5 Accessing NF Configurations through CNC Console IAM
CNC Console IAM REST API provides a secure option to access NF resources through access token. This chapter describes how to generate and refresh access tokens through CNC Console IAM REST API. You can generate access tokens through the CNC Console IAM REST API by using curl or Postman. Once the access token is generated, CNC Console will be able to access the required NF resources.
5.1 Generate Access Tokens
CNCC IAM provides a REST API for generating and refreshing access tokens.
You must use cncc-api-access client for accessing NF resources through REST APIs. For security reasons, Direct Access Grants Enabled is set to OFF by default.
Perform the following steps to set Direct Access Grants Enabled to ON.
- Log in to CNC IAM with valid credentials.
- Click the cncc realm.
- On the right pane, click Clients. The following screen
appears:
Figure 5-1 Clients

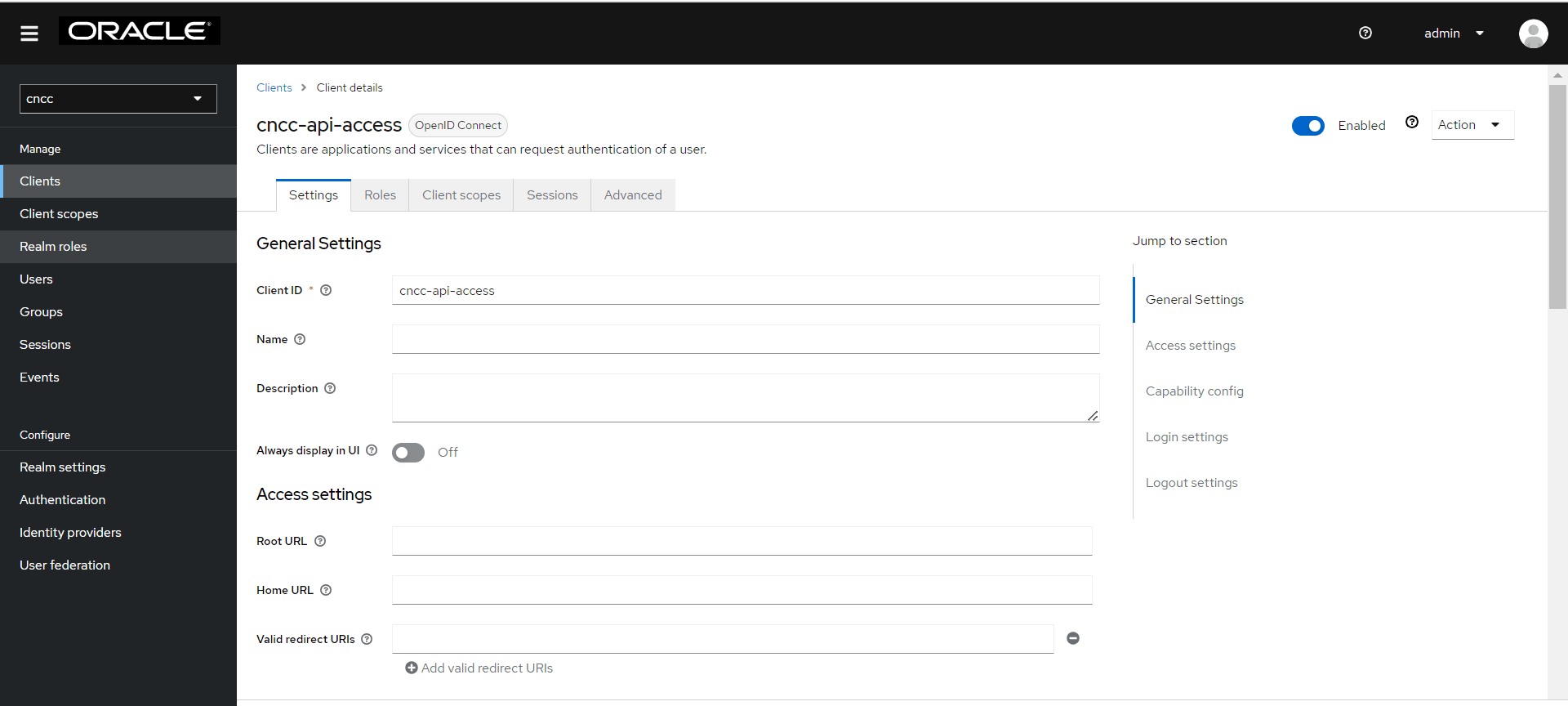
- Click cncc-api-access. The following screen appears.
