2 CNC Console Features
This section explains about the CNC Console features.
Support for Network Functions
CNC Console GUI provides a user interface to configure and manage the following network functions:
Binding Support Function (BSF)
- Allows PCF users to register, update, and remove the binding information
- Allows network function consumers to retrieve the binding information
For more information about configuring parameters, see the Configuring BSF Using CNC Console section in Oracle Communications Cloud Native Core Binding Support Function User Guide.
Data Director (DD)
Oracle Communications Data Director (OCDD) is a Network Data Broker (NDB) in the 5G core network. OCDD receives the network traffic data from various sources such as 5G NFs, Non-5G nodes, third-party producers and sends the filtered and consolidated data securely to the subscribed consumers, which are 3rd party consumer applications or platforms.
Data collection is a complex task in a 5G Service Based Architecture (SBA). The data collected must be correlated to provide meaningful insights to the customers. The OCDD can filter, replicate, aggregate data and route these data feeds to 3rd party consumers who have subscribed to the feeds. OCDD ensures data security, low latency and redundancy while collecting and processing the data feeds. The OCDD enables the communications service providers (CSP) to correlate and transform the acquired data as per their data feed configuration to create comprehensive dashboards and Key Performance Indicators (KPIs) and thereby achieve meaningful insights about all functions in the 5G network. This information can be used for monetizing, providing good quality of service for the user, reducing downtime, ensuring easy network scalability and minimizing losses. The OCDD generated data feed can be beneficial for monitoring and troubleshooting during a network failure. OCDD is a crucial function which aids in creating self-healing networks.
Network Repository Function (NRF)
OCNRF provides the following functions:
- Maintains the profiles of the available NF instances and their supported services in the 5G core network.
- Allows consumer NF instances to discover other provider's NF instances in the 5G core network.
- Allows NF instances to track the status of other NF instances.
- Provides OAuth2 based Access Token service for consumer NF authorization.
- Provides specific NF Type selection based on subscriber identity.
- Supports forwarding of messages from one NRF to another NRF.
- Supports georedundancy to ensure service availability.
The OCNRF interacts with every other NF in the 5G core network and it supports the above functions through the following services:
- Management Service
- Discovery Service
- Access Token Service
CNC Console provides an interface to configure global and service parameters in NRF.
For more information about configuring parameters, see the Configuring NRF Using CNC Console section in Oracle Communications Cloud Native Core Network Repository Function User Guide.
Network Slice Selection Function (NSSF)
NSSF provides the following functions:
Network slices enable the users to select customized networks with different functionalities (such as mobility) and performance requirements (such as latency, availability and reliability). Network slices differ in features supported and network function optimizations. In such cases, network slices may have different S-NSSAIs with different slice and service types. The user can deploy instances of multiple network slices delivering the same features but for different groups of User Equipments (UEs). These instances deliver different committed services as they are dedicated to a customer. The network slices may have different S-NSSAIs with the same slice or service type but different slice differentiators. The OCNSSF fulfills the requirement for determining the individual network function pertaining to a slice.
OCNSSF is a functional element that supports the following functionalities:- OCNSSF enables the Access and Mobility Management Function (AMF) to perform initial registration and Protocol Data Unit (PDU) session establishment.
- AMF can retrieve NRF, NSI ID, and target AMFs as part of UE initial registration and PDU establishment procedure.
- OCNSSF uses an NF Service Consumer (AMF) to update the S-NSSAI(s) that AMF supports and notifies of any changes in the status.
- OCNSSF selects the network slicing instance (NSI) and determines the authorized Network Slice Selection Assistance Information (NSSAIs) and AMF to serve the UE.
- OCNSSF interaction with NRF allows retrieving specific NF services to be used for registration request.
OCNSSF provides the following information when queried by the AMF:
- Allowed NSSAIs
- Configured NSSAIs
- Restricted NSSAIs
- Candidate AMF List (in case of registration)
- Network Slice instance ID (for PDU session establishment)
- Slice-level NRF information (for PDU Connectivity)
OCNSSF supports the above functions through the following NSSF services:
- NS Selection service (Nnssf_NSSelection): This service is used by an NF Service Consumer (AMF) to retrieve the information related to network slice. It enables network slice selection in the serving Home Public Land Mobile Network (HPLMN).
