1.1 API Security
This topic describes about the API Security.
The Oracle Banking Microservices Architecture application provides the API Layer (Service API Layer) which is used by external users to access the Oracle Banking Microservices Architecture functionality.
Access to this API layer is granted only via the following methods:
- OAuth with OAM (Oracle Access Manager)
- OAuth without OAM
- Oracle Banking Routing Hub
If the customer does not have OAM, they can use OAUTH without OAM or enterprise API Management layer should be implemented to protect the service API(s).
Register OAuth Clients with API Gateway
New Oath users can be registered with Oracle Banking Microservices Architecture using the below endpoint.
http://<hostname>:<port>/api-gateway/createOauthUsers- Header: appId: SECSRV001
- Header: Content-Type: application/json
- Header: userId: <USERID>
- Header: Authorization: Bearer <<JWT Access Token>>
{
"UserList": [
{
"clientId": "<< clientId >>",
"clientSecret": "<< clientSecret >>",
"validity": "<< Validity in seconds >>"
},
{
"clientId": "<< clientId >>",
"clientSecret": "<< clientSecret >>",
"validity": "<< Validity in seconds >>"
}
]
}Modify Token Expiry of Registered OAuth Client
Token expiry time can be updated using the below endpoint:
http://<hostname>:<port>/api-gateway/modifyvalidity- Header: appId: SECSRV001
- Header: Content-Type: application/json
- Header: userId: <USERID>
- Header: Authorization: Bearer <<JWT Access Token>>
{"client_id":"<< clientId >>","validity":"<< Validity in seconds >>"}API Security with OAuth
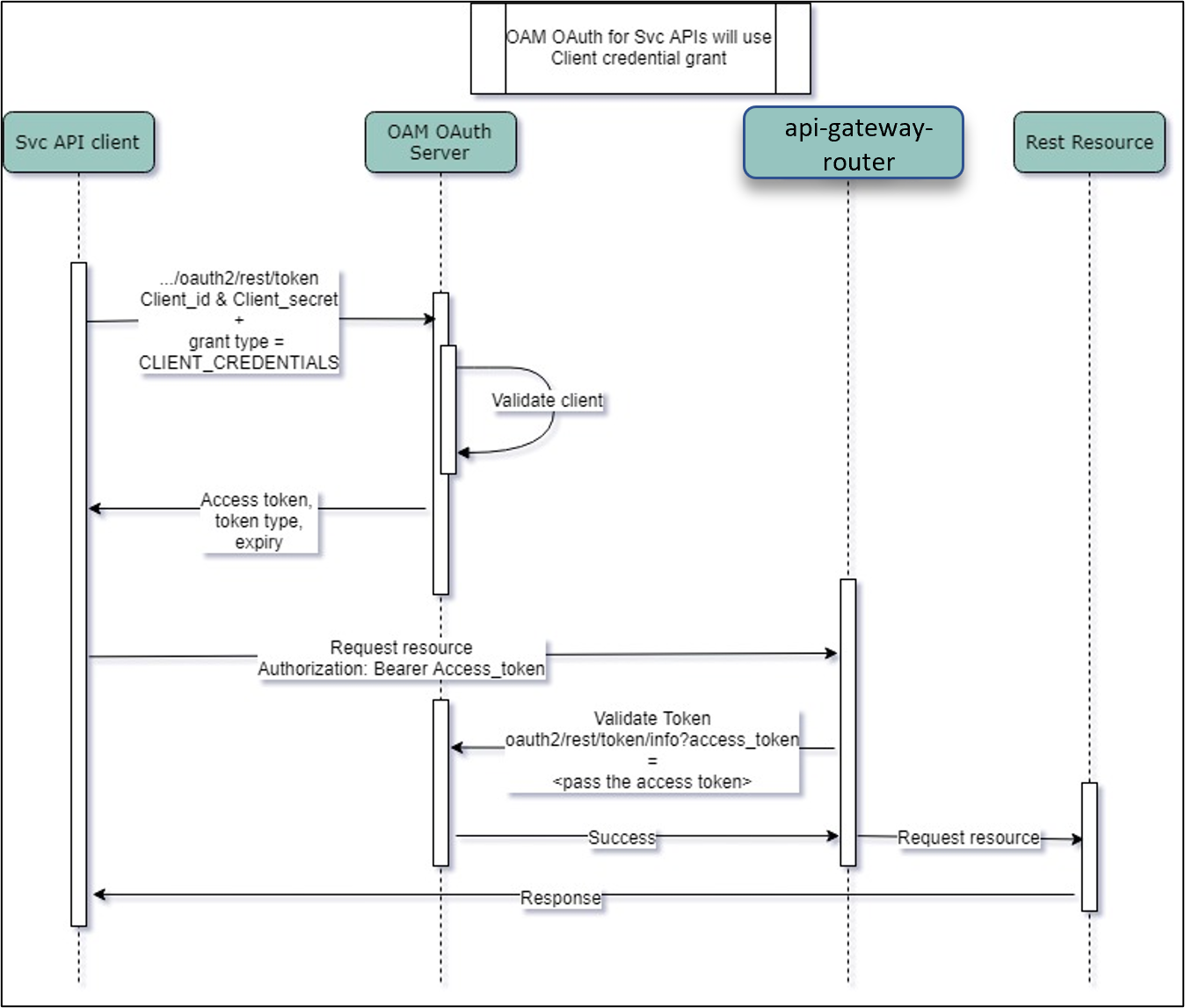
Oauth with OAM
The flow is explained below.