Figure 5-2 Cncc-api-access
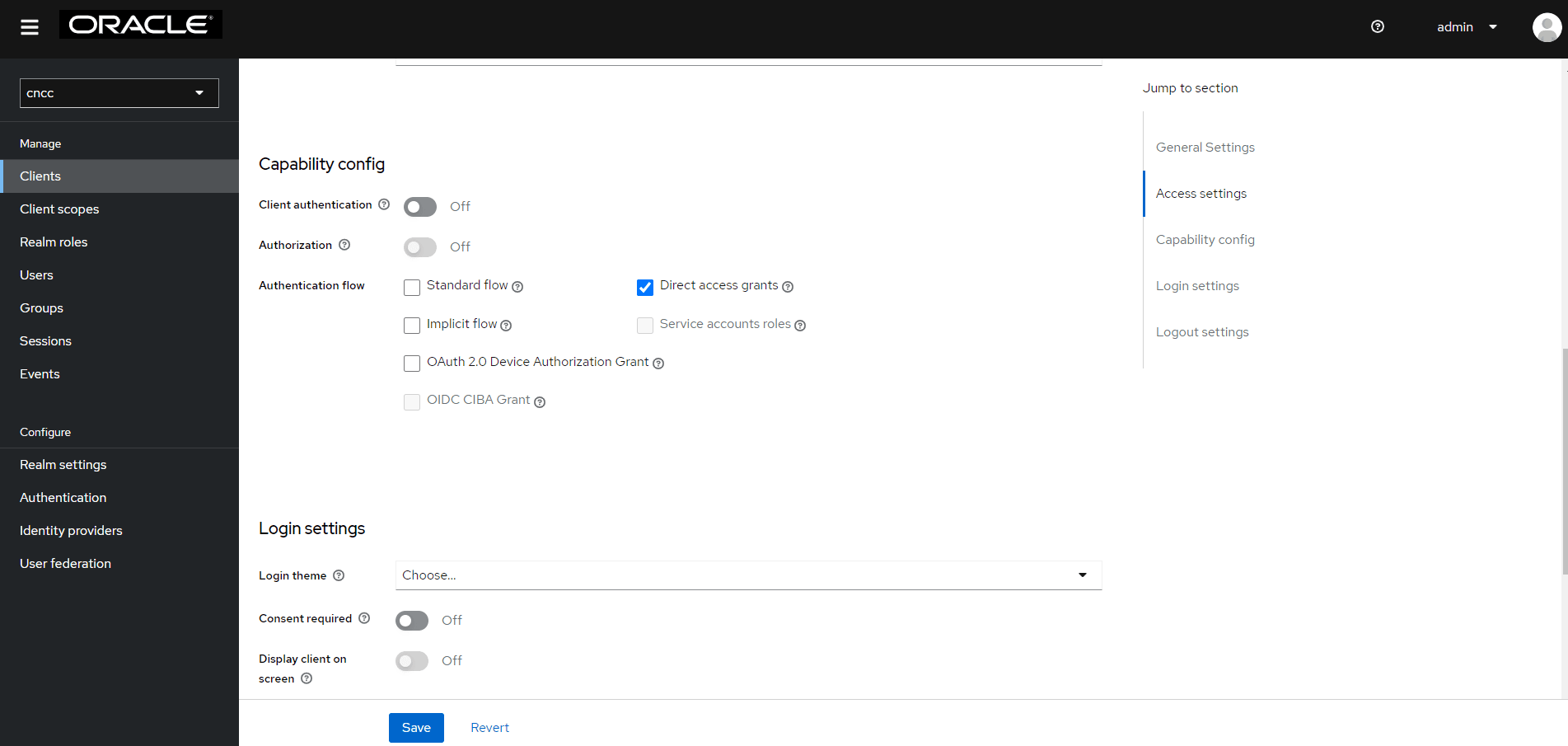
- Navigate to the Capability Config section in the Settings tab and
select the Direct Access Grants checkbox. Click Save.