- NS Availability Service (Nnssf_NSAvailability): This service stores and maintains list of supported S-NSSAIs per TA. It allows NF service Consumer (AMF) to update and subscribe the above data and get notifications for any addition or deletion of supported S-NSSAIs.
CNC Policy
-
CNC Policy is a network function for policy control decision and flow based charging control. It consists of the following functions:
- Policy rules for application and service data flow detection, gating, QoS, and flow based charging to the Session Management Function (SMF)
- Access and Mobility Management related policies to the Access and Mobility Management Function (AMF)
- UE Route Selection Policies (URSP) rules to User Equipement (UE) through AMF
- Access to subscription information relevant for policy decisions in a Unified Data Repository (UDR)
- Network control for service data flow detection, gating, and Quality of Service (QoS)
- Flow based charging towards the Policy and Charging Enforcement Function (PCEF)
- Receiving session and media related information from Application Function (AF) and informing AF of traffic plane events
- Provision of Policy and Charging Control (PCC) Rules to Policy and Charging Enforcement Function (PCEF) through the Gx reference point
- Session Management Service
- Access and Mobility Service
- Policy Authorization Service
- User Equipment (UE) Policy Service
- PCRF Core Service
CNC Console provides an interface to configure policies and manageable objects in CNC Policy.
For more information about configuring parameters, see the Configuring CNC Policy Using CNC Console section in Oracle Communications Cloud Native Core Policy User Guide.
Service Communication Proxy (SCP)
SCP provides the following functionalities to other 5G Network Functions (NFs):
- Routing/Selection: Routing rules, refresh cache, and handle
application failures and redirects.
- Dynamic Discovery: The 5G topology is determined from Network Repository Function (NRF) and creation of routing rules.
- Static Configuration: Enables NF Profiles configuration.
- Load Balancing: Load balancing based on static capacity, NF Type, NF Specific, and NF Priority as mentioned in the NF Profile.
- NF Subscription: Subscription for all NF types.
- Circuit Breaking: Initiated on a per FQDN basis when outstanding transactions exceed a configurable value.
- Message Priority : Message Priority assignment and override based on the 3GPP-SBI-Message-Priority header.
- Congestion and Overload: Uniform load balancing and routing strategy across the network and protects the pod from overload related to various system resources.
CNC Console provides an interface to configure the SCP features.
For more information about configuring parameters, see the Configuring SCP Using CNC Console section in Oracle Communications Cloud Native Core Service Communication Proxy User Guide.Security Edge Protection Proxy (SEPP)
OCSEPP supports the following functionalities:
- Protects application layer control plane messages and sensitive
data between two NFs belonging to different PLMNs that use the N32 interface to
communicate with each other. The N32 interface is used between the SEPPs of a
VPLMN and a HPLMN in roaming scenarios. 3GPP has specified N32 to be considered
as two separate interfaces: N32-c and N32-f.
- N32-c is the Control Plane interface between the SEPPs for performing the initial handshake and negotiating the parameters to be applied for the actual N32 message forwarding.
- N32-f is the Forwarding interface between the SEPPs, that is used for forwarding the communication between the Network Function (NF) service consumer and the NF service producer after applying the application level security protection.
- Provides secure communication of Inter PLMN messages from Consumer NF to Producer NF using TLS protection mode (HTTP over TLS)
- Supports configuration of roaming partner profiles using REST API
- Performs mutual authentication and negotiation of cipher suites with the SEPP in the roaming partner’s network
- Handles key management aspects that involve setting up the required cryptographic keys needed for securing messages on the N32 interface between two SEPPs
- Provides a single point of access and control to internal NFs
- Validates inbound traffic as to whether it is from an authorized external PLMN
- Supports cross-layer validation of source and destination addresses and identifiers to provide anti-spoofing capabilities
CNC Console provides an interface to configure different services in SEPP.
