2 LSMS Security Overview
This chapter describes basic security considerations and provides an overview of LSMS security.
2.1 Basic Security Considerations
The following principles are fundamental to using any application securely:
- Keep software up to date
This includes the latest product release and any patches that apply to it.
- Limit privileges as much as possible
Users should be given only the access necessary to perform their work. User privileges should be reviewed periodically to determine relevance to current work requirements.
- Monitor system activity
Establish who should access which system components, and how often, and monitor those components.
- Install software securely
For example, use firewalls, secure protocols using TLS (SSL), and secure passwords. See Performing a Secure LSMS Installation for more information.
- Learn about and use the LSMS security features
See Implementing LSMS Security for more information.
- Use secure development practices
For example, take advantage of existing database security functionality instead of creating your own application security.
- Keep up to date on security information
Oracle regularly issues security-related patch updates and security alerts. You must install all security patches as soon as possible. See the "Critical Patch Updates and Security Alerts" Web site:http://www.oracle.com/technetwork/topics/security/alerts-086861.html
When planning for security, consider the following questions:
- Which resources need to be protected?
- You need to protect customer data, such as telephone number (TN) information and associated data.
- You need to protect internal data, such as proprietary source code.
- You need to protect system components from being disabled by external attacks or intentional system overloads.
- Who are you protecting data from?
For example, you need to protect your subscribers' data from other subscribers, but someone in your organization might need to access that data to manage it. You can analyze your work flows to determine who needs access to the data; for example, it is possible that a system administrator can manage your system components without needing to access the system data.
- What happens if protections on strategic resources fail?
In some cases, a fault in your security scheme is nothing more than an inconvenience. In other cases, a fault might cause great damage to you or your customers. Understanding the security ramifications of each resource will help you protect it properly.
2.2 Understanding the LSMS Environment
Local Number Portability (LNP) allows a subscriber to change location, service provider, or service while keeping the same directory number. Number portability ensures that subscribers receive the same freedom of choice for local service as they have with long-distance service providers.
These changes in telephone service enable LNP:
- When a subscriber is granted LNP service, the subscriber’s telephone number is "ported" into various LNP databases that contain routing information. The official repository for LNP database information is contained in government-controlled Number Portability Administration Centers (NPACs). Currently, eight regional NPACs serve the United States and Canada.
- Central office and tandem switches no longer will use only a telephone number’s NPA-NXX code (area code and local exchange code) to determine where a call should be delivered. Routing information is stored in LNP databases, which must be queried when any call is made to an NPA-NXX that contains one or more ported numbers.
LSMS Security Overview details how an LSMS serves as an interface between NPAC Service Management Systems (SMSs) and network elements (central office or tandem switches). The LSMS maintains a service provider’s LNP data so that it is not necessary for each network element (NE) to have a direct connection with each NPAC. This figure shows the maximum number of NPACs and network elements supported by Oracle's LSMS.
Figure 2-1 LNP Configuration
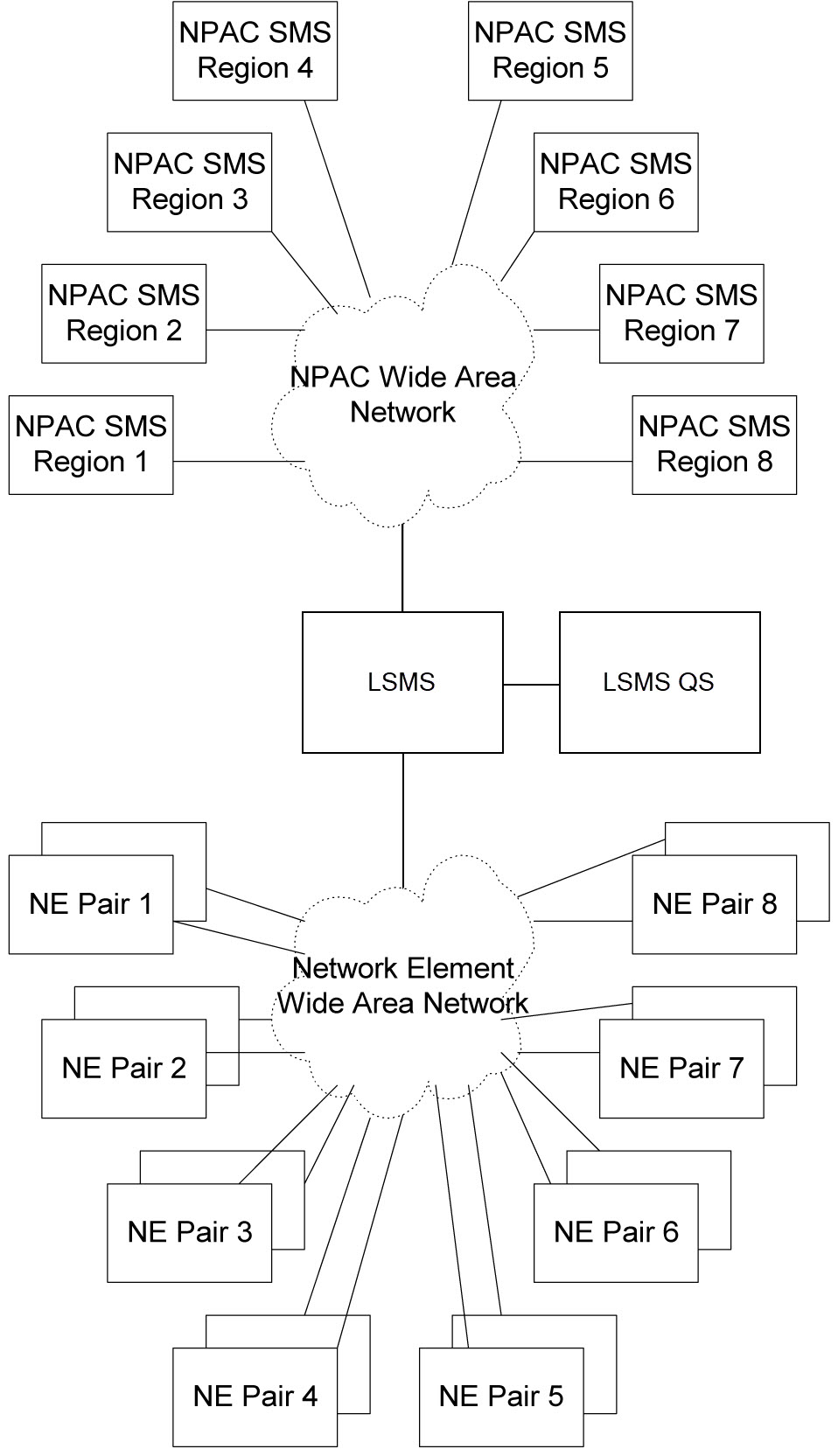
