Packet Inspector
The Packet Inspector page allows you to examine and download arbitrary network traffic captured on the probes. Downloads are done in the industry-standard PCAP file format, that contains the complete messages as monitored on the network.
Most of the available protocol analyzers can interpret the PCAP file format, including open- source tools. Any stored message contains the full raw frame including IP and TCP/UDP headers, as well as the timestamp when the message was received.
The filter for Packet Inspector determines the traffic that is captured and available for searching. You set this filter in the Signaling Protocols page in Platform Setup Application on the Probe. For increased system performance, it is important that this filter restrict the traffic that is captured and is comparable to the default filter. The Probe captures the packets from the moment the it is set up. See Session Monitor Installation Guide for more information about signaling protocol filters.
If you use Packet Inspector for recording media, you need to include media packets in the filter. Media packets are initially stored on the Probe machine until the Probe sends the packets to the Mediation Engine when a user downloads the media to a PCAP file. You need to ensure that there is sufficient disk space on the Probe machine for storing media.
Packet Inspector Page
The Packet Inspector page consists of a form where you specify the search parameters and a panel listing the preview of the results of a search.
Query Panel
The Query panel displays a chart that shows the amount of traffic received every two seconds. You can use the chart for selecting a time range. Operations Monitor searches the packets captured during the selected interval of time.
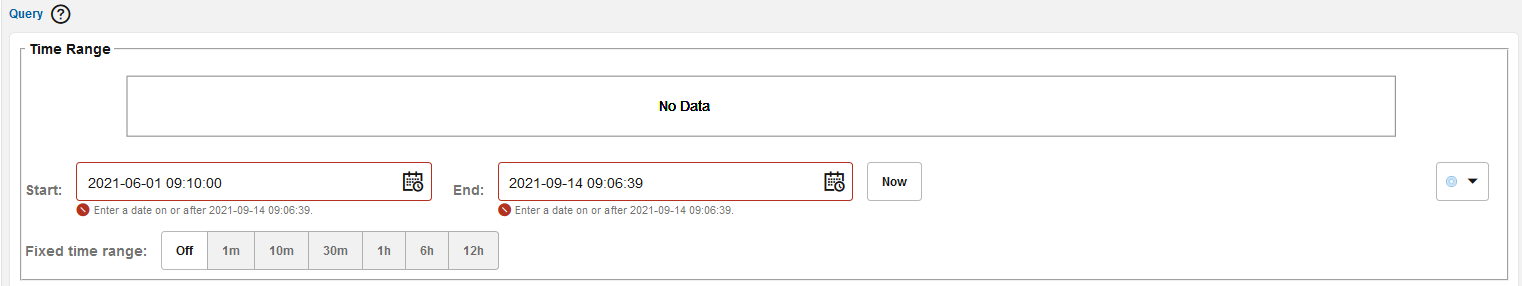
Time Range Selection
To select a time range, you can select, move, or resize a time range selection in the chart or use the controls to select a specific start and end date or a fixed time range (see the following figure). If you select a start and end date, the selection on the chart changes accordingly. If you select a fixed time range, the start and end dates and the selection on the chart changes accordingly.
Figure 3-38 Packets - Time Range Selection
Filter
To filter the result set further, you can enter filters in the Filter text field. On the right of the Filter text field (see the following figure) are some filter examples. See "Query Examples" for additional usage examples.
Figure 3-39 Filter

Search Results Preview Panel
Figure 3-40 Search Results Preview panel
Note:
When the traffic sniffing is used with multiple ports and multiple worker threads, the packet sequence in the PCAP file resulting from the Packet Inspector search may not be in the timestamp order. However, if the packets need to be in order based on their timestamp, Wireshark can be used.Query Examples
Query examples are Wireshark syntax. The following are examples of queries that can be used in the Filter text field:
-
Filter for any IP
traffic to or from 192.168.42.70:
ip.addr == 192.168.42.70 - Filter for MEGACO messages to
192.168.1.1 or from 192.168.1.2 with transaction ids in range 2000..2500:
(ip.src == 192.168.1.2 or ip.dst == 192.168.1.1) and megaco.transid > "2000" and megaco.transid < "2500" - Filter for ISUP to the device
with point-code 1111 calling number 1234567:
mtp3.dpc == 1111 and isup and e164.called_party_number.digits == "1234567"
Not all filter expressions work with fragmented packets. To get all packets, use an expression like:
sip.Call-ID == "910820420140505605616932@172.19.235.6" || ip.flags.mf==1Using a query to filter for media packets can decrease system performance; therefore, it is not recommended.
Note:
The total size of the storage space that Packet Inspector can use is limited. The default value of this limit is 81% of the disk space for each configured probe. Furthermore, there is a limit of three concurrent queries for each product instance running.To improve the speed of Packet Inspector queries, use the following syntax to search for IP or ports:
tcpdump: [bpf filter]You can use this syntax to search only for IP or ports and without any message content. For examples of BPF filters, see the topic on Filter Syntax in the Oracle Communications Session monitor Installation Guide.
Note:
Searches combining tcpdump/BPF and Wireshark filter language are not supported.