Mobile User Validation
Mobile user validation is done in the Network Management System Configuration Assistant and is a separate validation scheme than the Network Management System Web Workspace users.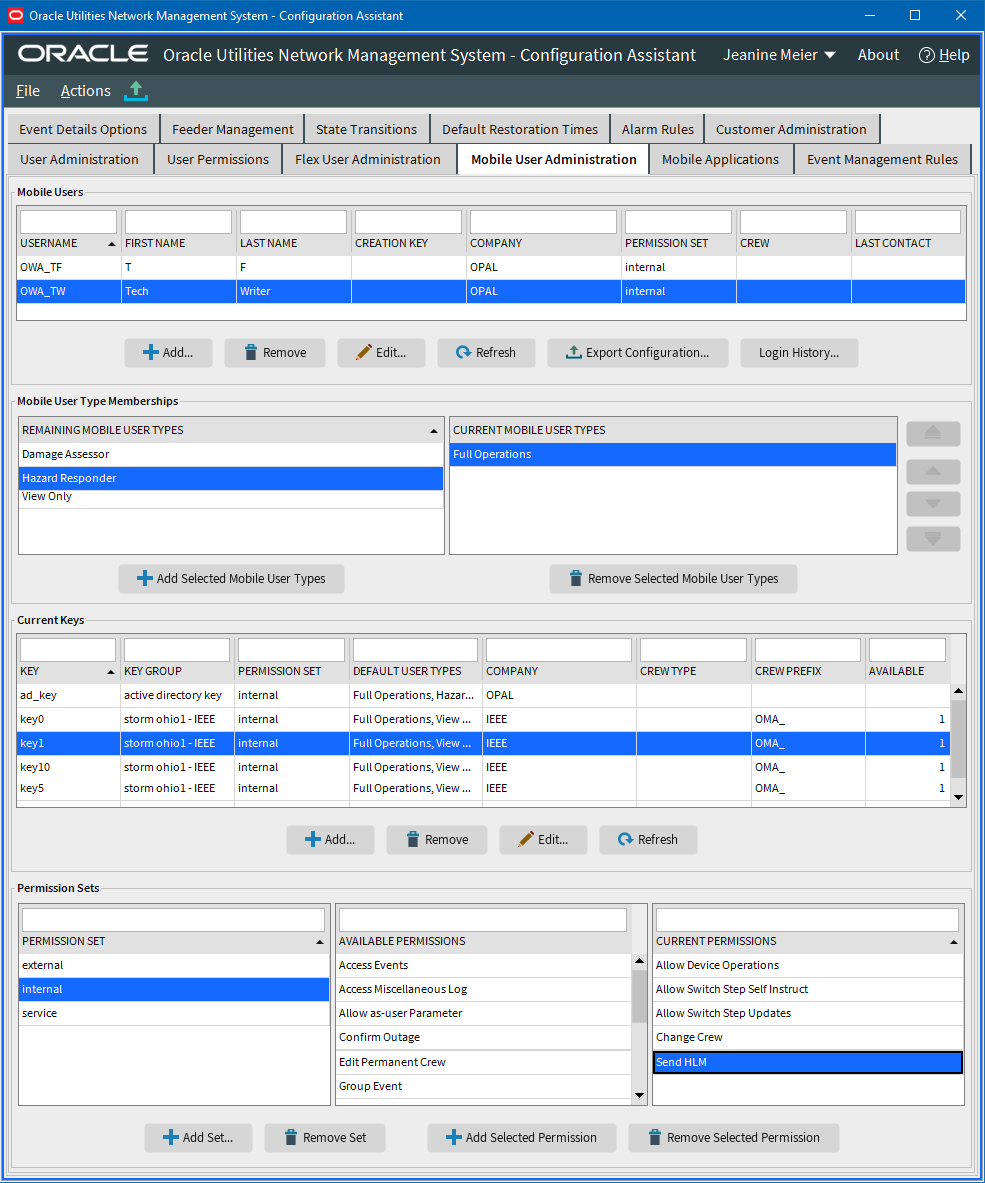

Permissions and Permission Sets
Permissions are used to allow users to have access to functionality and information. The permissions available include:
• Change Crew: This access allows a user to change the crew. If it is not assigned to a user then the user will be locked to their existing crew.
• Extended Switch Step Updates: Client side rule to allow the user to edit more switch step fields than just the completion time and comments.
• Allow Switch Step Updates: Allow the user to update switch sheet transitions and update fields.
• Allow Device Operations: Ability to mark non-SCADA devices open or open or closed in NMS
• Send HLM: Allow the user to send high-level messages to the NMS.
Permission sets are groups of permissions. Users and Keys have permission sets associated to them.
Predefined Users
Mobile users can be defined in the Network Management Systems using the Configuration Assistant Mobile User Administration tab. An administrator can create the predefined username using the Mobile Users section by hitting the Add button and filling out the Add/Edit Mobile User Information panel and saving the changes.
Operations Mobile Application users can enter the username/password as authorized in this section to gain access to the application functionality.
Creating Users Using a Key
Mobile users may be created on the mobile client when the user is given a key authorizing the creation of a mobile user. In the mobile app login page, the user can check the new user box and enter in a new username, password, and the provided new user key and create a new mobile user.
