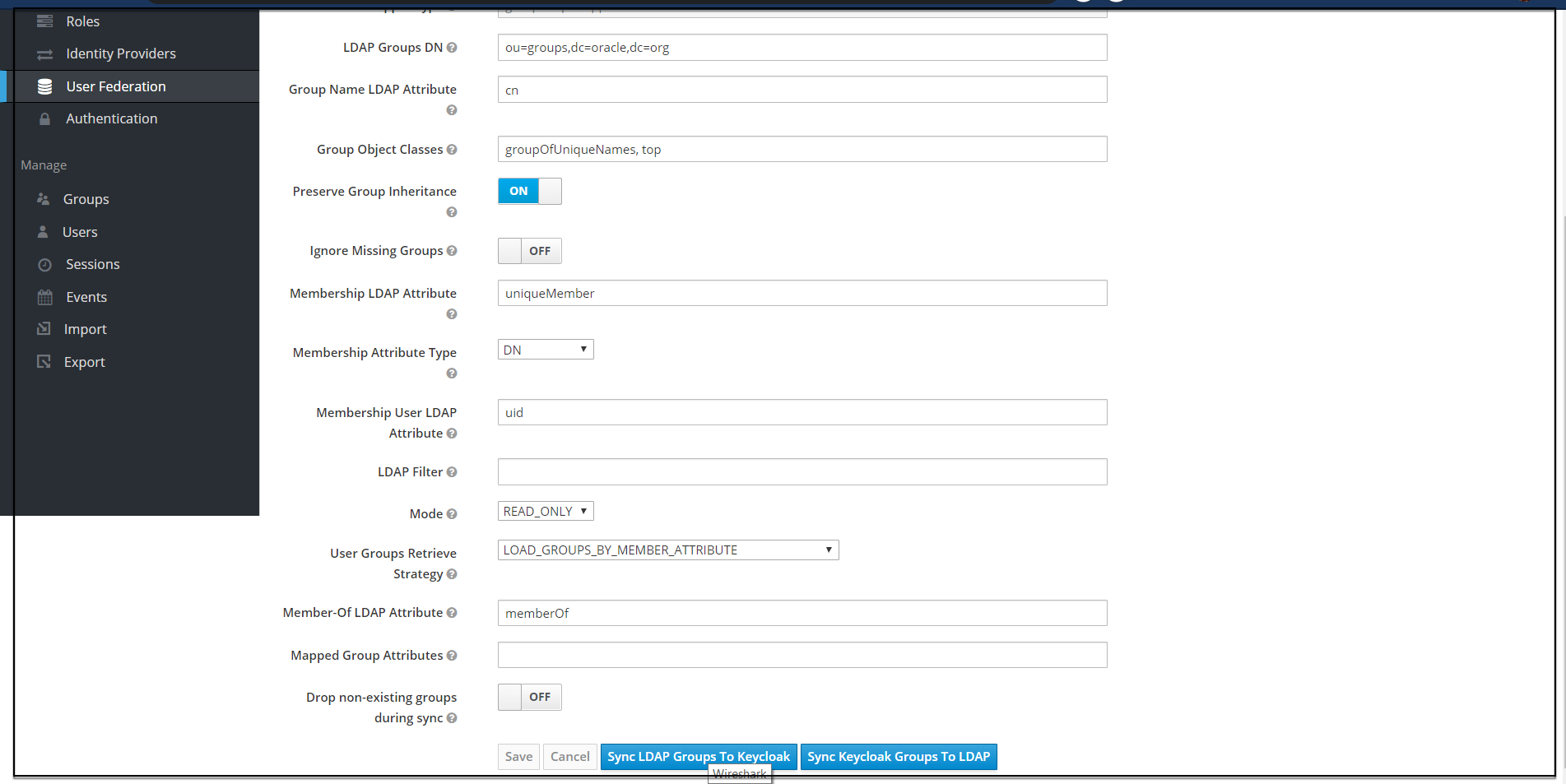
- Click Synchronize LDAP Groups
to Keyclaok. The success message appears with the number of groups
imported and so on.
Note:
If this step fails then you might need to check to the trouble shooting section and look at cncc-iam logs in debug mode. - Select the Groups in the left pane and click the View all groups in
the right pane.
