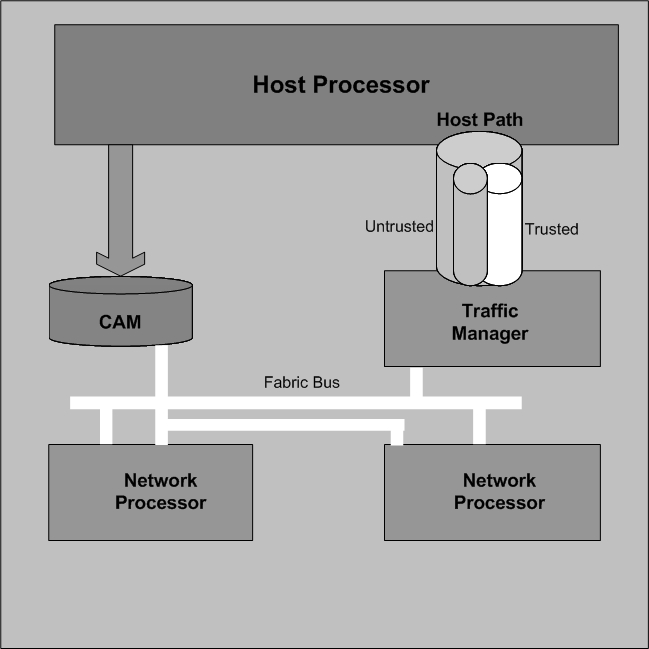
About the Process
DoS attacks are handled in the OECB’s host path. The OECB uses NAT table entries to filter out undesirable IP addresses; creating a deny list. After a packet from an endpoint is accepted through NAT filtering, policing is implemented in the Traffic Manager subsystem based on the sender’s IP address. NAT table entries distinguish signaling packets coming in from different sources for policing purposes.
The Traffic Manager has two pipes, trusted and untrusted, for the signaling path. Each signaling packet destined for the host CPU traverses one of these two pipes.