Figure 5-3 Direct Access Grants
Perform the following procedure to generate the access tokens:
- Acquire an access token from CNC Console IAM by sending a POST
request to the following URL:
http://${cncc-iam-ingress-extrenal-ip}:${cncc-iam-ingress-service-port}/cncc/auth/realms/${realm}/protocol/openid-connect/tokenExample:
http://10.75.182.79:8080/cncc/auth/realms/cncc/protocol/openid-connect/token - The body of the request must be x-www-form-url encoded as
follows:
'client_id': 'your_client_id', 'username': 'your_username', 'password': 'your_password', 'grant_type': 'password' Example: 'client_id': 'cncc-api-access', 'username': 'user1', 'password': '******', 'grant_type': 'password' - The Curl Command to access the token is as follows:
curl --location --request POST 'http://${cncc-iam-ingress-extrenal-ip}:${cncc-iam-ingress-service-port}/cncc/auth/realms/cncc/protocol/openid-connect/token' \ --header 'Content-Type: application/x-www-form-urlencoded' \ --data-urlencode 'grant_type=password' \ --data-urlencode 'username=user1' \ --data-urlencode 'password=<password value>' \ --data-urlencode 'client_id=cncc-api-access' - In response, you will get an access_token and a
refresh_token. The response is as follows:
{ "access_token": "eyJhbGciOiJSUzI1NiIsI................._LcCZYwDQJJTloj2PJ8y1WjO9l2Q", "expires_in": 300, "refresh_expires_in": 1800, "refresh_token": "eyJhbGciOiJIUzI1NiIs ................ldUIiwia2lkIiA6ICI3YTFlYvKPF-ZIg", "token_type": "bearer", "not-before-policy": 0, "session_state": "6c42d978-14ac-4793-a1e3-789cfbdb2b74", "scope": "email profile" }Note:
M-CNCC IAM IP/FQDN which is used to generate access token and M-CNCC IAM IP/FQDN which is specified in custom-cncc_values.yaml should be the same.
5.2 Refresh Access Tokens
Perform the following procedure to refresh the access tokens:
If the access_token has expired, it can be refreshed by sending a POST request to the same URL as above; but the POST method must have the refresh token instead of username and password. The format is as follows:'client_id': 'your_client_id',
'refresh_token': refresh_token_from_previous_request,
'grant_type': 'refresh_token'
Example:
'client_id': 'cncc-api-access',
'refresh_token': 'eyJhbGciOiJIUzI1NiIs ................ldUIiwia2lkIiA6ICI3YTFlYvKPF-ZIg',
'grant_type': 'refresh_token'In response, you will receive a new access_token and refresh_token.
5.3 Accessing NF Resources
Perform the following procedure to access NF Resources:
To access NF Resources, you must use the access token in every request to an NF resource by placing it in the Authorization header.
The following headers are to be included while sending API request:
- Authorization : The access token should be used in every request to a NF resource by placing it in the Authorization header
- oc-cncc-id : M-CNCC uses the oc-cncc-id header to find the agent or master owning the instance.
- oc-cncc-instance-id : A-CNCC Core (or M-CNCC Core ) uses the oc-cncc-instance-id header to find the NF instance for routing.
Using CNC Console IAM API, the following headers need to be passed in curl/postman request while accessing NF resource:
curl --location --request GET 'http://${cncc-mcore-ingress-external-ip}:${cncc-mcore-ingress-service-port}/<NF API URI>' \
--header 'oc-cncc-id: oc-cncc-id value' \
--header 'oc-cncc-instance-id: oc-cncc-instance-id value' \
--header 'Authorization: Bearer <token>'Example: Using SCP Canary Release API, the following headers need to be passed in curl/postman request while accessing NF resource:
curl --location --request GET 'http://${cncc-mcore-ingress-external-ip}:${cncc-mcore-ingress-service-port}/ocscp/scpc-configuration/v1/canaryrelease ' \
--header 'oc-cncc-id: Cluster1' \
--header 'oc-cncc-instance-id: Cluster1-scp-instance1' \
--header 'Authorization: Bearer <token>'