Overview
The Oracle Session Border Controller (SBC) family of products is designed to increase security, when deploying Voice over IP (VoIP) or Unified Communications (UC) solutions. Oracle's SBC family helps to protect IT assets, safeguard confidential information, and mitigate risks, while ensuring the high levels of service that users expect from the corporate phone system and the public telephone network.
- Overload protection to prevent DoS attacks and registration floods
- Access control to inhibit toll fraud and service theft
- Topology hiding to counter topology discovery through reconnaissance scans
- Encryption and authentication to ensure privacy and prevent loss of confidential information
- Protocol validation to combat fuzzing and other types of malicious attacks
Net-SAFE Security Framework
The Oracle Net-SAFE™ security framework addresses the unique security challenges of delivering SIP-based interactive IP communications over the Internet. The Net-SAFE framework includes advanced security features, a highly-scalable architecture, and comprehensive monitoring and reporting capabilities. The framework reduces risk in UC services and applications by ensuring confidentiality, integrity, and availability.
- Protect the SBC—The first line of defense at the border is the SBC, which must be secure and resistant to attacks and overload.
- Protect the infrastructure—The infrastructure includes the customer’s network of multimedia equipment (soft switches, application servers, SIP proxies, H.323 gatekeepers, gateways, and others).
- Protect the service—Preventing attacks is not enough. UC services that generate revenue need to remain in service.
Example 1-1 Net-SAFE Requirements
The Net-SAFE framework identifies the requirements that an SBC must satisfy to meet the goals of the framework and provide confidentiality, integrity, and availability.
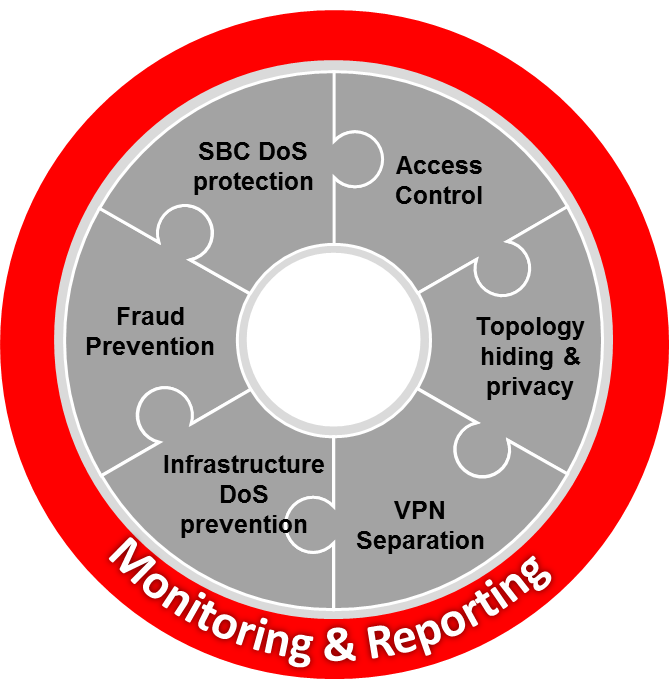
The Net-SAFE Framework spans seven general functions.
- Denial of Service (DoS)
protection
- Dynamic self-protection against malicious and non-malicious DoS attacks and overloads at layers 3 and 4 (TCP, SYN, ICMP, fragments, and others) and layer 5 (SIP signaling floods, malformed messages, and others)
- Traffic management queues for control and throttling of signaling and media
- Access control
- Session-aware access control for signaling and media using static and dynamic permit/deny ACLs at layers 3 and 5
- ACL and DOS protection for the management interface
- Topology hiding and
privacy
- Complete infrastructure topology hiding at all protocol layers for confidentiality and attack prevention as well as modification, removal, or insertion of call signaling application headers and fields
- Confidentiality and integrity through use of industry-standard encryption methods such as TLS, SRTP, and IPSec
- VPN separation
- Support for Virtual Private Networks (VPNs) with full inter-VPN topology hiding and separation
- Ability to create separate signaling-only and media-only VPNs
- Optional intra-VPN media hair-pinning to monitor calls within a VPN
- Service infrastructure DoS
prevention
- Per-device signaling and media overload control, with deep packet inspection and call rate control to prevent DoS attacks from reaching service infrastructure
- Fraud prevention
- Session-based authentication, authorization, and contract enforcement for signaling and media
- Monitoring and reporting
- Audit trails, event logs, access violation logs and traps, and management access command recording
- Call Detail Records (CDRs) with media performance monitoring
- Raw packet capture ability
- Lawful Intercept capability (For Service Provider products, only. Enterprise products do not support Lawful Intercept.)