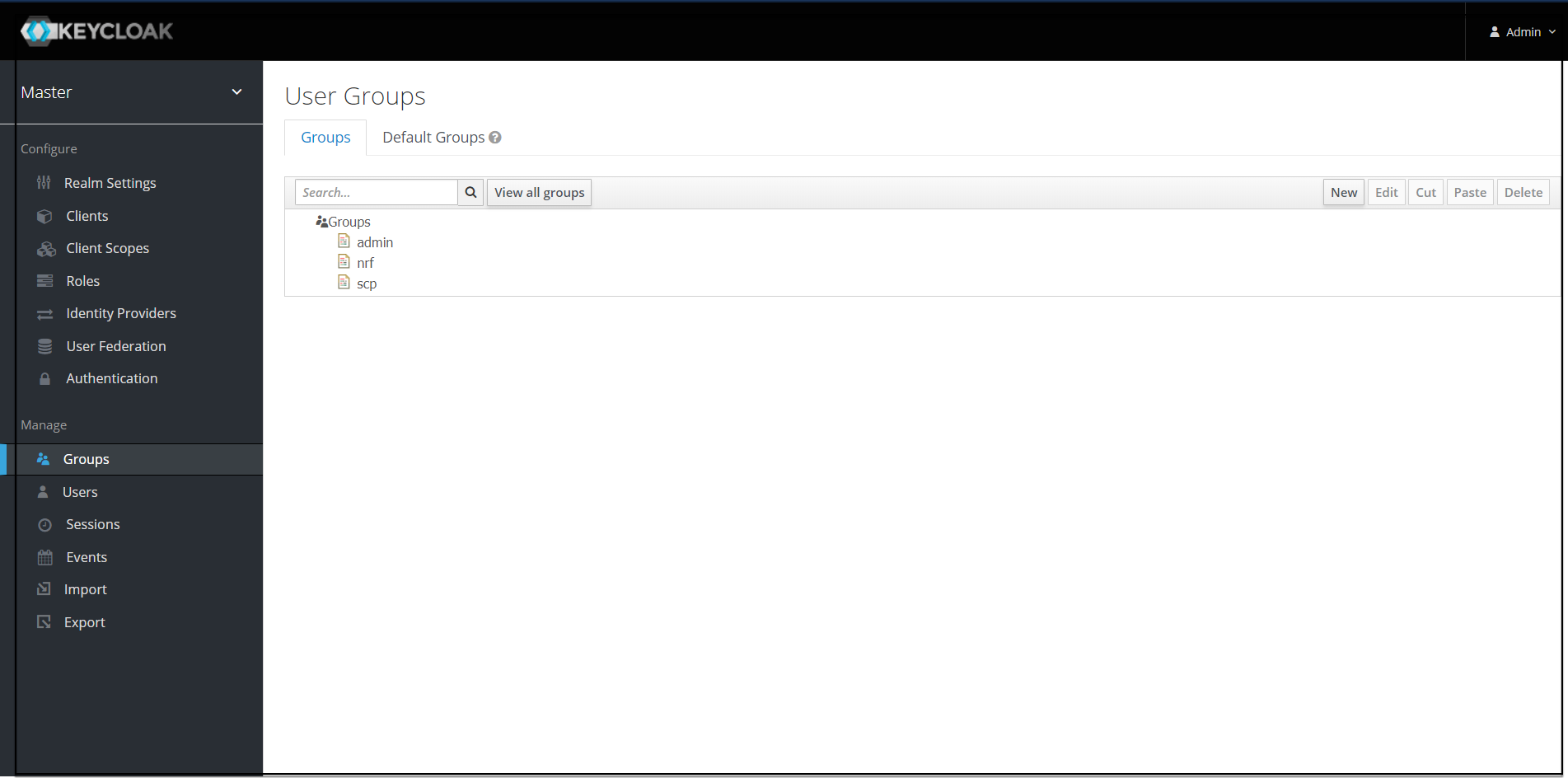
- Click any group and click Edit. The following
tabs appear: Settings,
Attributes, Role Mappings, and Members.
