Password Policy
The Admin Security feature set supports the creation of password policies that enhance the authentication process by imposing requirements for:
- password length
- password strength
- password history and re-use
- password expiration and
grace period
The Admin Security feature set restricts access to the ACP ports and mandates the following password length/strength requirements.
- user password must contain at least 9 characters (Admin Security only)
- admin password must contain at least 15 characters
- passwords must contain at least 2 lower case alphabetic characters
- passwords must contain at least 2 upper case alphabetic characters
- passwords must contain at least 2 numeric characters
- passwords must contain at least 2 special characters (such as !, ", #, $, %, &, ' , (, ), *, +, , , -, ., /, :, ;, <, =, >, ?, @, [, \, ], ^, _, `, {, |, }, ~)
- passwords must differ from the prior password by at least 4 characters
- passwords cannot contain, repeat, or reverse the entire user name
- passwords cannot contain three consecutive identical characters
The Admin Security ACP add-on feature imposes the same password length/strength requirements as above except for the minimum length requirement, and also provides access to the ACP ports.
- passwords cannot contain two or more sequential characters from the user ID. This rule is not case sensitive. For example, if the username is "admin," the password cannot contain "ad" nor "AD."
- passwords cannot contain a sequence of three or more characters from any password contained in the password history cache
- passwords cannot contain a sequence of two or more characters more than once
- passwords cannot contain either sequential numbers or characters
In the absence of the Admin Security ACP feature, you may safely ignore the password-policy-strength config property and retain the default value (disabled). For more information, see Configuring the Admin Security with ACP Password Rules.
Some specific password policy properties, specifically those regarding password lifetime and expiration procedures, are also applicable to SSH public keys used to authenticate client users.
Configuring Password Policy Properties
The single instance password-policy configuration element defines the password policy.
Configuring the Administrative Security with ACP Password Rules
To enforce the stronger password rules and restrictions that the Administrative Security ACP license it provides, you must enable the password-policy-strength parameter.
- Confirm that the Administrative Security ACP license is installed on the system.
- You must have Superuser permissions.
Note:
The password-policy configuration element displays the min-secure-pwd-len command. You do not need to configure the min-secure-pwd-len command because the Administrative Security ACP license overrides this command with a stronger rule.You can configure any of the other password policy settings without a system override, according to the ranges specified in this procedure. For more information about the ranges, see "Administrative Security ACP License Configuration."
Changing a Password
As shown in the following figures, the password-policy configuration element provides prior notice of impending password expiration via the login banner display, and with additional notices when ending a login session.
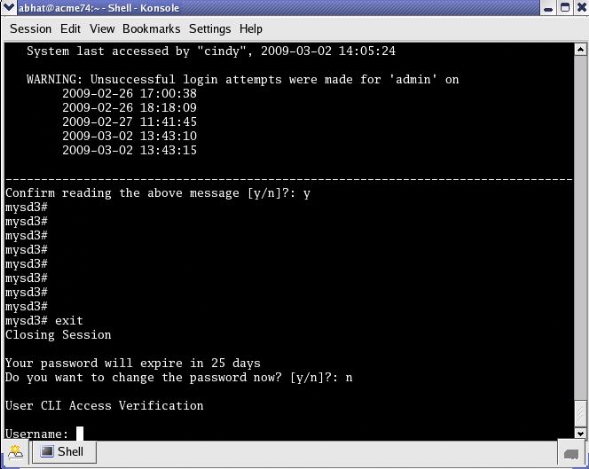
Password Expiration Notices at Login and Logout
After password expiration, additional notices are displayed with each grace login. If all notices are ignored, the password-policy enforces a password change when grace logins have been exhausted, or when the grace period has elapsed.
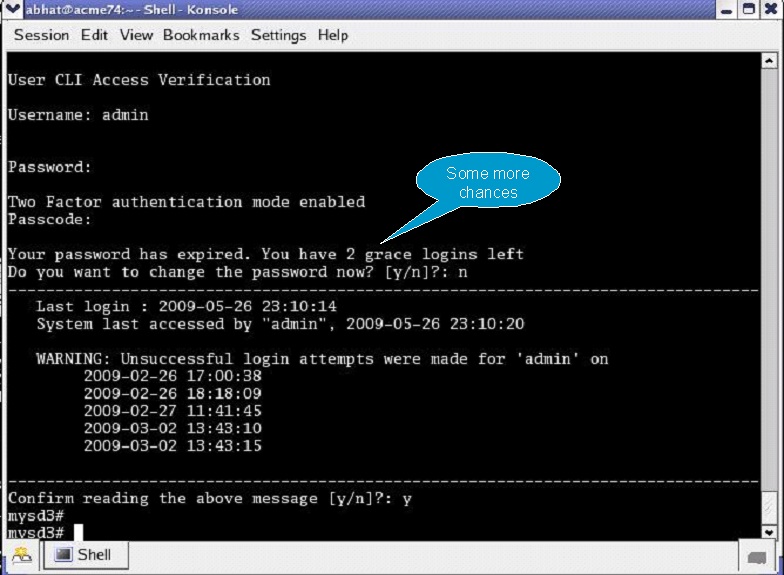
Changing Password Process
To change your password in response to (1) an impending expiration notice displayed within the login banner or at system logout, (2) a grace login notice, or (3) an expiration notice:
Changing a Passcode
A passcode is a secondary credential passed to the authentication process when |two-factor authentication is enabled. Passcodes are subject to length/strength requirements imposed by the password policy, but are not bound by other policy mandates regarding history, re-use, and expiration.
The admin account can change passcodes using the ACLI as described below.
Change the user passcode from the # (admin) prompt.