OAuth Operation
The Oracle Communications Unified Session Manager assumes a client requesting OAuth authentication has previously acquired a token from its authorization server. This and token refresh procedures are performed outside of the scope of Oracle Communications Unified Session Manager operation. Within the context of OAuth processes, the Oracle Communications Unified Session Manager performs the functions of a resource server only.
Upon receiving applicable requests from a UA, the Oracle Communications Unified Session Manager attempts to authenticate using OAuth or Digest. If the request includes a bearer string and a token, the Oracle Communications Unified Session Manager initiates OAuth authentication by sending an HTTP query (GET request) to a Secure Token Service Server (STS), as shown below.
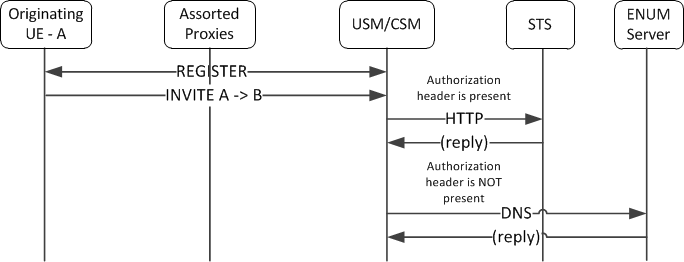
If the STS returns a 200 OK, the Oracle Communications Unified Session Manager proceeds with authentication. If the STS does not reply or is not reachable, the Oracle Communications Unified Session Manager replies to the UA with a 500 Internal server error. If the STS replies with any message other than a 200OK, the Oracle Communications Unified Session Manager replies to the UA with a 403 Forbidden.
The Oracle Communications Unified Session Manager uses the User ID within the STS 200OK to authenticate and authorize service, as follows:
- For register requests, the system compares this to the user ID field in the TO header of the SIP request.
- For other requests, the system compares it to the user ID field in the FROM header.
If the user ID matches, the Oracle Communications Unified Session Manager proceeds with authentication. If this procedure concludes with matches, the Oracle Communications Unified Session Manager provides service to the UA. If not, it replies to the UA with a 403 forbidden.
Note the following operational caveats:
- If the bearer token is present, but the Oracle Communications Unified Session Manager is not configured for OAuth, the Oracle Communications Unified Session Manager responds with a 500 internal service error message. Such misconfiguration includes the OAuth SPL plugin, described below, being absent or disabled.
- If the bearer token is not in the request, the Oracle Communications Unified Session Manager proceeds with SIP digest authentication.
- If the request arrives over a secure channel, the Oracle Communications Unified Session Manager follows the procedure defined by the applicable sip-authentication-profile, which may not require authentication.