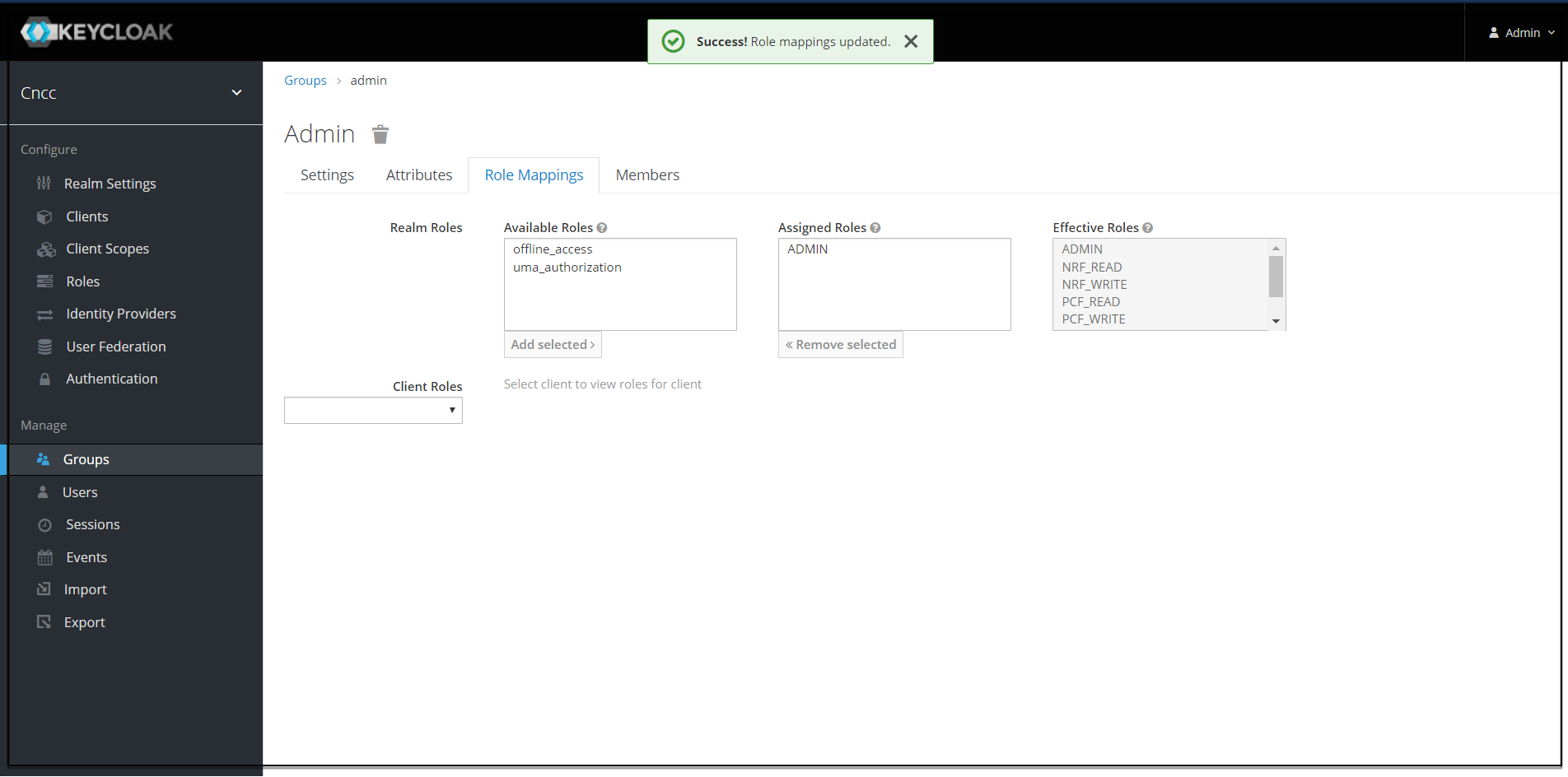
- Select Role Mapping tab to see a list of roles that are pre-defined in cncc-iam.
- Select one or more roles from Available Roles and assign it to the group. For example, If group "admin" is assigned with role "ADMIN", it means that any user which belongs to the admin group will be automatically assigned the admin role which allows him to access all the NF resource of CNC console that it supports.
- Once done you can test authentication and authorization by logging into CNC Console GUI.
Note:
- When the password of user is updated from CNCC-IAM and sent to LDAP, it is always sent in plain-text. This is different from updating the password to built-in CNCC-IAM database, when the hashing and salting is applied to the password before it is sent to DB. In the case of LDAP, the CNCC-IAM relies on the LDAP server to provide hashing and salting of passwords.
- Most of LDAP servers (Microsoft Active Directory, RHDS, FreeIPA) provide this by default. Some others (OpenLDAP, ApacheDS) may store the passwords in plain text by default and user need to explicitly enable password hashing for them.
Note:
For more information about the user roles, refer APPENDIX.