For more information about configuring parameters, see the Configuring SEPP Using CNC Console section in Oracle Communications Cloud Native Core Security Edge Protection Proxy User Guide.Unified Data Repository (UDR)
- Leverages a common Oracle Communications Cloud Native Framework
- Is compliant to 3GPP 29.505 Release 15 specification UDM
- Is compliant to 3GPP 29.519 Release 16 (backward compatible with Release 15) specification for PCF
- Has tiered architecture providing separation between the connectivity, business logic, and data layers
- Uses Oracle MySQL NDB Cluster CGE Edition as backend database in the Data Tier
- Registers with NRF in the 5G network so that the other NFs in the network can discover UDR through NRF
- Registers UDR with services like DR-SERVICE and GROUP-ID-MAP
CNC Console provides an interface to configure global and service parameters in UDR.
For more information about configuring parameters, see the Configuring UDR Using CNC Console section in Oracle Communications Cloud Native Core Unified Data Repository User Guide.Managing CNC Console Support for NF GUI
Enable and Configure each NF
See CNC Console Supported NF Configurations in Oracle Communications Cloud Native Core Console Installation and Upgrade Guide for more details about enabling and configuring NFs .
Observe
For information on Metrics and KPIs, see CNC Console Metrics, and CNC Console KPIs sections.
Maintain
If you encounter alerts at system or application levels, see CNC Console Alerts section for resolution steps.
- Collect the logs: For more information on how to collect logs, see CNC Console Logs.
- Raise a service request: See My Oracle Support for more information on how to raise a service request.
Support for OCCNE Common Services
CNC Console Common Services GUI provides an option to enable cards (hyperlinks) for OCCNE Common services and OSO services.
CNE Common Services
CNC Console Common Services GUI provides an option to enable cards (hyperlinks) for OCCNE Common services such as Grafana, Kibana, Jaeger, Prometheus and AlertManager.
OSO Common Services
CNC Console Common Services GUI also provides an option to enable cards (hyperlinks) for OSO services such as Prometheus and AlertManager.
Managing Common Service Support (OSO Cards and CNE Cards)
Enable and Configure
Observe
For information on Metrics and KPIs, see CNC Console Metrics, and CNC Console KPIs sections.
Maintain
If you encounter alerts at system or application levels, see CNC Console Alerts section for resolution steps.
- Collect the logs: For more information on how to collect logs, see CNC Console Logs.
- Raise a service request: See My Oracle Support for more information on how to raise a service request.
LDAP Integration
The Lightweight Directory Access Protocol (LDAP) is a protocol that defines the technique for accessing the directory data.
Figure 2-1 LDAP
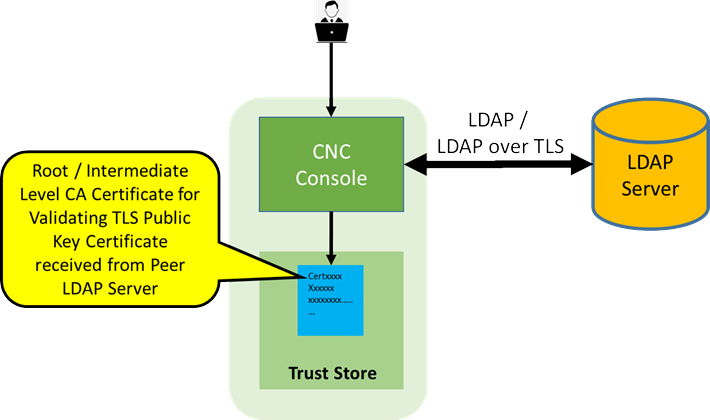
The CNC Console IAM is used as an integration platform to connect it into existing Lightweight Directory Access Protocol (LDAP) and Active Directory (AD) servers.
CNC Console IAM can combine existing external user databases having user and credential details. You can integrate the CNC Console IAM to perform validation of these user credentials and pull in the identity information.
CNC Console IAM provides LDAP over TLS support to securely communicate with external LDAP and active directory servers.
CNC Console IAM also supports Lightweight Directory Access Protocol Secure (LDAPS) between the client and server to make the communication secure.
Managing LDAP Integration
Enable and Configure
Observe
For information on Metrics and KPIs, seeCNC Console Metrics, and CNC Console KPIs sections.
