Data Reaction on Export
Personal identifiable information (PII) requires special handling when exported out of the application and written to files. Information that is encrypted at the database level remain encrypted and therefore protected when exported. With respect to non-encrypted information, the need to obfuscate it for added protection depends on how the exported data is intended to be used. If the exported information is part of an integration flow with an external system then the data should remain unchanged. However, when exporting data from a production environment for testing purposes sensitive information should be anonymized before they can be imported to a lower environment.
The following are key aspects of this functionality:
• Redaction rules define how specific fields should be redacted when exported.
• When redaction rules exist, data redaction is performed by default by specific export tools. In absence of redaction rules, data is exported in its original form.
• Redaction rules are customer specific and may only be relevant to environments that contain sensitive data. As such, they are not released with the base product. Review your data redaction requirements and configure appropriate rules in relevant environments.
• Certain users may be allowed to export data in a non-redacted form based on application security.
The following sections provide additional information about this topic.
Redaction Rules Are Customer Specific
Redaction rules identify which fields should be redacted and how they should be anonymized. The list of fields to redact and the function to use to manipulate their values are customer specific and therefore are not released with the base product. A sample set of rules are provided as accelerator data for reference only.
It is important that you review your data redaction requirements and configure rules that reflect your business needs.
Redaction By Default
Processes that support data redaction on export do so by default when redaction rules exists. When rules are not defined, data is exported as is. Note that for this reason it is unnecessary to define such rules in lower environments that do not contain sensitive information.
Specific Export Tools Only
Data redaction is supported by the following export tools only:
• Content Migration Assistant (CMA). Depending on application security, a user may indicate on a specific data set export request that data should be exported in its original form.
• General Data Export (GDE) batch processes. A batch parameter may be used to explicitly request that data is exported in its original form. This option is also protected by application security and enforced at batch submission time.
Note:
This type of process establishes a single export stream that may be sent to multiple targets. Review these integrations to ensure they do not have conflicting data redaction requirements and set the batch parameter accordingly.
This type of process establishes a single export stream that may be sent to multiple targets. Review these integrations to ensure they do not have conflicting data redaction requirements and set the batch parameter accordingly.
Different Types of Redaction Rules
Sensitive information may reside in various types of storage fields which impact the way they are identified for redaction. You may define rules that target fields on specific tables or provide a more global rules that applies to all references of a specific field.
The application supports the following types of reduction rules:
• Physical Field. This type of rule applies to a value residing in a field on a specific table. An optional filter expression may be provided when only records of a certain type needs to be redacted.
• XML Storage. This type of rule applies a value associated with the specified field name that resides within an XML storage field on a specific table. This option also supports a filter expression.
• Reference Field. This type of rule applies to a value residing anywhere and associated with the specified field name. It does not include fields referenced in XML storage fields.
Redaction Function
A redaction function defines the format by which a value is anonymized. The type of function used depends on the field’s data type. For example, to anonymize a numeric field the redaction function should only use numeric values etc.
Refer to the Redaction Function extendable lookup for a list of available functions. The base product provides a sample of common functions but the list may be extended by your organization as needed.
Fields May Contain Sensitive Information
The field definition record includes an indication as to whether the field may contained sensitive information or not. Note that the indication does not imply that the field is actually used to capture such data but rather that it can potentially be used this way. Use this indication to review fields that may need to be associated with a redaction rule.
Exporting Non-Redacted Data Requires Security Rights
By default, the aforementioned export tools redact data by default based on existing redaction rules. There are situations where certain users may be allowed to export data in its original form, i.e. request to not apply the redaction rules.
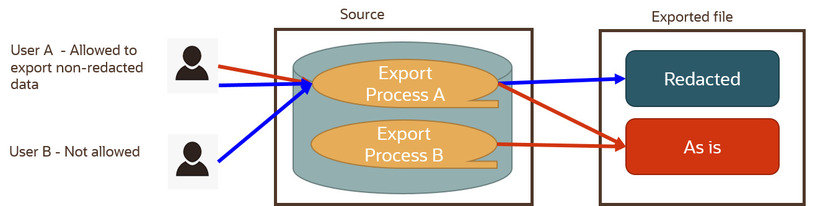
The following points briefly describe the above illustration:
• Some processes always export data as is, i.e. the target consumer needs the raw data. This is irrespective of the user requesting the export.
• Some processes perform data redaction by default and may offer an option for exporting data as is. The option to export data in its original form is secured by application security.
• In this example, process A supports data redaction by default with an option to export non-redacted data. User A has the right to export the data redacted (default) or explicitly request to export it in its original form. User B does not have the right to do so hence their export content is redacted by default.
The option to export data in its original form is associated with the Do Not Apply Redaction Rules access mode associated with the following relevant application services:
• For CMA, the additional access mode is associated with the migration data set export's application service. When granted, the user may select the special non-redacted export option when they create the export data set request.
• For GDE batch processes, the access mode is associated with their application service and is tied to the Do Not Apply Redaction Rules batch parameter they support. Only users with the proper application security can submit these batches using the special batch parameter option
Parent topic