The LSMS application receives LNP data from the NPAC, stores the data, and transfers the data to the correct NE. LSMS supports the following NPACs:
- Midwest
- MidAtlantic
- Northeast
- Southeast
- Southwest
- Western
- WestCoast
- Canada
When connected to multiple NPACs, LSMS keeps the data for each NPAC separate. Each NPAC can access data only in its corresponding regional database.
The LSMS is composed of hardware and software components that interact to create a secure and reliable LNP system.
2.3 Overview of LSMS Security
The LSMS is a secure and reliable Local Number Portability (LNP) system that enables customers to administer their LNP data in a central place.
Operating System Security
Oracle Communications Tekelec Platform (TPD) handles all operating system security for the LSMS application. Make sure you always have the latest TPD software/patches installed on your machines.
TMN Toolkit licenses and Marben OSI stack licenses must be installed for both LSMS servers. License files are obtained from NE Technologies, Inc. For information about how to obtain and install the TMN Toolkit licenses, refer to this release's Incremental Upgrade/Installation Guide.
GUI Security
By default, both Hypertext Transfer Protocol (HTTP) and Secure Hypertext Transfer Protocol (HTTPS) are enabled for the GUI.
HTTPS supports encryption of data exchanged between the web server and the browser, thus facilitating data privacy. HTTP is not encrypted/secure and can be disabled. For more information, see Using Login Sessions.
Database Security
The following LSMS-specific security considerations apply to the MySQL database:
- Secure Database Access Credentials
Only authorized personnel are allowed to access the database and a user ID and password are required.
Provide minimum privileges to the user so that unauthorized modifications can be avoided. For more information, see Managing User Accounts.
- Use SSH/SSL Connections
SSH/SSL is a robust, commercial-grade, and full-featured toolkit that implements the security and network encryption. SSH/SSL provides secure data transmission through encryption keys.
Encryption is required for the connection between the NPAC and the LSMS. The LSMS has a key for each NPAC that it services. For more information about using key lists, refer to Configuration Guide.
- Modify the MySQL Port for Query Servers
Since the default MySQL port 3306 is a well-known port, to prevent eavesdropping use the LSMS GUI to change the MySQL port for query servers. For more information about modifying the MySQL port for query servers, see Alarms and Maintenance Guide.
SPID Security for Locally Provisioned Data
Without the optional Service Provider Identifier (SPID) Security feature, any user is able to log in using any SPID that is defined on the LSMS. The user is able to view any data for any SPID, and depending on the user privileges that were assigned to the user, the user might even be able to change data associated with any SPID.
The SPID Security feature enables the LSMS administrator to control the users that can log on with a specified SPID. In addition, the LSMS administrator can assign special access to a user that provides access to all SPIDs; such a user is called a golden user.
The SPID Security feature is especially useful for LSMS customers that act as service bureaus, offering LSMS services to other service providers. The service bureau may administer locally provisioned data for a client and may choose to allow the client to administer or view its own data without allowing that client to view or change data belonging to other clients.
For more information, refer to Managing SPID Security.
Secure Network Management
LSMS can interact with Oracle Communications EAGLE Element Management System (OCEEMS) or other network management systems using secure SNMP v3 authentication and encryption. For more information, see Alarms and Maintenance Guide.
LSMS can interact with LSMS Query Server using TLS 1.2 encryption. For more information, see LSMS Query Server on Linux Installation and Upgrade Guide.