Maintain
If you encounter alerts at system or application levels, see CNC Console Alerts section for resolution steps.
- Collect the logs: For more information on how to collect logs, see CNC Console Logs.
- Raise a service request: See My Oracle Support for more information on how to raise a service request.
SAML 2.0 Integration
SAML (Security Assertion Markup Language) enables applications to authenticate a user using an identity provider. CNC Console can broker identity providers based on the SAML v2.0 protocol.
Managing SAML 2.0 Integration with CNC Console
Enable and Configure
Observe
For information on Metrics and KPIs, see CNC Console Metrics, and CNC Console KPIs sections.
Maintain
If you encounter alerts at system or application levels, see CNC Console Alerts section for resolution steps.
- Collect the logs: For more information on how to collect logs, see CNC Console Logs.
- Raise a service request: See My Oracle Support for more information on how to raise a service request.
Logging Support
- Regular logs
- Audit logs
- Security logs
Regular logs
These logs contain all kinds of error messages, warnings, or other events written within the application which provide logical, high level information about the application and ongoing events.
{"level": "INFO","message": "Started GatewayApplication in 10.748 seconds (JVM running for 12.825)"}
{"level": "INFO","message": "Creating plain httpClient"}
{"level": "INFO","message": "Creating plain restTemplate"}
{"level": "ERROR","message": "Can't get cfgs of topic public.dynamic.datamodel, exception is:\n
javax.ws.rs.ProcessingException: java.net.ConnectException: Connection refused (Connection
refused)"}Audit Logs
These logs contain user related information and the activity within the system.
^[[0m^[[33m10:12:57,388 WARN [org.keycloak.events] (default task-3) type=LOGIN_ERROR, realmId=master, clientId=security-admin-console,
userId=ef58d62e-a0a8-4f4e-bcc6-abccf917641c, ipAddress=192.168.203.108, error=invalid_user_credentials, auth_method=openid-connect, auth_type=code,
redirect_uri=http://10.75.240.33:30085/cncc/auth/admin/master/console/,
code_id=3e6d822a-9e82-4660-bb01-a814f7ae8f97, username=admin,
authSessionParentId=3e6d822a-9e82-4660-bb01-a814f7ae8f97,
authSessionTabId=2ak6Xwal-28Security Logs
These logs contain the header, payload, method, scheme, URI, and other details for all the requests and corresponding responses.
Disabling Security Logs
# CNCC configuration
cncc:
enabled: false
enablehttp1: false
securityLogEnabled: falseLog Levels
The log level indicates the level of the logs.
The default log levels for CNC Console Core is as follows:
ingress-gateway:
log:
level:
cncc:
root: WARN
audit: INFO
security: INFOThe default log levels for CNC Console IAM is as follows:
ingress-gateway:
log:
level:
cncc:
root: WARN
security: INFOManaging Security Logs and Audit Logs
Enable and Configure
Observe
For information on Metrics and KPIs, see CNC Console Metrics, and CNC Console KPIs sections.
Maintain
If you encounter alerts at system or application levels, see CNC Console Alerts section for resolution steps.
- Collect the logs: For more information on how to collect logs, see CNC Console Logs.
- Raise a service request: See My Oracle Support for more information on how to raise a service request.
Support for Multi Cluster Deployment
Multi cluster is a method of deploying an application on or across multiple Kubernetes clusters for improving availability, isolation, and scalability.
Support for Multicluster Deployment for NFs
CNC Console supports NF deployment across Kubernetes clusters using Manager CNC Console IAM (M-CNCC IAM), Manager CNC Console Core (M-CNCC Core), and Agent CNC Console Core (A-CNCC Core). In a multicluster deployment, the CNC Console can manage NFs and OCCNE common services deployed in the remote Kubernetes clusters.
Support for Multiple Instances of NFs within a cluster
CNC Console supports multiple instances of NFs within a Kubernetes cluster using Manager CNC Console IAM (M-CNCC IAM), Manager CNC Console Core (M-CNCC Core), and Agent CNC Console Core (A-CNCC Core).
The support for multi cluster deployment mTLS Configuration is added to provide secure communication between CNC Console Master and Agent.