- API clients pass the client ID & client secret and grant type
as CLIENT CREDENTIALS. To get the access token, use the endpoint
/oauth2/rest/token. - API clients passes the access token in the authorization header as bearer token in their subsequent calls to access the Service API's.
- Plato-Apigateway-router calls API Gateway validates the client access token on OAM Authorization server.
- If valid, it passes the request onto the Svc API's and gets the response.
- The client can refresh to get a new token before the current token expires. If the token expires, they can pass the client ID and client secret to get a new token.
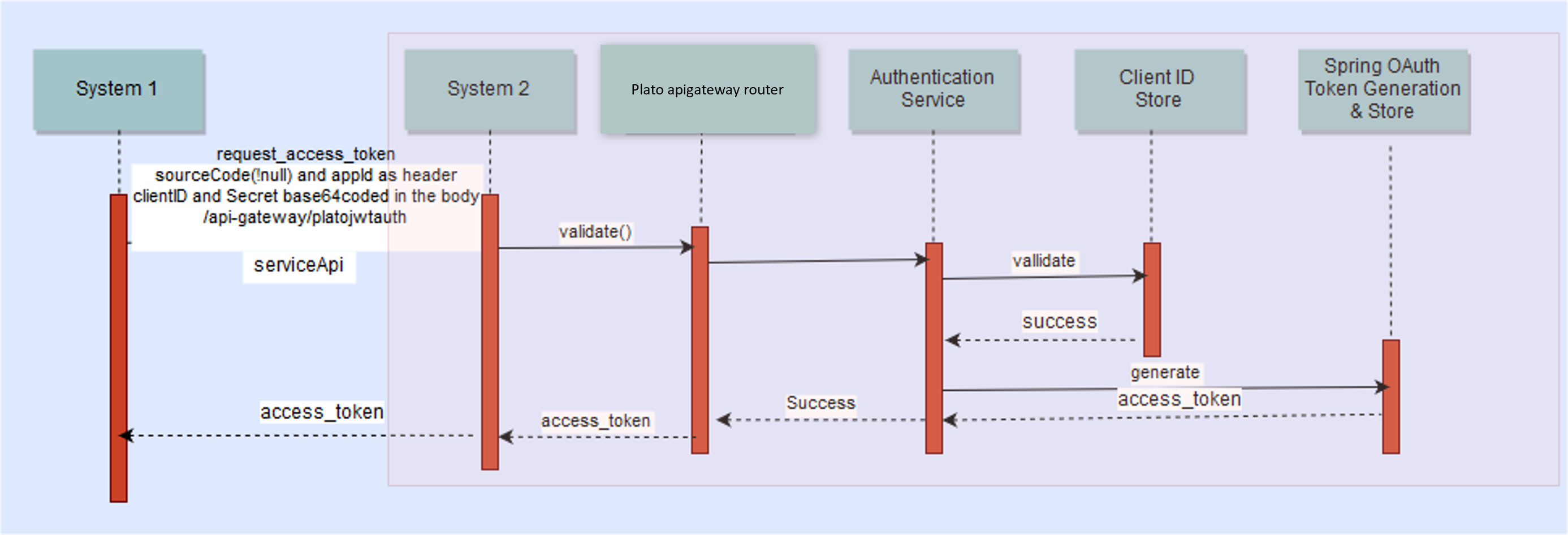
OAuth without OAM
The flow for token generation is depicted below:
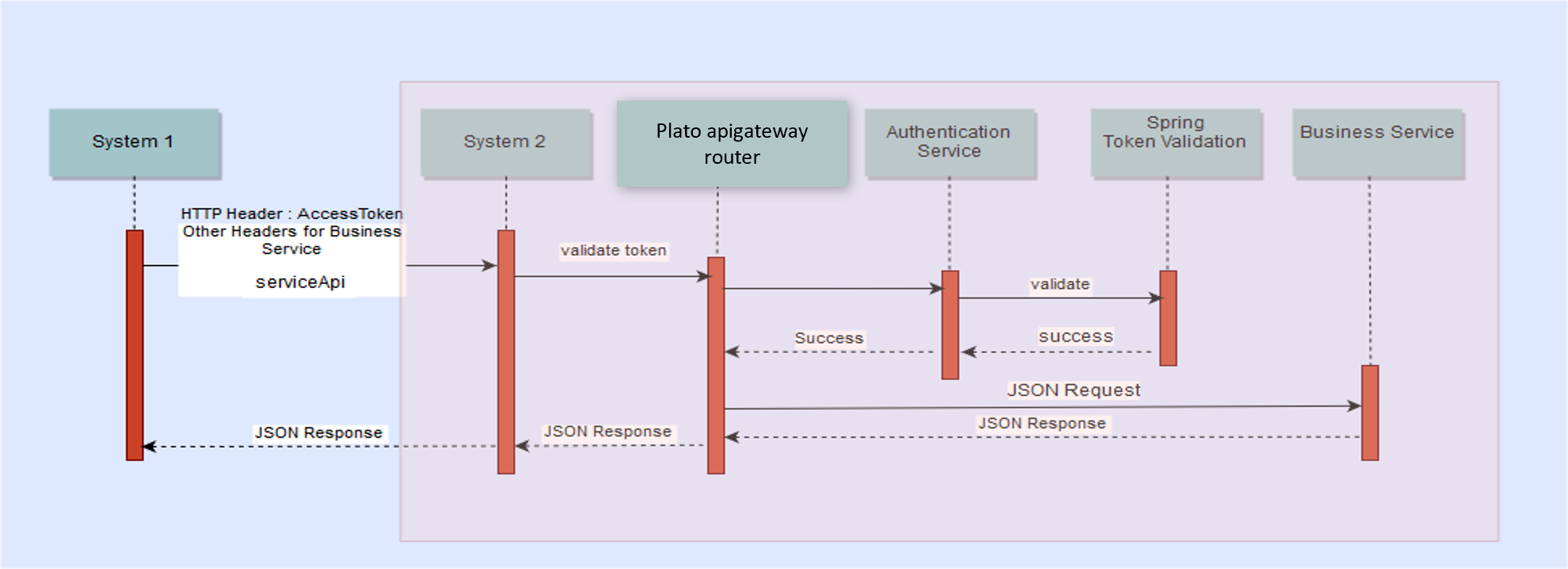
The flow for accessing svc is depicted below:
Figure 1-3 OAuth without OAM - Accessing svc flow
- API clients passes the client id & client secret in the body and
other required headers. To get the access token, use the endpoint.
http://<<hostname>>:<<port>>/api-gateway/platojwtauth/. - API clients passes the access token in the authorization header as bearer token in their subsequent calls to access the Service API's.
- Plato-apigateway-router calls Plato-api-gateway for validation before is routed to service.
- API Gateway validates the client access token on Authorization server.
- If valid, it passes the request on to the Svc API's and gets the response.
- The client can choose to get a new token (refresh) before the expiry of the current token. In case the token expires, they will pass the client Id and client secret to get a new token.
- Also, an additional facility of increasing the token is provided.
Access APIs through Oracle Banking Routing Hub
If the external services (services in bank or consulting) need to access APIs in Oracle Banking Microservices Architecture modules, the services will first have to generate an access token using Oracle Banking Routing Hub endpoints and then use the token to authorize themselves to access the endpoints.
Refer to Authentication section under Implementation topic in Routing Hub Configuration User Guide for the further details.
Parent topic: Securing API Services