Additional Enhancements
- Auto-Path Groups for WAN Links
In previous releases the user would have to create a manual path and then edit the advanced attributes for the path for private WAN links. Because there was no auto-path for private (intranet) WAN links the user was forced to define the paths and attributes for the path. This new feature allows a user to define an “Auto-Path-group” at the global level and assign attributes to the group.
An “Auto-Path-group” defines a set of WAN links in the Oracle SD-WAN Edge that are reachable to each other. Figure 8 displays the options for the group.
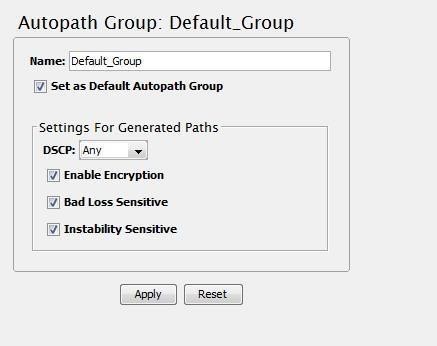
Figure 8
The options other than the group name are standard Oracle options:
- DSCP setting for the path
- Encryption enabled or disabled
- Bad loss sensitivity
- Instability Sensitive
Once the group is defined it can be applied to as many WAN Links as needed reducing the configuration time.
Figure 9 displays where to apply this option.
The group is applied at the WAN link – Service properties – Conduit Level, under the Autopath group pull down menu.
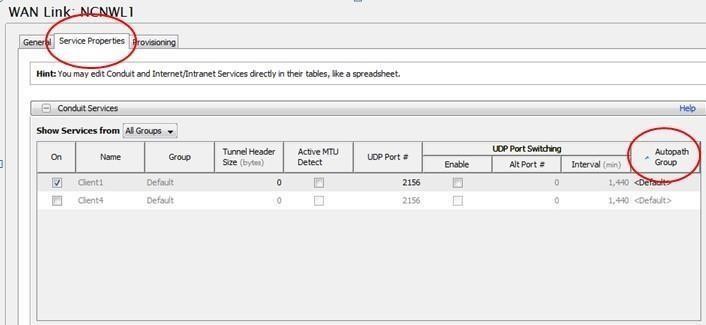
Figure 9
- SNMP
Within the Oracle SNMP MIB there were enhancements and bug fixes added to the Oracle MIB. These changes include the following:
- Add a Last updated date for the MIB
- OracleNumEvents is now a gauge with events being clean up after 30 days
- When in standby mode for HA counters are now accurate
- All rule statistics types have changed from counters (64) to gauge
- Dynamic Conduit statistics table is a separate table as there is only data when the conduit is in use
- The appliance serial number is viewable from SNMP
- The MIB now allows customers to define a “Contact”, “Location”, and or Description for an appliance. This is configured under Integrate >>Configure Events and Alerts in the web console of the appliance
- tnStatsRuleTable now reports data correctly and will match the web console displayed data for rule statistics
- tnStatsConduitEntry –now records BOWT (Best One Way Time), Jitter, Packets
Lost uni- directionally
- The ability to query Oracle version information was added to the MIB, including APNware version, OS version etc.
- tnstatsConduitClassType values now match the web console classes as expected
- Cisco NetFlow MIB is no longer supported
- ARP Timeout Setting
In the past this option was set-able through a debug level. This has now been moved to a user configurable parameter. Any previously configured ARP timeout value set using the debug level will be lost and must now be configured using the Gateway ARP Timer setting in the Configuration Editor. It defines the amount of time between ARPs for a Oracle WAN link gateway.
This option is changed when devices do not handle the 1 second ARP value used by default in the Oracle appliance. The user can now define the number of seconds for ARP on an appliance at the global level. Figure 8 displays where to define this option.
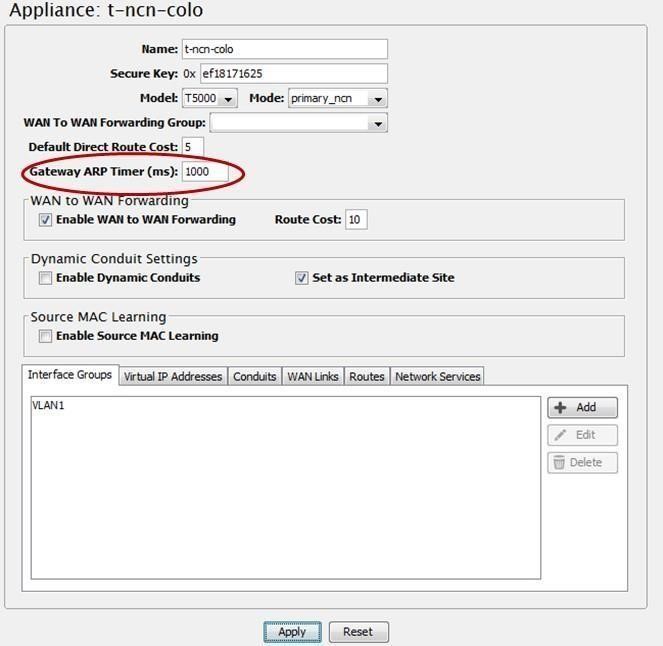
Figure 10
- WAN Link Disable Paths Option
In previous releases, a user wishing to prevent traffic from using a WAN link would have to individually disable each path that used the WAN link. Based on user requests, this has been enhanced to allow a user to select a WAN link to disable, which will automatically disable all paths on that WAN link.
- Ping Enhancements
Ping has now been enhanced to include the following new options:
- Ping count
- Packet size
In the past the system would only ping 5 times and the user could not define the size of a ping frame. This has been enhanced for troubleshooting purposes.
- Security Enhancements
Certain security enhancements are now included in APNware 3.0. These are listed below.
- Within the web console or the CLI the admin level user can now change the root level password if they know the current root password.
- Users accessing the appliance from SSH now can be authenticated by RADIUS or TACACS (Release 3.0P1)
- Additional RADIUS and TACACS server are now configurable, if the first server fails then the next server in the list will be used to authenticate the user. (release 3.0P1)