Selecting the Instance
CNC Console multi cluster deployment has introduced a drop-down on header pane for selecting instance.
Values configured in M-CNCC Core instances section gets displayed in the drop down. Naming conversion used for instance drop down display is <owner>.<type>.<instance id>
Figure 2-2 Selecting the Instance
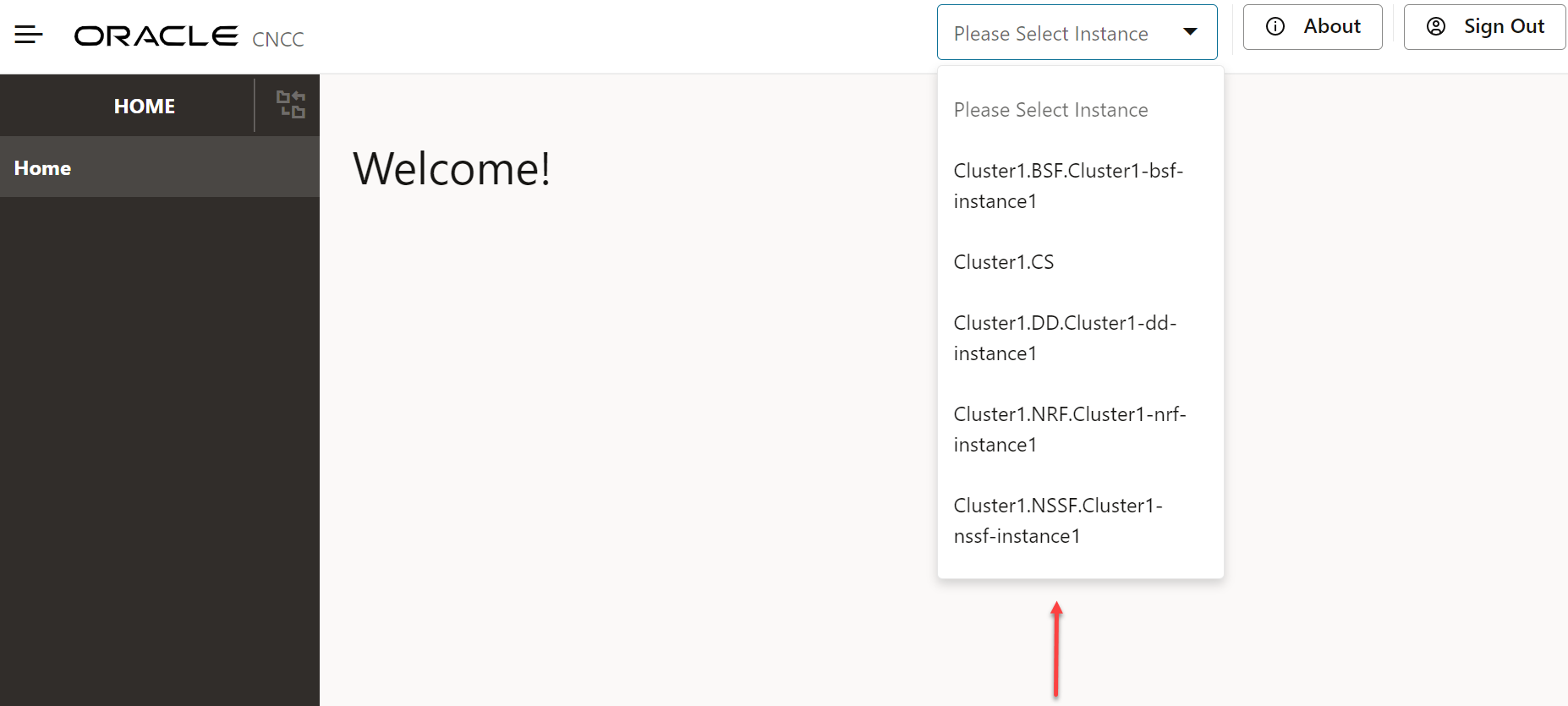
Figure 2-3 Loading the Menu
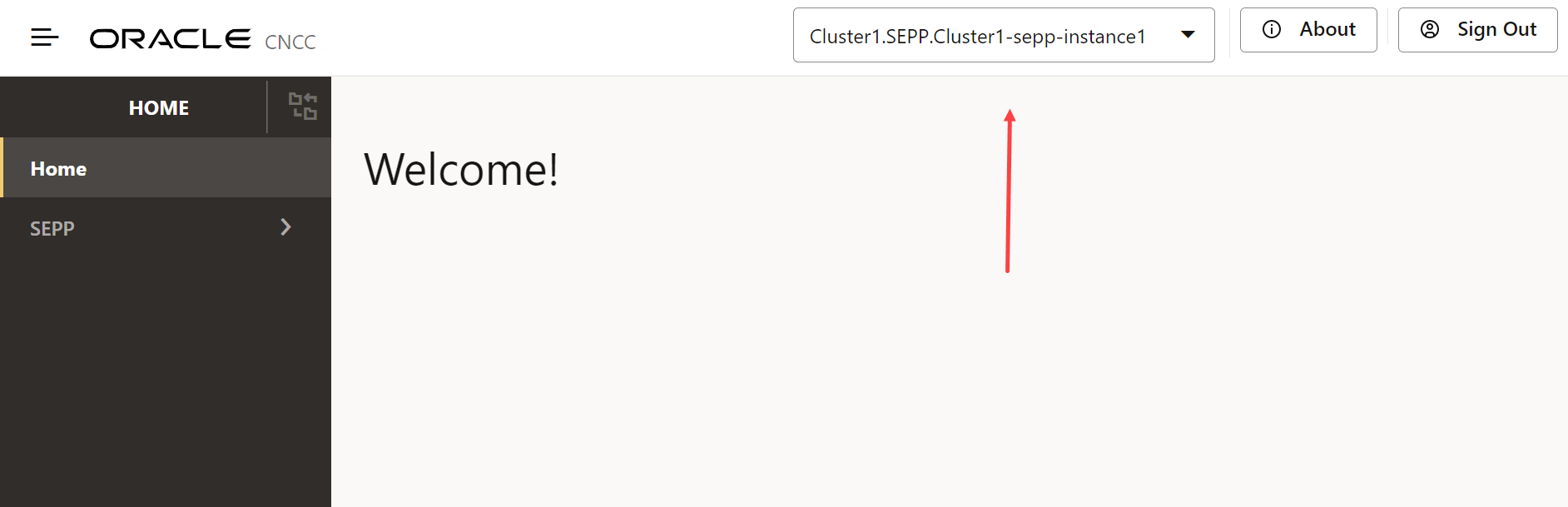
The common service instances configured in the instances section
gets displayed in the drop down.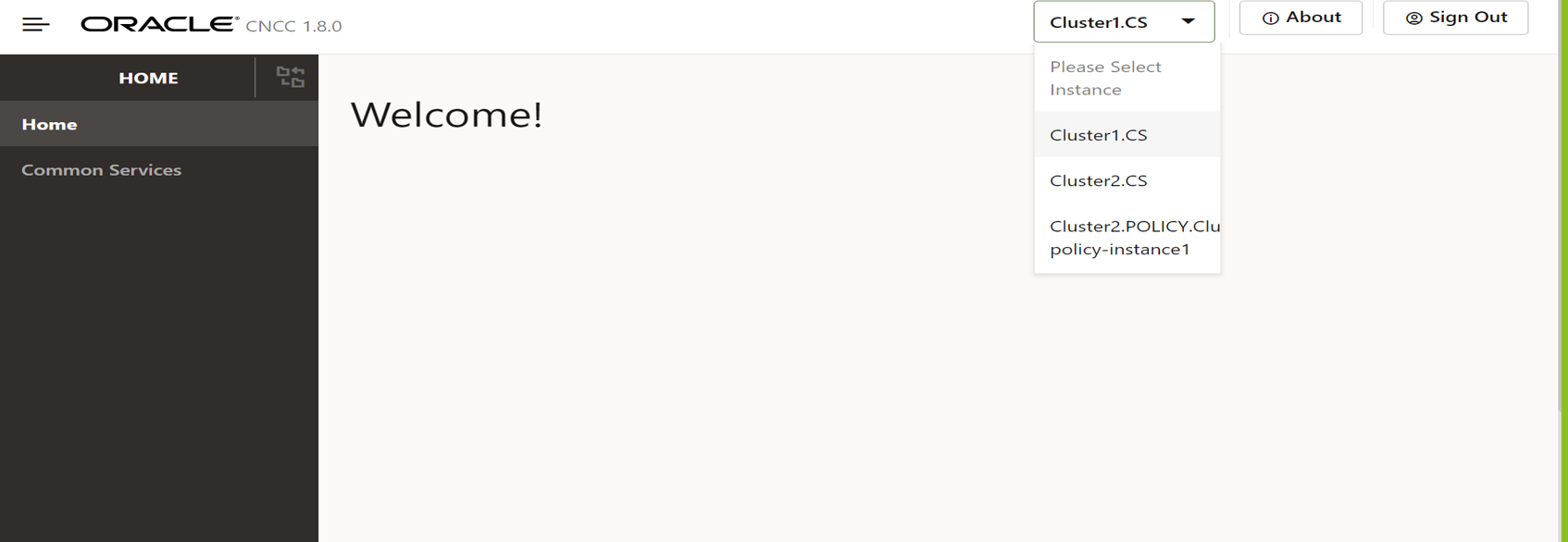
cnDBTier Integration
CNC Console is integrated with cnDBTier in a containerized Oracle Communications Cloud Native Environment. For more information, see Oracle Communications cnDBTier Installation Guide.
TLS Certificate Support
Transport Layer Security (TLS) certificates or Secure Sockets Layer (SSL) are essential to securing internet browser connections and transactions through data encryption. TLS/SSL is the standard security technology that works behind the scenes to keep the online transactions and logins secure. HTTPS enables end to end encryption of messages to ensure security of data. HTTPS requires creation of TLS (Mutual TLS by two way exchange of ciphered keys).
HTTPS requires creation of TLS (Mutual TLS by two way exchange of ciphered keys).