The keys required to create a mobile user from the mobile application are maintained in the mobile_new_user_keys database table in the Network Management System. This table can be managed using the Network Management System Configuration Assistant Mobile User Administration tab in the Current Keys section. Simply add a new key with an availability count greater than zero, the key can be used by a mobile app user to create a new username/password into the system. The number of times this key can be user is based on the available number, each time the key is used, the available number is decremented.
To create a key for the mobile application, click the Add button at the bottom of the Network Management System Configuration Assistant Mobile User Administration Current Keys section and filling out the Add/Edit Mobile Keys Information panel and saving the changes.
If a key contains a crew type and crew prefix, a crew will be created automatically for the users created with the key.
For more details on the Configuration Assistant Mobile User Administration, refer to the Oracle Utilities Network Management System User’s Guide and the Oracle Utilities Network Management System Configuration Guide.
Using LDAP/AD User Validation
LDAP/AD users can be configured to work with OMA. However, if you plan to support both OMA authenticated users, Predefined or Keys (as described in the previous two sections), then you need to force OMA authenticated users to have a user name prefix to eliminate potential conflicts with LDAP/AD user names. To specify a user name prefix requirement for OMA authenticated users, specify the Crew Prefix in the Configuration Assistant’s Mobile Users tab’s Current Keys section.
LDAP validation can occur in one of two places: the nms-ws WebLogic authentication scheme or the cesejb WebLogic authentication scheme. If the RESTful service calls contain an http header nmsWsValidate: true, then the nms-ws WebLogic authentication scheme will be used first prior to attempting to use the cesejb WebLogic authentication scheme. Otherwise, without the nmsWsValidation header, only the cesejb WebLogic authentication scheme will be used.
To configure LDAP/AD user validation for OMA, there are two lines that need to be enabled in the CentricityServer.properties file. Uncomment the last two lines, as shown below:
# Operations Mobile Application (OMA) user authentication configuration
#
# If a user belongs to an ldap group starting with the defined mobile_ldap_user_group_prefix, they are allowed access to OMA services
#
# If the value of mobile_ldap_user_group_prefix = DISABLED, no user validation to the ldap server will be performed.
#
# If the mobile_ldap_user_group_prefix is an exact match, and the user is new to OMA, the mobile_ldap_user_default_new_user_key is assigned to the user.
#
# If the group_prefix is followed by -<new_user_key>, (example, omauser-ad_key), then the <new_user_key> will be used as the new_user_key for the new user.
#
# Once set, permissions must be changed in NMS Config Assistant for the user.
#
# Example behavior of these new users
#
# user1 belongs to group OMAdev. This user is not given access to OMA because the group does not start with the user group prefix
#
# user2 belongs to group omauser. This user is given access to OMA and will have the permission defined by the default user key ad_key because the user_group is an exact match
#
# user3 belongs to group omauser-damage. This user is given access to OMA and will have the permission defined by the user key damage
mobile_ldap_user_group_prefix = omauser
mobile_ldap_user_default_new_user_key = ad_key
Further, in the MOBILE_NEW_USER_KEYS, the value for available should be 0 for the key "ad_key". This is the user_key that is assigned to new users through this automated process and should not be allowed to be assigned to users through any other process. Setting available = 0 will prevent this key from being assigned to users other than the new LDAP-authenticated users.
Mobile Applications Validation
Mobile Applications Validation is done in the Network Management System Configuration Assistant and is a separate validation scheme than Mobile User Validation. Mobile Application Validation consists of a application key built into the OMA application and it must match a configured model application key in the NMS Configuration Assistant Mobile Applications tab:
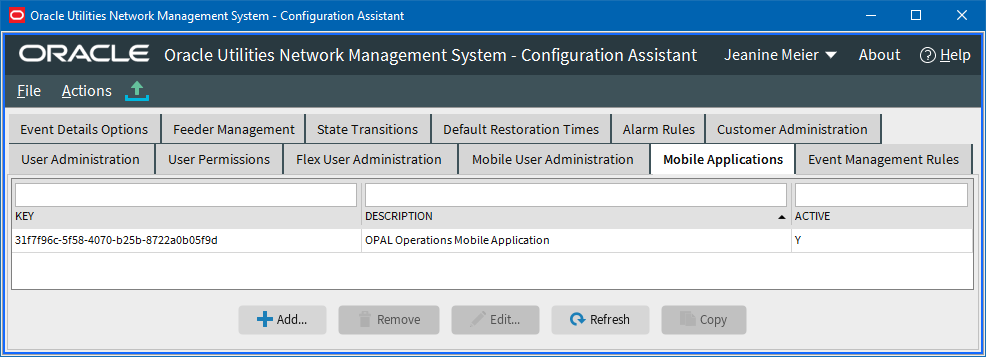
The Key must match the KEY in the OMA src/js/resources/config/loginSettings.js file’s self.appKey value.
Here is the default key:
self.appKey = '31f7f96c-5f58-4070-b25b-8722a0b05f9d';
You can have as many keys in the NMS Configuration Assistant Mobile Applications tab as you like; OMA is only built with one key, but different versions of OMA can use different keys (one for internal version of the app, another for extern version of the app).