2 Performing a Secure Installation
This chapter presents planning information for your Oracle Communications Design Studio installation, and describes recommended deployment topologies that enhance security.
For information about installing Design Studio, see Design Studio Installation Guide.
Understanding the Design Studio Environment
When planning your Design Studio implementation, consider the following:
-
Which resources need to be protected?
You need to protect customer data, such as credit card numbers, internal data, such as proprietary source code, and system components from external attacks and intentional overloads. Run-time archives and projects they are derived from need to be protected to prevent tampering and exposure of internal mechanics. Application components should have restricted access to help prevent creation of viral cartridges.
-
Who are you protecting data from?
You need to protect subscriber data from other subscribers and you need to analyze your workflows to determine who in your organization needs access to subscriber data. Design information needs to be protected from potential hackers since it could provide critical details enabling an attack. Access to data should be limited for run-time and design-time information. For example, can a system administrator manage your system components without needing to access the system data?
-
What happens if protections on strategic resources fail?
In some cases, a fault in your security scheme is easily detected and considered nothing more than an inconvenience. In other cases, a fault might cause great damage to you or your customers. Understanding the security ramifications of each resource will help you protect it properly.
Recommended Deployment Configurations
This section describes recommended deployment configurations for Design Studio.
Figure 2-1 Recommended Deployment Configuration
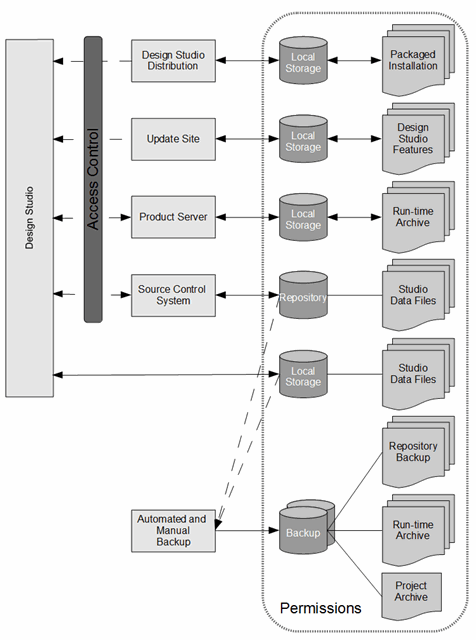
Description of "Figure 2-1 Recommended Deployment Configuration"
Table 2-1 Design Studio Deployment Recommendations
| Component | Recommendation |
|---|---|
|
Design Studio |
Limit application and project file permissions to the user. Enable user authentication and desktop locking. |
|
Design Studio Distribution |
When distributing Design Studio to users as a pre-packaged archive, use web/FTP server with access control. Limit distribution files access to the web/FTP server for download only. |
|
Update Site |
Use web/FTP server with access control. Limit update site file access to the web/FTP server for download only. |
|
Product Server |
Use Cartridge Management web service access control with limited functions. |
|
Source Control System |
Enable user authentication. Limit repository file access to the source control system. |
|
Automated/Manual Backup |
Control backup utility access. Limit backup file permissions to backup administrators only. |
Employ access control to components to limit use to privileged users. Configure Design Studio files and folders to provide limited permissions to the user or associated component only.
Additionally, carefully consider security requirements for the resources that you deploy to production servers. These run-time archives contain code and logic which execute on production servers. Use source control and access control on any run-time archives (and the cartridge projects which produce them) to protect against cartridge tampering.
Finally, protect against the misuse of cartridge management actions. Unauthorized development of viral cartridges and cartridge deployment, for example, can enable various forms of attack such as denial of service or theft of secure data. Protect against this type of incident by limiting access to the Design Studio application and to the cartridge management functions.
Operating System Security
See the following documents:
-
Windows Security Checklist at microsoft.com
-
Oracle Solaris Security for System Administrators
-
Guide to the Secure Configuration of Red Hat Enterprise Linux 5
-
Hardening Tips for the Red Hat Enterprise Linux 5
Cartridge Management Security
Design Studio interacts with product server components for cartridge management functions. Secure these interactions using secure connections. Oracle recommends that you install the product server components with secure connectivity enabled.
Enabling Secure Connectivity
Content contained in cartridge management messaging may include sensitive information. You can use Secure Sockets Layer (SSL) connections to protect against snooping during transport. Employ secure connection configuration for all interactions from Design Studio to the product server components.
See Design Studio System Administrator's Guide for more information about enabling SSL connections.
Ensure that you make the SSL keys available to Design Studio. The key store must include keys for any environment connection using SSL.
See "Studio Environment Editor Tab" in Design Studio Help.
See Oracle Fusion Middleware Securing a Production Environment for Oracle WebLogic Server.
Protecting Deployment Functions
The cartridge management functions should be configured to require user specific authentication credentials. The credentials should allow the minimum privileges necessary to enable the cartridge management functions.
Deployment scripts used for automated deployment should be protected from unauthorized use or tampering. The scripts and ability to execute them need to be restricted to authorized users and have permissions restricted based on the user role.
See Oracle Communications product installation documentation on the Cartridge Management web service for more information.
Secure Design Studio Installation
Design Studio installation includes a number of options for making Design Studio application components secure.
Consider each of the following sections for applicability to your Design Studio installations.
Secure Design Studio Update Site
If providing users access to the Design Studio update site (rather than distributing a pre-packaged installation), use web or FTP access with user access controls. Requiring individual user authorization limits Design Studio feature access to a limited set of users. See authentication configuration instructions for the web server or FTP server in use.
Secure Packaged Installation
Use a secure web server or FTP server when publishing a pre-packaged Design Studio installation. To help prevent development of viral cartridges or tampering of cartridges, restrict the Design Studio application to a limited set of users.
Following extraction, users should ensure that the Design Studio files and folders have full privileges for the user and no privileges for groups or other users.
See operating system-specific documentation for configuring file and directory access privileges.
SSL Key Store
SSL connections are required to secure connectivity to the product servers when executing cartridge management functions. The SSL keys must be made available to each Design Studio installation using a key store. To ensure a secure installation, configure the keys and ensure that the key store is configured with strict file access privileges, readable to Design Studio users only.