Steps to Enable HTTPS
Certificate CreationTo create certificate you must have the following files:
- ECDSA private key and CA signed certificate of OCNRF (if initial algorithm is ES256)
- RSA private key and CA signed certificate of OCNRF (if initial algorithm is RSA256)
- TrustStore password file
- KeyStore password file
- CA certificate
Secret Creation
$ kubectl create secret generic occnccaccesstoken-secret --from-file=ecdsa_private_key_pkcs8.pem --from-file=rsa_private_key_pkcs1.pem --from-file=trustStorePassword.txt --from-file=keyStorePassword.txt --from-file=ecdsa_occncc_certificate.crt--from-file=rsa_occncc_certificate.crt -n occnccCertificate and Key Exchange
Once the connection is established between the client and the server, using the agreed algorithm and keys, they can send messages securely to each other. The TLS handshake has the following phases:
- Hello
- Certificate Exchange
- Key Exchange
The client generates a random key to be used for the main, symmetric algorithm. The client encrypts the key using an algorithm also agreed upon the server’s public key (found on its SSL certificate). The client sends this encrypted key to the server, where it is decrypted using the server’s private key. The parties are identified that they are talking to the right person, and have secretly agreed on a key to symmetrically encrypt the data that they are about to send each other. The HTTP requests and responses can be sent by forming a plain text message and then encrypting and sending it. The other party is the only one who knows how to decrypt this message, and so Man In The Middle Attackers are unable to read or modify any requests that they may intercept.
CNC Console supports the following cipher suites:
- TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384 - TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 - TLS_ECDHE_RSA_WITH_CHACHA20_POLY1305_SHA256 - TLS_DHE_RSA_WITH_AES_256_GCM_SHA384 - TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256 - TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
Service Mesh Communication
CNC Console leverages the Istio or Envoy service mesh (Aspen Service Mesh) for all internal and external communication. The service mesh integration provides Console-NF communication and allows API gateway co-working with service mesh. The service mesh integration supports the services by deploying a special sidecar proxy in the environment to intercept all network communication between microservices.
For more information, see CNC Console Configuration to Support ASM and OSO in Oracle Communications Cloud Native Core Console Installation and Upgrade Guide.