ALG for HTTP and HTTPS
The Oracle® Enterprise Session Border Controller (Enterprise SBC) functions as an HTTP Application Layer Gateway (ALG) for HTTP/HTTPS traffic that originates on Avaya endpoints and terminates on the Avaya Session Manager (ASM) as follows:
- The Enterprise SBC receives HTTP requests from Avaya endpoints on a user-configurable IP address and port.
- The Enterprise SBC forwards the requests to a user-configurable destination, which is the IP address and port of the ASM.
- The ASM sends the response to the HTTP request to the Enterprise SBC.
- The Enterprise SBC parses the HTTP
response and searches for:
- getHomeServerResponse-If present, the Enterprise SBC replaces any text between the <PpmServer> or <SipServer> tags with the IP address of the public interface on which the HTTP-ALG is configured.
- getHomeCapabilitiesResponse- If present, the Enterprise SBC replaces any text contained between the <ServiceURI> tags with the IP address of the public interface on which the HTTP-ALG is configured.
If the Enterprise SBC is behind a NAT device, the nat-address parameters allow it to replace the above parameters with that address instead of its public interface, allowing persistent connectivity. The Enterprise SBC checks the nat-address parameter in the public part of the HTTP-ALG object (or the session-manager-mapping). If you have configured this parameter with an IP Address, then the Enterprise SBC use it as a replacement. If not, it replaces it with the external IP address of the Enterprise SBC.
- If the external IP of NAT is configured in the HTTP-ALG object, then the Enterprise SBC behaves as follows:
- If session-manager-mapping is not configured, the Enterprise SBC adds the external IP address of NAT/Firewall device in the Public part of HTTP-ALG object.
- If a session-manager-mapping is configured, the Enterprise SBC adds the external IP address of NAT/Firewall device in the applicable session-manager-mapping.
- If the external IP of NAT is configured, the Enterprise SBC replaces the fields <ppmServer> and <sipServer> of getHomeServerResponse and getHomeCapabilitesResponse messages.
- If several ppmServer/sipServer fields are present in getHomeServerResponse and getHomeCapabilitesResponse , the Enterprise SBC searches for a specific ip-address and then replace it with the new configured value if a match is found.
- If the external IP of the NAT is not configured in HTTP-ALG object and there is no session-manager-mapping, the Enterprise SBC adds the external IP address of NAT/Firewall device in the Public part of HTTP-ALG object.
- After the Enterprise SBC processes the response, it forwards the response to the originating Avaya endpoint.
The following illustration shows how the Enterprise SBC sends and receives HTTP requests and responses to the Avaya Session Manager.
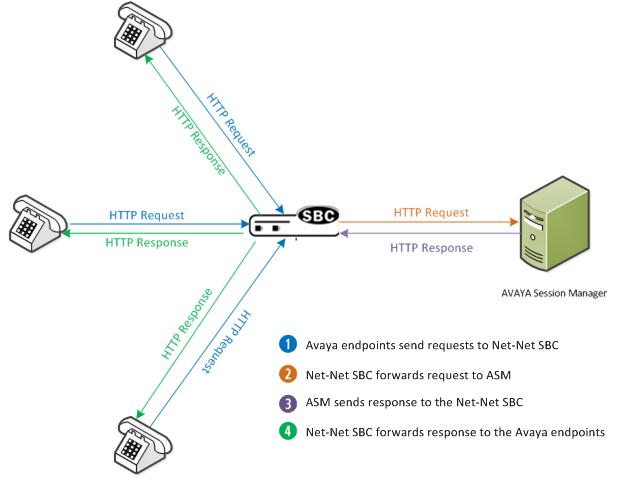
The following is the call flow that occurs as the HTTP/HTTPS requests and responses are passed between the Avaya endpoints, the Enterprise SBC, and the ASM.
